Table of Contents
Toggle- Why Is Mobile Application Security Checklist Essential For Indian Businesses?
- What Is Mobile Application Security?
- Why do Indian Mobile App Users Need A Security Checklist?
- Complete Mobile Application Security Testing Checklist
- Securing Mobile App For Indian Users/Businesses with Expert Help from WattleCorp
- WattleCorp’s Mobile App Testing Services For Indian Businesses
- Why Choose Wattlecorp Mobile Application Testing Program For Indian Mobile Applications?
- Mobile Application Security Checklist FAQs
Why Is Mobile Application Security Checklist Essential For Indian Businesses?
Did you know that 85% of mobile apps have security and privacy issues that can damage reputation, cause customer dissatisfaction, and lead to disputes and fines?
India has been noted as one of the most targeted countries in the world with mobile malware attacks rising to 28% from a global perspective. This fact could be well ascertained by a fake app introduced by the name of ‘SBI REWARDZ.apk‘ that led to SMS, notification, contact list, and financial details harvesting – uploading them to Firebase. The incident was subsequently brought to notice by the Rajasthan Police in June 2025, warning the public about this malware‑laden fake app. How social media-distributed malware continues to threaten mobile users and businesses was significantly demonstrated.
The number of cyberattacks on mobile platforms has reached an all-time high in India, and we can’t ignore the risks. We all know at this time these mobile apps go far from being just tools.
They’re like a lifeline for businesses and also for us. But that comes with an equally alarming rise in cyber threats and without proper security.
That’s why we set up a complete mobile application security checklist. You can review this list to ensure that your app is one step ahead of threats. Whether you’re developing a new mobile app or maintaining an existing one, a mobile app security checklist is your first line of defense.
This blog will teach you there are no shortcuts to ensuring business mobile app security.
What Is Mobile Application Security?
Mobile application security is the measures and techniques used to protect mobile applications from all kinds of threats, vulnerabilities and inaccessibility. The entire system includes protecting the data, processes and users of a particular application from all attacks and violations.
From regular apps to enterprise software, security protocols are essential to maintaining trust and ensuring seamless operations. Mobile security is important in many ways:
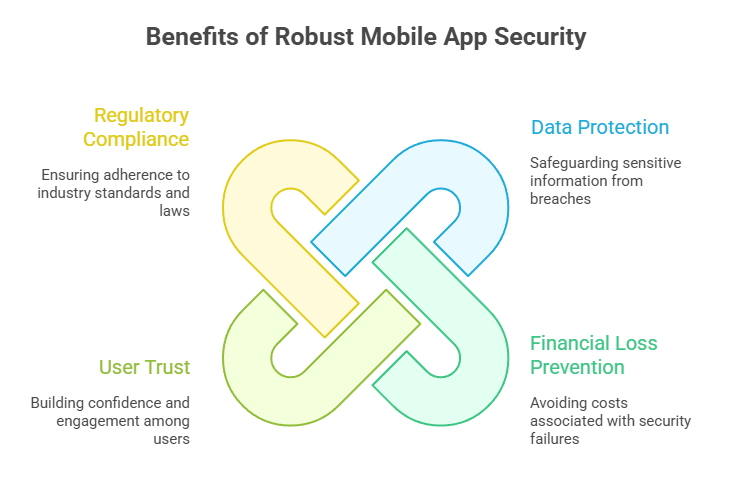
- Protects Sensitive Data: This helps protect sensitive information such as personal and business-critical data such as financial information, login credentials, and confidential information.
- Prevents Financial Loss: Some weak security measures in mobile apps can lead to damages such as fines, legal fees, and reputational damage.
- User Trust: All users need to have trust that helps them be more likely to engage with mobile apps that prioritize their security and privacy.
- Compliance with Regulations: Getting proper security measures to ensure compliance with industry standards like GDPR, HIPAA, or PCI DSS.
Why do Indian Mobile App Users Need A Security Checklist?
You know how much your personal information holds value for you. When you input your data, including your financial details, would you care to leave them astray? You wouldn’t, isn’t that right?
A security checklist in this scenario is essential to keep your identity and money safe. This checklist can effectively guide you to identify and fix potential security flaws when utilizing mobile apps. By preventing data breaches and malware through unauthorized access, your mobile application security checklist acts like a locker to safeguard your apps and critical personal information.
Also Read : Top 10 Mobile App Security Threats In 2025
The DPDP Act, 2023 plans on establishing the Data Protection Board of India to come into effect in the near future. The aim is to adjudicate user‑data breach complaints and impose penalties up to ₹250–₹500 crore for insufficient safeguards or breach notification lapses.
Complete Mobile Application Security Testing Checklist
Go through this mobile app security checklist guide to make sure your mobile app is safe from potential vulnerabilities
1. Secure Source Code
The source code forms the basis for the development of any mobile application and is usually based on open source, which facilitates rapid development and deployment. This gives hackers a chance to stab such software with malware. This source code contains organizations’ information like APIs, encryption keys, passwords and more. So make sure it is secure, or other malicious errors get your details.
- Conduct Static Application Security Testing (SAST) using tools, such as MobSF, SonarQube, and Veracode
- Perform Software Composition Analysis (SCA) to identify vulnerable libraries and dependencies
- Remove hardcoded sensitive information, including API keys, passwords, and cryptographic keys)
- Conduct regular peer reviews and manual code audits
The urgent advisory (CIVN-2025-0092 & CIVN-2025-0094) issued by CERT-In in May 2025 warned of high‑risk vulnerabilities in the 13, 14, and 15 versions of the Android operating systems and in iOS versions that are older than 18.3, i.e., 17.7.3. These when exploited can make way for remote code execution or denial‑of‑service attacks. Users were, therefore, and strongly urged to update their mobile OS and avoid unverified apps.
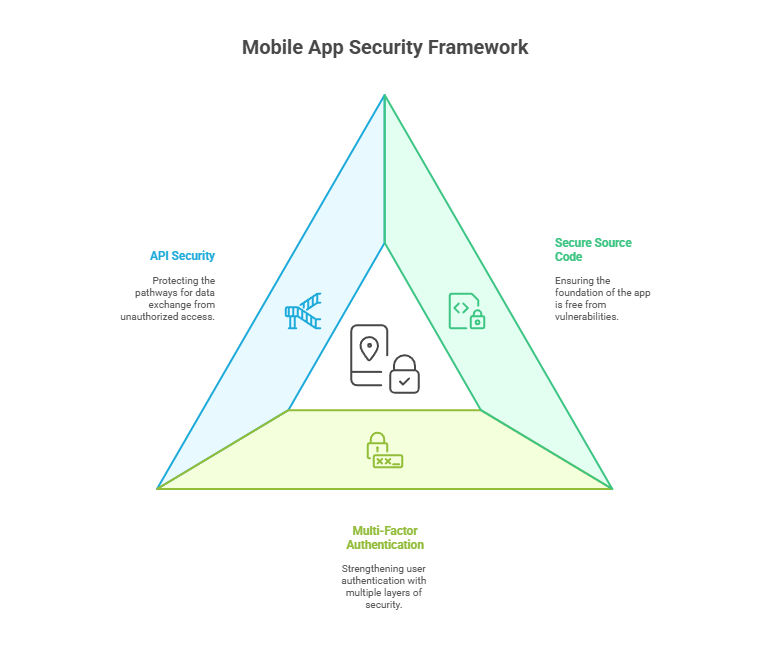
2. Implement Multi-Factor Authentication
Phone users don’t like the repeated authentication and checks on their devices. So this multi-factor authentication helps in strengthening the user authentication that implies that 2 or 3 steps are added to deploy protection. It comes with biometric verification, pins, calls, messages and other security questions.
- Enforce strong multi-factor authentication (MFA) for sensitive features (biometric, OTP)
- Implement secure session handling with expiration and logout functions
- Validate authorisation schemes thoroughly (RBAC, Principle of Least Privilege)
- Prevent insecure direct object references (IDOR)
3. API Security
APIs are another main way that acts as a path for attackers to enter. Also, you need high-quality secured APIs for improved mobile app security and don’t expose the data swapped. You can adapt an API security framework, like the REST security framework, and implement the Principle of Least Privilege (also known as PoLP) – users should only have access to the resources they need.
- Ensure API endpoints are secured using TLS 1.2/1.3 encryption
- Implement strict input validation to prevent injection attacks (SQL, XSS, and Command Injection)
- Enforce strong authentication mechanisms (JWT, OAuth 2.0, and API keys)
- Implement robust rate-limiting and anti-abuse measures
4. Penetration Testing
Pentesting or penetration testing can help set up regular penetration testing that identifies vulnerabilities before attackers exploit them. This will help scan the code for any suspects and take precautions to mend it. This mobile app penetration testing helps you in getting to know any activities that happen there.
- Conduct periodic comprehensive pentesting using manual & automated tools (MobSF, Burp Suite configured for mobile) with Frida, Drozer, and Objection for dynamic analysis
- Validate against OWASP Mobile Security Testing Guide (MSTG) checklist
- Follow OWASP Mobile Top 10 vulnerabilities for risk prioritization
With digital banking having revolutionized the financial ecosystem in India, threats of frauds amid such conveniences can indeed skyrocket. With ransomware, phishing attacks, and identity theft being more common to target critical industries like banks, healthcare, oil and gas, etc., these strictly mandate tightening data protection laws, exploring evolving regulations, and highlighting critical vulnerabilities by identifying and fixing security flaws proactively.
5. Runtime Protection & Reverse Engineering (RASP)
RASP adds a dynamic layer of protection by detecting and mitigating threats in real time. This tool monitors a company’s application in real-time by analyzing both the context and behaviour in which it occurs. If RASP finds a security event, for example, a suspicious effort to roll or open a file without proper authorized access, it will try to stop it right off.
- Deploy Runtime Application Self-Protection (RASP) or advanced runtime protections (Guardsquare DexGuard, Arxan, Appdome)
- Use code obfuscation and anti-tampering measures
- Detects and responds to debugging, hooking, and memory tampering (Frida, Magisk, Xposed detection)
6. Implement HTTPS – SSL/TLS Security Layer
There lies a possible and significant attack with a not-so-secure network connection between a mobile application and the server. Securing mobile application communications with HTTPS using SSL/TLS is regarded as a foundational security practice. It helps ensure encryption and prevention of unauthorised interception and tampering of data transmission between the application and servers.
For you to secure your mobile application communications using SSL/TLS, you need to:
- Obtain and Install SSL/TLS Certificates. You should also ensure your server security certificates are from a trusted Certificate Authority (CA)
- Secure your connections by redirecting HTTP traffic to HTTPS
- Using proper validation mechanisms helps avoid fake or self-signed certificates
India’s Bharat NCX 2024—a 12‑day national cybersecurity exercise organized by NSCS and Rashtriya Raksha University is designed to boost cyber‑defense readiness across industries, including mobile threat simulations and critical infrastructure protection for Indian entities.
7. Data Storage & Encryption
If you are the one who stores your records locally, this will end up with an attacker gaining access to anything. Whether it is iOS or Android your local data storage implementation needs to be done based on thorough security considerations.
- Encrypt sensitive data using strong encryption standards (AES-256)
- Store encryption keys securely in platform-specific key stores (iOS Keychain, Android Keystore)
- Regularly verify and limit local storage of sensitive data
- Prevent sensitive data leakage via cache, logs, backups, or screenshots
The ICICI iMobile glitch affected 17,000 credit cards and the Telangana/Tamil Nadu police mobile app data leaks emphasized that even official apps have exposed locations, contacts, biometric data, etc.
8. Input & Output Validation
- Validate all user and external input for length, type, format, and encoding
- Apply proper escaping/encoding methods to protect against injection attacks
- Perform validation server-side, not solely client-side
9. Session Management
- Implement secure and unpredictable session tokens
- Invalidate sessions on logout, after idle timeout, or suspicious activities
- Protect session identifiers with secure flags (HttpOnly, Secure)
10. Error Handling & Logging
- Ensure error messages don’t disclose sensitive information
- Implement secure logging practices: sanitize logs, avoid logging sensitive data
- Store logs securely and maintain retention policies
Also Read : Common Web Application Vulnerabilities Putting Your Business At Risk In 2025
11. Platform-Specific Security Controls
Android
- Implement runtime protections against rooting and emulator detection (e.g., SafetyNet API)
- Use Android Keystore for secure key management
- Validate Android manifest configurations (exported components, permissions)
IOS
- Implement Jailbreak detection
- Leverage iOS-specific protections (App Transport Security, secure entitlement usage)
- Properly configure app sandbox and entitlements (specific permissions that allow an app to perform certain operations – access certain resources otherwise restricted by the sandbox environment)
This concludes the mobile application security assessment checklist you can use in your mobile testing. It’s also possible to hire a professional team to do that so you can get everything done in a better way we’ll discuss in the next section.
Securing Mobile App For Indian Users/Businesses with Expert Help from WattleCorp
When it comes to safeguarding Indian mobile applications like yours, getting comprehensive security testing is the best idea.
WattleCorp has an experienced team that specialises in mobile application security testing to ensure your app is protected against any threats. The team sets up deep testing mobile apps to know their weaknesses, fix them, and strengthen their security. The team supports through online, email, phone and also on Jira, Teams and Slack.
The WattleCorp team mobile app testing comes with advantages that are:
- Analyse your security posture by simulating attacks
- Enhance the speed and quality of secure code development by developers
- Streamline the security testing process without compromising quality
- Provide highly secure applications and reduce compliance costs
- Prevent Security testing from delaying application release
- Remove Complexities with vulnerability management and upgrades
- Reduce time and effort invested in finding and fixing security vulnerabilities
WattleCorp’s Mobile App Testing Services For Indian Businesses
Wattlecorp utilises the following tools to conduct mobile app testing in India:
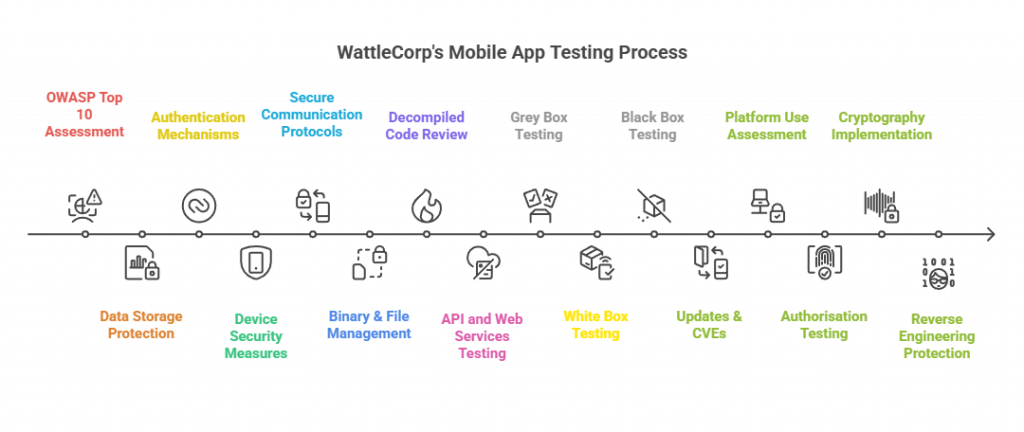
- OWASP Top 10: We assess, identify, and mitigate the most critical vulnerabilities in your mobile app by running the OWASP Top 10 list as a benchmark.
- Data Storage: We enhance your app’s data storage practice efficiency by protecting sensitive information from unauthorised access.
- Authentication: Our security experts execute robust authentication mechanisms to safeguard user identities, preventing unauthorised access in the event.
- Device Security: We protect your app against device-specific threats, ensuring it remains secure on various platforms and devices.
- Secure Communication: We implement secure communication protocols to protect data during transmission, preventing interception or tampering.
- Binary & File Management: We assess the security of your app’s binaries and file handling processes, ensuring safe storage and transfer.
- Decompiled Code Review: Our team analyzes the reconstructed code extracted from your app’s APK or IPA file to detect vulnerabilities, ensuring robust security before deployment.
- API and Web Services: We test your app’s APIs and web services for potential security flaws to prevent unauthorised access and data breaches.
- Grey Box Test: We simulate attacks with partial knowledge of the system to identify vulnerabilities that may be exploited.
- White Box Test: We conduct an in-depth security evaluation with full access to the source code to uncover hidden vulnerabilities.
- Black Box Test: We simulate attacks with no prior knowledge of the system to mimic external threat actor behaviour and test defences.
- Updates & CVEs: We ensure your app stays protected by regularly updating it with the latest patches and addressing any known vulnerabilities (CVEs).
- Platform Use: We assess the security risks associated with the platforms your app is designed for, ensuring compatibility and protection.
- Authorisation Testing: We thoroughly test the application’s access controls to verify that only authorised users can access sensitive resources and perform restricted actions.
- Cryptography: We secure your app’s data with industry-standard encryption techniques, protecting sensitive information from unauthorised access.
- Reverse Engineering and Decompiling: We analyse and protect your app from reverse engineering and decompiling attempts, ensuring your intellectual property remains secure.
Why Choose Wattlecorp Mobile Application Testing Program For Indian Mobile Applications?
Choosing Wattlecorp’s Mobile Application Testing Program for Indian mobile applications offers the following advantages, such as:
- Build secure apps while cutting down on compliance costs
- Catch business and logic issues that automated tests might miss
- Keep sensitive customer data safe from leaks
- Simplify vulnerability management and patching
- Find and fix security issues faster
- Wattlecorp expert developers deliver secure code efficiently
- Track your app’s security progress with easy-to-use dashboards
Whether you’re looking to identify vulnerabilities, assess risks, or implement a security framework, we offer customized solutions tailored to your unique needs. Know all our mobile application security testing services to learn more about how we can help secure your app from start to finish.
Keeping your mobile app secure isn’t just important – it’s rather crucial, especially if you are using Indian-based mobile applications.
This checklist takes you through the vital steps for protecting your app from hackers and preventing data leaks.
If you’re not sure about how to implement it, you can call us and our VAPT professionals will do it for you. We’ll handle the testing and security so you can focus on what you do best in building your app.
So, how secure are your mobile applications as an Indian business entity? The mobile application security testing service that our Wattlecorp team in India offers ensures maximum protection for your apps, business, and data – making them out of reach for potential exploitation from the hackers.
It will not hurt you if you consider checking your defenses for your applications – Android or IOS by running them through our free checklist.
Don’t sit there and wait for the breaches to occur. Take Action To Enhance Your Apps’ Protection. Get a pentest today!
Mobile Application Security Checklist FAQs
1.Why is mobile app security checklist crucial for Indian businesses and users?
Mobile app security will protect sensitive data like personal and payment details, build user trust, and prevent cybercrimes such as identity theft and fraudsters.
2.What are the essential security testing methodologies for mobile apps?
The essential security testing methodologies for mobile applications in India include:
• Penetration testing
• Static code analysis
• RASP API security
• HTTPS/SSL
• MFA (Multi-factor Authentication)
3.How can I address the security challenges of mobile payments and financial transactions?
If you’re operating your fintech enterprise in India, you should:
• Ensure strong encryption for your sensitive data
• Implement secure authentication methods, i.e., MFA (multi-factor authentication)
• Perform regular security assessments and penetration tests
• Secure APIs and network communications
• Use transaction monitoring for fraud detection
• Continuously update your app for prompt vulnerability patching