Table of Contents
ToggleWhy Is Data Privacy a chief concern to business in the UAE in 2025?
Businesses focus on data privacy particularly to avoid costly breaches and loss of trust. The digital economy of the UAE is growing rapidly, and sensitive data must be protected as cyber threats are evolving more. Moreover, when a business build secure access, they are free from legal penalties and, eventually build trust and loyalty of their stakeholders.
What trends are transforming data privacy in 2025?
Data protection is now a major objective that many growing businesses take seriously. With evolving global privacy regulations, rising consumer expectations, and shady hacking practices, businesses are forced to invest in a more proactive security approach. Here is the checklist of data security and privacy trends that businesses must know in 2025.
Equipping before the breach
Unethical breach sources are growing more efficient and are competing on par with the technological evolution. That’s why being cautious early to a data breach is the right way to defend. So, businesses should be prepared for the worst with clear and tested strategies to handle breaches.
When expected breaches are handled responsibly with simulated attack scenarios, businesses are perfectly prepared to face such situations. Such preparedness will help the professionals detect the risks earlier and defend against them so that the damages and downtimes are avoided.
Consent focused
Earlier it was the generic “Accept all cookies” icon in use, and it was effected to change when the users were aware of their data safety. Now the user end expectation is clarity and transparency. Responding to the consumer need and redesigning the consent standards puts users’ requirement in the forefront.
Providing the customers with privacy dashboards, real-time preference centers for custom choices, and just-in-time consent prompts make it comprehendible for users on what they are giving consent for. Focusing on privacy, now businesses build purpose-specific consent with simple language. At the same time unticking permission is also made easy.
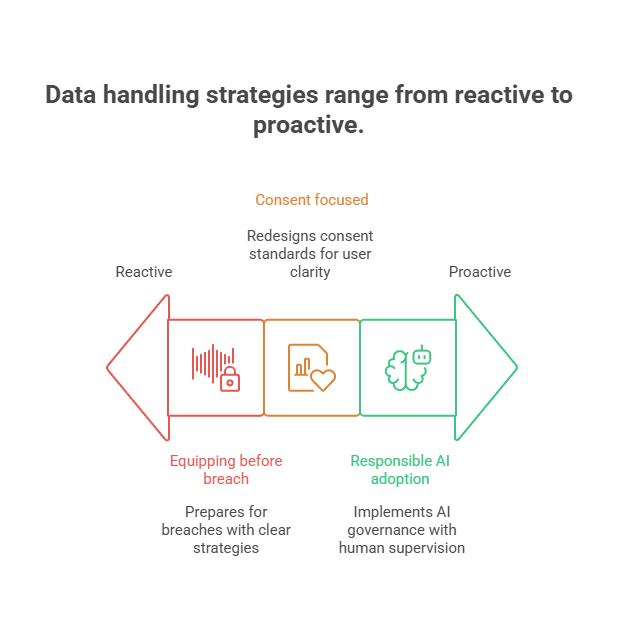
Responsible AI Adoption
AI assistance is incorporated in many business operations from customer support to fraud detection. However, only the accountable use of AI systems makes the operations fair.
Businesses now implement AI governance policies to monitor the responsible use of regular audits to detect bias. Now, AI is unavoidable, however human supervision takes lead in decision-making in most businesses. This is especially in sensitive areas like finance, hiring, or healthcare.
Zero Trust security Standard
Previously the security approach was a one time model and now it operates on the “zero trust” approach and it works on the objective- “verify always”.
With this zero trust policy the access is continuously verified across devices and applications. Most operations are adopting endpoint monitoring, micro-segmentation, and dynamic access controls to check if every interaction is authenticated in real-time.
Work Network Guardrails
Traditional office structures are migrating to remote and hybrid working, resulting in a need to protect sensitive data. By implementing secure remote access solutions, endpoint monitoring, and real-time activities can be tracked.
Employees working remotely should be provided security training to help them recognize phishing, and other device-level threats.
Also Read : Cybersecurity and Data Privacy Regulations: Understanding the Connection
Making use of Privacy-Enhancing Technologies
Privacy-enhancing tools and suits were reserved only for top enterprises with high budget. Now PETs are accessible for small and medium sized enterprises. These tools allow businesses to handle and use data without privacy breaches.
With differential privacy techniques, it is possible to mask individual identities within datasets. Also while dealing with encrypted data operation, homomorphic encryption allows it to work without decrypting it. In addition, to train AI models and learn across decentralized data sources, Federated learning technology is used.
Strong Global Privacy Regulations
Trade and business operations are expanding across different horizons of the globe and there are rising challenges. So to smoothen the processes there are updates enabled in the compliances.
Some of the compliance updates include: Privacy frameworks similar to GDPR that expands around the world, cross border data transfer regulations and children’s data protection. The compliance should include sector-specific regulations, and aggressive enforcement with penalties for violators.
Don’t ignore third-party risks
While dealing with supply chains a business’s sensitive data is circulated amongst different partners and the weakness in a single third party dealer can add risk. So, it’s essential to build a stronger fort.
The best practices to follow are adopting vendor risk management platforms to track third-party compliance in real time. This works on continuous monitoring, which is ongoing, automated, and audit-ready. AI is also integrated to help flag suspicious patterns across vendor interactions to spot the risks before they escalate.
Also Read : Ensuring Data Privacy Compliance: Essential Steps for Your Business
Cloud-Native Architecture
Switching to cloud-native architecture is a scalable option and currently it demands few considerations to abide with. Microservices, containerization, and serverless infrastructure implementations come with improved compliance.
Security is integrated during the development lifecycle through DevSecOps, so that vulnerabilities are caught early. Also to improve the vendor flexibility and improved resilience, multi-cloud strategies are devised.
All-in-one approach
The fragmented and segment-wise approach was proving to be risky as many components failed to pass through the compliance check. So, SMEs are making use of platform-first solutions that centralize security, compliance, and privacy controls.
With this real-time threat monitoring, automated audits, customizable compliance workflows, and cross-system integration are followed. Some even use built-in AI to detect anomalies and alarm the risks proactively.
Handling the evolving data privacy landscape in Dubai can be overwhelming when the country is adopting technologies largely in recent times. The risks can be higher especially with AI integration, expanding compliance responsibilities, and stricter regulations globally.
At Wattlecorp, we help businesses automate with secure access following regulations like consent management, impact assessments, and data mapping. Our data privacy consultants perform strict compliance checks to verify if it’s region specific while also screening the data privacy in your AI/ML enabled systems.
Data privacy FAQs
1. Is there a data privacy law in the UAE?
Yes, it is established under Federal Decree-Law No. 45 of 2021 and was followed from January 2, 2022. This data privacy regulation of the UAE is also known as the Personal Data Protection Law (PDPL). As per this law, personal data and privacy in the UAE digital sources are secure.
2. Is GDPR applicable to UAE?
UAE’s data safety digital practices completely aligns to Federal Decree-Law No. 45 of 2021. However, if the company operating from Dubai is connected with the European market, then it must compliant to the GDPR standard.
3. What is the open data law in UAE?
It is a policy that allows public access to government economic data without restrictions. This means the law permits individuals and institutions the freedom to use, reuse, and share the data freely. The Ministry of Economy of the UAE government supports this by offering open access to updated economic data through its website.
4. What is the confidentiality law in UAE?
According to Article 379 of the UAE Penal Code, it is a criminal offense to use third party information without its consent, or for its own or benefit of others. This is the case where the particular person who gained information was the one who was exercising a profession, position, craft, or art that involves the relevant data.








