Cybersecurity threats and challenges notoriously affect small as well as large businesses. To outsmart cybercriminals, organizations need to employ ethical hacking strategies. Penetration testing is orchestrated by mimicking security attacks on a system to analyze the response and identify the vulnerabilities.
The different penetration testing methodologies and approaches used in pen testing can significantly impact the outcome. Choosing a penetration testing methodology is of prime importance as it identifies potential security weaknesses, guides the organization against evolving threats, and ensures the pen testing is organized and accurate.
In this article, we will discuss the best penetration testing methodologies and which are suitable for your business.
Table of Contents
Toggle- What Is Penetration Testing?
- 1.Open Web Security Project (OWASP)
- 2. Open-Source Security Testing Methodology Manual (OSSTMM)
- 3.Penetration Testing Execution Standard (PTES)
- 4. National Institute of Standards and Technology (NIST)
- Types Of Penetration Testing
- 2. White box Penetration Testing
- 3. Grey Box Penetration Testing
- How Do You Choose a Penetration Testing Methodology for Your Business?
- Frequently Asked Questions (FAQs)
What Is Penetration Testing?
Penetration testing is cyber security testing to identify potential vulnerabilities in a system and mitigate their impact. Penetration testing methodology helps to understand how your system will respond to a cyber attack, build up ethical hacking strategies, and meet industry-specific compliance regulations, thus providing complete coverage of critical cybersecurity aspects. Pen tests can be carried out manually or via automated tools through a penetration testing methodology.
1.Open Web Security Project (OWASP)

Advantages
The Open Web Application Security Project is considered a golden standard for web application pen-testing. It is an open-source and non-profit organization that aims to improve the security of web applications and is preferred by organizations that deal with sensitive data, including the financial sector.
- Produces learning guides, application tools, and standards that improve the security of applications.
- Organizations can get professional advice and support from OWASP.
- Provides an industry standard of code review guides and frameworks
- Designed for WebApp
Business security use cases
OWASP’s Top 10 list, which was published in 2003 and is updated every 3 years, elaborates on the major vulnerabilities that can severely threaten the security of web applications. Testing framework, reposting, and testing methodology are the 3 sections of the OWASP Testing Guide.
- Used for web application penetration testing, mobile application penetration testing, API penetration testing, and IoT penetration testing.
- As a security test for preventing business logic vulnerabilities.
2. Open-Source Security Testing Methodology Manual (OSSTMM)
The Open-Source Security Testing Methodology Manual is a methodology developed with peer review by the Institute for Security and Open Methodologies (ISECOM) for performing quantitative, transparent pen tests and metrics.

Advantages
- Provide physical security guidance
- Workable metrics and measurement.
Business security use cases
Suitable for organizations that require detailed finding reports for post-test activity and most optional if your team is external/third-party based.
- With the vast network of interconnected systems, financial firms can opt for OSSTMM for comprehensive auditing.
- Firms in the Healthcare sector often use OSSTMM to protect sensitive patient data.
3.Penetration Testing Execution Standard (PTES)
The Penetration Testing Execution Standard is a penetration testing method that guides organizations throughout the testing phase, including the pre-engagement stage. It consists of seven sections, covering all the details of pen testing.

Open Web Application Security Project is considered a golden standard for web application pentest. It is an open-source and non-profit organization that aims to improve the security of web applications—preferred by organizations that deal with sensitive data including the financial sector.
Advantages
- Produces learning guides, application tools, and standards that improve the security of applications.
- Organizations can get professional advice and support from OWASP.
- Provides an industry standard of code review guides and frameworks
- Designed for WebApp
Business security use cases
OWASP’s Top 10 list, which was published in 2003 and is updated every 3 years, elaborates on the major vulnerabilities that can severely threaten the security of web applications. Testing framework, reposting, and testing methodology are the 3 sections of the OWASP Testing Guide.
- Used for web application penetration testing, mobile application penetration testing, API penetration testing, and IoT penetration testing.
- As a security test for preventing business logic vulnerabilities.
4. National Institute of Standards and Technology (NIST)
National Institute of Standards and Technology is a cybersecurity framework that provides guidelines to help organizations strengthen their cybersecurity. It is a federal agency within the United States Department of Commerce that includes standards like Special Publication 800-53A Rev. 5.
Advantages
- It provides a common language and systematic methodology for managing cybersecurity risk.
- Will guide through risk management activities within various levels of an organization
- To assess the skill set of the testing team regarding their understanding of web apps, telecoms, networking, etc.
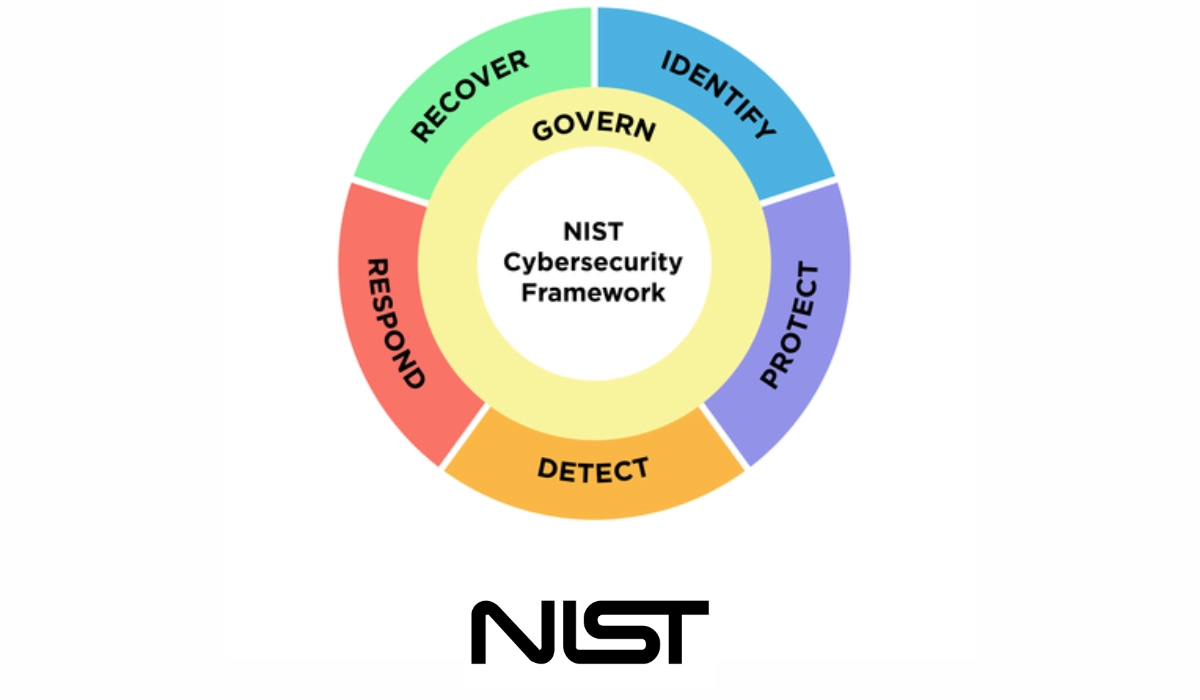
Business security use cases
Organizations when using NIST penetration testing should follow their pre-determined guideline. Suitable for large businesses.
- With the quantum resistance mathematical functions, NIST has been working to develop a post-quantum cryptography standard.
- Zero-trust architecture (ZTA) to protect the assets, and resources of a user within the network parameter.
Also Read : 7 Phases In Penetration Testing: Complete Process and Tools
Types Of Penetration Testing
1. Black Box Penetration Testing
In black box testing, the pentester is provided with little to no information about the system. From primary access to complete execution, the tester follows the steps of an unprivileged hacker that attributes to a real-world attack.
Since the tester does not have much information regarding the internal structure of the system, they will have to input a lot more work making it a costlier and time-consuming one.
Advantages
- Most useful to understand how a malicious actor with no knowledge of the internal structure can exploit or attack the system
- Demonstrates how a real-world external attack would look like
Business security use cases
- Identify vulnerabilities like CSRF, XSS, injection attacks, etc.
- Pentest the overall security of the system
2. White box Penetration Testing
In white box testing the tester is provided with all the information regarding the system and its network.
Since the testers are given full access to the system including access to network maps, documents, source code, and credentials, they help to stimulate targeted attacks on a system by using as many attack vectors as possible.
Advantages
- As the tester is fully aware of the internal structure of the system, it helps to save time and minimize the total cost.
- Expose the vulnerabilities that are often exploited by malicious actors and how this is carried out in real-time.
- With complete access to the system information white box testing can help you understand what an internal attack would look like
Business security use cases
- Penetration testing of the company’s network infrastructure and internal structure
- Stimulates the real-life attack on a specific system
3. Grey Box Penetration Testing
The tester is only provided with limited information about the system hence it is also referred to as translucent box testing. The partial information given to testers helps to understand the accessibility of a privileged user and the damage such privileged users can cause.
In Grey box testing When a real-world attacker probes into the targeted system, it gives knowledge similar to that of an insider.
Advantages
- Stimulates an insider attack as well as the data breach that occurs within the network perimeter.
- Since it is a combination of black box and white box testing, grey box testing has the perfect balance between efficiency and authenticity that a customer desires.
- Removes the time-consuming reconnaissance phase.
Business security use cases
- Usually carried out in public-facing websites or applications that have a private backend server, to identify vulnerabilities and remediate them.
- Detect vulnerabilities present in the early stage of a system and how much information an attacker can receive.
Also Read : Manual Vs Automated Penetration Testing-Finding the Right Balance for Your Business
How Do You Choose a Penetration Testing Methodology for Your Business?
There are numerous standardized testing methodologies in the industry but always opt for the one that aligns with your organizational goals. Choosing the right penetration testing methodology is crucial for the security of your system, to identify and address potential weaknesses. There are many factors to consider while selecting a pen testing methodology for your business:
- The methodology should provide end-to-end cybersecurity testing to identify and mitigate potential vulnerabilities.
- The methodology should align with your organizational needs
- Ensure that you agree with the budget and time allotted by a methodology.
- Thoroughly review their guidelines, instructions, and reports to ensure effective communication.
- Some methodologies are suitable for small-scale businesses like OWASP and some are good for small-scale as well as large scale including NIST, so choose according to the security requirement of your business.
A penetration testing methodology in India will keep in check the accuracy, efficiency, and consistency of the pen testing and its report. It ensures that Pentest will not miss any potential security weaknesses.
Choosing a methodology that tailors according to your organizational goal is important, as the methodology guideline is the benchmark for your cyber security and provides recommendations to the testers.
Frequently Asked Questions (FAQs)
1: What are the most effective penetration testing methodologies for businesses?
Ans: The most effective penetration testing methodologies for businesses are grey box testing, black box testing, and white box testing, as well as penetration test frameworks like OSSTMM, OWASP, PTES, ISSAF, and NIST. These pen-testing methods help to detect and address potential weaknesses before hackers can take advantage of them. Pen-testing not only identifies cyber security issues but also provides remedies for those issues.
2: How does the choice of penetration testing methodology impact business security?
Ans: The penetration testing methodology provides a complete assessment of the internal structure of the system, detects security weaknesses, ensures that the testing process is repeatable, and helps to meet the complaint requirements.
3: What factors should businesses consider when choosing a penetration testing methodology?
Ans: There are many factors to consider when choosing a penetration testing methodology. They are:
Ensure the methodology aligns with your business needs
Choose the ones that effectively meet the industry compliance requirements
Consider the cost and time of each methodology
Go through their guidelines and technical instructions to understand their transparency.







