Prevention is better than remediation. However, we are living in a technological realm where everything is changing in a blink of an eye. Be it the gadgets and applications we use daily or being used by huge companies.
However, there is a warning light, which often everyone forgets to look upon – the disruptive evolution of vulnerabilities.
In the cat-and-mouse game of our team against a single vulnerability that brings catastrophes to your business, staying not just one step, but two steps ahead of the bad actors is inevitable.
Penetration testing aka pen-testing is an approach to proactive security, which means finding the vulnerabilities in your application before the bad actor does, simulating how a real hacker does in real conditions. Penetration testing helps to verify the occurrence of a vulnerability found in the vulnerability assessment, which would cause cyber incidents otherwise.
Apart from a normal vulnerability assessment, a penetration test is more of an intrusive methodology, which might require scheduling prior and informing the employees regarding the same.
Also, there exist multiple classifications of penetration testing based on the technology and assets about to undergo the test. Understanding them helps to choose the best based on your business requirements, which we are about to look into with this blog.
Table of Contents
Toggle- Different Types of Penetration Testing
- 1. Web application Penetration testing
- 2. Wireless network penetration Testing
- 3. Mobile application penetration testing
- 4. Social engineering penetration testing
- 5. Cloud infrastructure penetration testing
- How a penetration test is conducted?
- Why does conducting penetration testing matter?
Different Types of Penetration Testing
Conducting penetration testing varies primarily based on the scope of the project and the expected result of the test. Following are the main three penetration testing techniques:
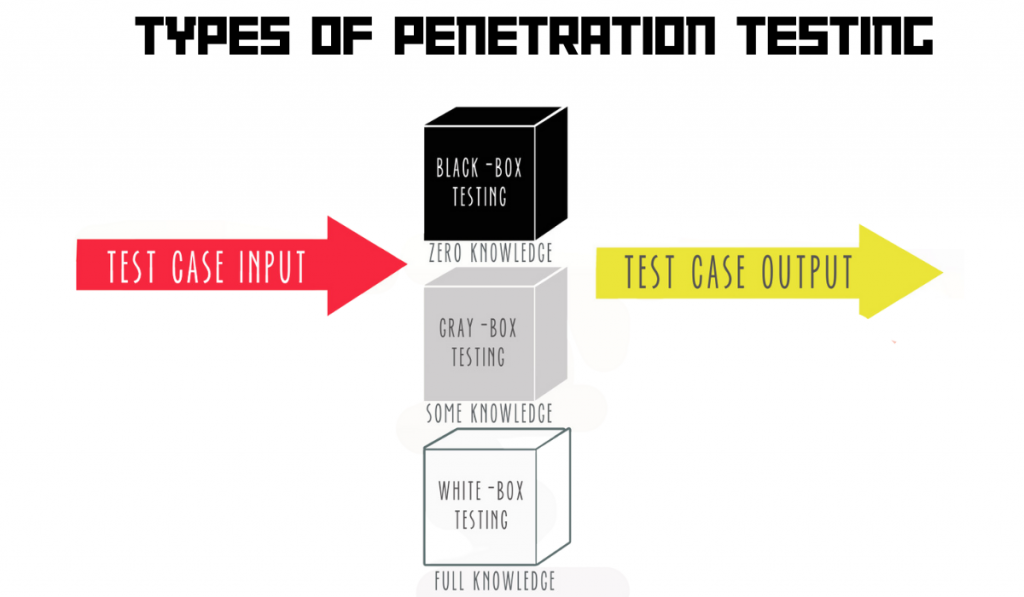
White box penetration testing
This is a penetration testing technique, in which the tester is given full information regarding the organization, network, and security systems. And due to the same reason, while considering the rest of the following, these provide more of a thorough test.
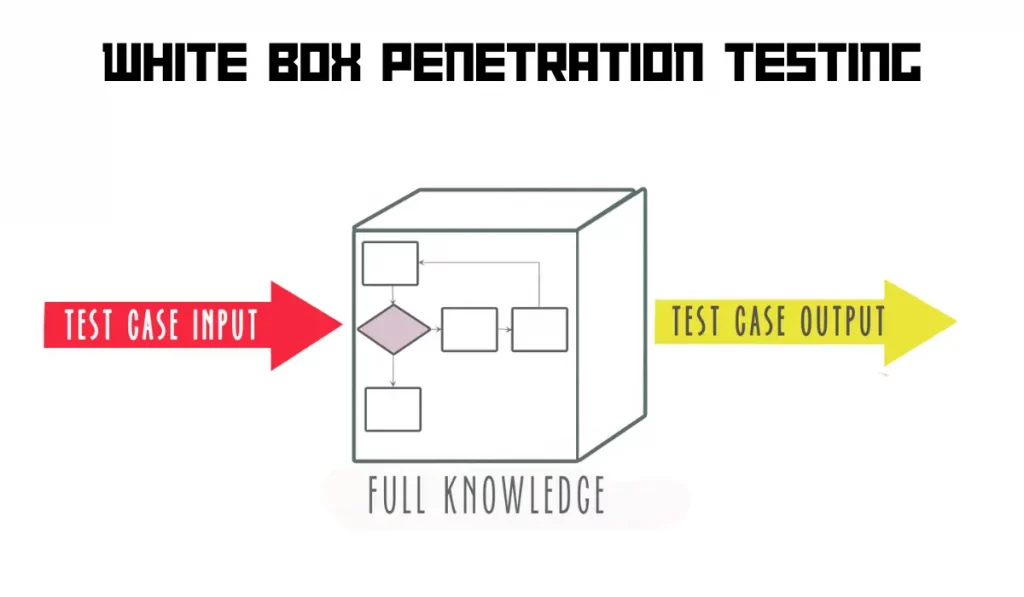
Since ample data is being provided this type of test might not mimic exactly how a bad actor would act. However, this helps to find how an insider attack would look like, due to the transparency of information to the pentester.
Black box Penetration testing
Black box testing can be considered the exact opposite of the white box one. The pentester would be given little to no prior information about the infrastructure or security measures of the asset they are assigned to scan. And, due to the same, this helps to find what an external attack would look like being attacked by a bad actor.
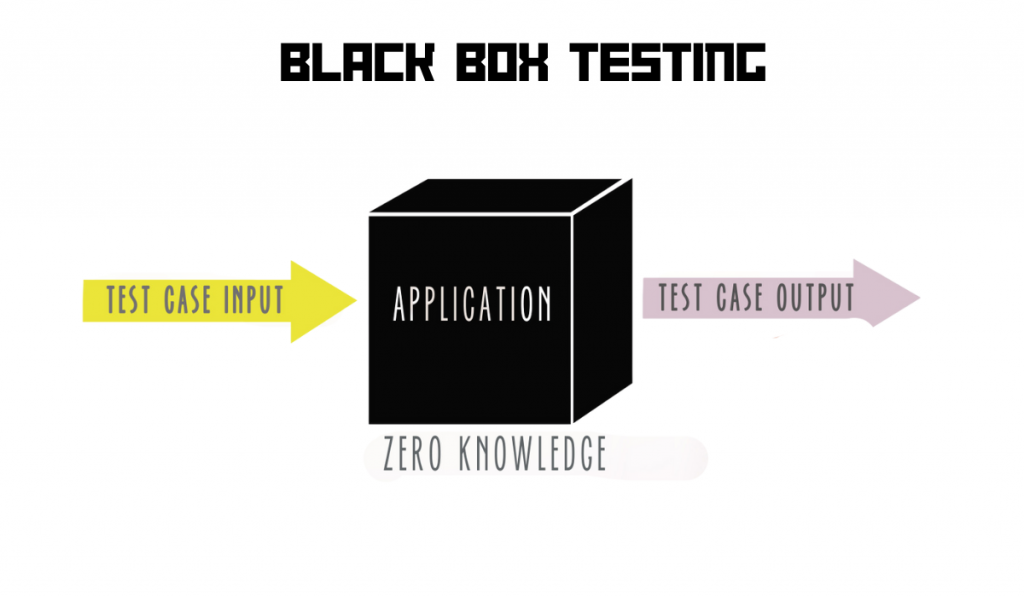
This requires lots of groundwork and the tester starts from outside the organizational network. Also, the black box testing approach is the most time-consuming one.
Grey box Penetration testing
As the name symbolizes, gray box testing is a combination of black box and white box testing methods. The pentester will be provided with partial information about the organization, greater than in the black box approach and less than in the white box approach.
Usually, this is conducted to find the vulnerabilities in the public-facing application with a private backend server. Similar to the definition of the gray box testing approach, the time required for completion is also in between.
Penetration testing does not always focus on an entire network or applications. In most cases, penetration testing will be conducted on technologies classified based on their nature. This helps to have a sharper focus on hunting the vulnerabilities and utilizing resources (both time and money) effectively and efficiently.
Following are a few of the most common penetration testing methodologies based on the technology:
1. Web application Penetration testing
Web application vulnerabilities have the potential to slip confidential data which could help attackers in the information-gathering phase of an attack or provide them backend access to a particular application.
Also, the multitude of browsers, plugins, and extensions in the web app alters the time complexity when conducting a pen test. SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF) are a few of the vulnerabilities found in the web application. Our services like Web Application Penetration Testing for SaaS Platforms India helps to address the unique security challenges effectively.
2. Wireless network penetration Testing
Wireless access points have become a common technology in our daily lives. Be it office space or house, Wi-Fi has made accessing the internet using electronic gadgets much more convenient.
Wireless network penetration testing technique helps accurately evaluate a network’s susceptibility to infiltration. Packet sniffing, de-authentication attacks, and rogue access points are commonly used to intercept and hijack wireless sessions to gain access to the organization’s network.
3. Mobile application penetration testing
Mobile app penetration testing is a comprehensive evaluation procedure that involves actively investigating and reviewing a mobile application for flaws and vulnerabilities.
Insecure data storage, insecure communication, weak authentication, and authorization, code code-related vulnerabilities such as buffer overflows, SQL injection, and other code execution vulnerabilities are mostly found vulnerabilities in a mobile application.
Conducting mobile app pentest assists developers in identifying potential vulnerabilities prior to attackers exploiting them, to improve the security of mobile apps by recognizing and mitigating them the earliest.
4. Social engineering penetration testing
However hard you secure your organization, people are the most insecure element.
Social engineering is a tactic used by attackers to fool employees into providing confidential information or access to a company.
The human vulnerabilities are commonly leveraged through forms of a phishing email, vishing (voice phishing attack), or by a human convincing or pretending to be someone else.
Providing proper training strengthens the IT infrastructure and the expertise of every employee in your organization. Social engineering tests are often conducted via email or over the phone.
5. Cloud infrastructure penetration testing
Cloud infrastructures are said to be more secure than on-premise IT environments, and not impenetrable. Cloud cyberattacks once take place have an immense potential to wreak havoc on business.
It should be a top priority for corporations in order to avoid costly breaches and achieve compliance. By doing cloud penetration testing, you are able to address and rectify critical security flaws related to the cloud before they become a bad hacker’s advantage.
How a penetration test is conducted?
The best way to stay ahead of the bad actors is to put your feet in their own shoes.
A pentester is someone who does the same for you, professionally and ethically. Hence they are called ethical hackers.
The entire process starts with a ping (initial communication) from the business owner or the one from corresponding departments within the organization. The scope will be set with defined guidelines, limitations, and a feasible timeframe for completing the penetration test. Also, the legal agreements shall be signed by both parties in common terms of the expected outcomes, risks, and the resources required.
Vulnerability assessment (VA) will be conducted as the initial step which helps to identify the loopholes in the application or network. It can be due to anything ranging from misconfiguration of the firewall to bugs in source code.
Once the loopholes are found, the pentester tries to escalate the vulnerability to find more towards gaining higher privileged accounts and access to the maximum critical system possible. This helps to understand the worst-case scenario.
Apart from the above-mentioned conventional manner, often pen-testers use other techniques such as dropping infected USBs in the hallways, which an employee plugs into any of the computers leading to access to the pentester, as it would to a bad actor in a real incident.
The aim of the pentester would be nothing less than to gain access to the most critical asset in the infrastructure, call it physical or electronic. Once the test is done, a comprehensive report containing all the necessary information about the penetration test, which includes the vulnerabilities found, their impact, occurrences, insights on fixing them effectively, and the steps of the test will be shared with the respective team.
Also, it is recommended that most conduct penetration tests periodically to find and fix even the latest vulnerabilities. Usually, the majority of the business conducts them at least once a year or after making security changes in their application.
Why does conducting penetration testing matter?
The dirty little secret is that the majority of cyberattacks are the result of poor cyber hygiene. The legacy security architecture that looks fine on paper but does not prevent cyber attacks, weak access control, and inadequate security control implementation will result in a vast attack surface that no new flashy technology can fix. Simply said, “prevention is always better than cure” is a notion that must be applied in all parts of technology in order to give near-perfect services to the most essential asset, which is clients.
The penetration testing technique in India has the potential to detect system, network, and application vulnerabilities. An ethical hacker will conduct pen testing to simulate an attack in order to identify vulnerabilities that may be exploited Penetration testing is only one part of a larger network security strategy. It is often carried out over a certain length of time and is complemented by other types of scans and programs that help improve an organization’s overall security posture.
Regular vulnerability scanning can also be used in tandem with annual penetration testing to help ensure that businesses stay safe in the meantime. It may now be automated and conducted in the background of a network on a regular basis to help discover possible flaws that a bad actor could exploit to get access to a network. Vulnerabilities are most commonly discovered in outdated software, unpatched systems, and improperly configured networking equipment such as routers or switches.