UAE (United Arab Emirates) has experienced significant advancement from economic, technologic, and most importantly, cybersecurity perspectives. Its excessive involvement in securing the digital landscape in the land could be felt through the introduction of the OWASP (Open Web Application Security Project) Foundation.
With OWASP actively evolving in the UAE to enhance software security in open-source projects, it’s the OWASP Top 10 Privacy Risks project that has been gaining momentum. This allows you to identify and gather the top 10 privacy risks in the web applications – simultaneously adopting respective countermeasures to tackle every risk involved.
The scope for digital risks has expanded – thanks to the UAE-approved National Cybersecurity Strategy in February 2025 for emphasizing governance, protection, innovation, capacity-building, and partnership simultaneously. A move that simultaneously mandates national efforts to combat potential risks now equally requires the UAE businesses to align OWASP Top 10 Privacy Risks to directly support national priorities.
We also have tips for implementing privacy, which can help web application providers and developers improve privacy in the software. The list uses OECD user privacy guidelines as a baseline framework, also leveraging the top 10 privacy guidelines to eliminate web applications-associated privacy risks.
This blog takes you through the top 10 privacy risks and how to tackle them with appropriate counter measures.
Table of Contents
ToggleOWASP Top 10 Privacy Risks That The UAE Businesses Be Aware Of
1. Web Application Vulnerabilities
Vulnerability is a core concern in any system that guards or runs on sensitive user information.
If you fail to design and deploy an application without detecting potential issues and patch them on time, you risk a privacy breach.
For example, the injection flaws let attackers manipulate or copy the data with the advantage of SQL injection or related attacks.
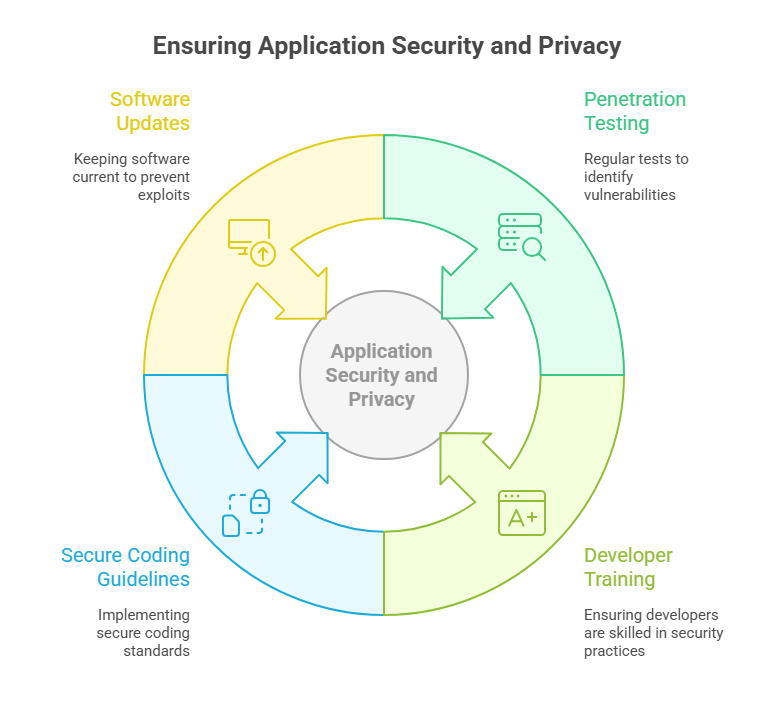
How to Check?
- Do regular penetration testing emphasize privacy?
- Are the developers well-trained in web application security?
- Are the coding guidelines implemented securely?
- Is any software outdated?
What are the Countermeasures?
- Conduct a penetration test by authorized cybersecurity experts.
- Perform usual vulnerability and web privacy scans using automated tools like DAST, IAST, SAST, etc.
- Implement procedures like SDL (Security Development Cycle) and DevSecOps for secure development.
- Deploy updates, patches, and hotfixes regularly.
2. Operator-Sided Data Leakage
The inability to prevent data leakage specific to the user data, or the data itself, to an unauthorized party leads to data confidentiality violation. Any unintentional mistake or intentional/malicious breach can trigger such a risk. Potential causes include a lack of proper access management controls in place, data duplication, and lack of awareness.
Every organization – local or international, processing the personal data of the UAE residents should strictly implement strong access controls and encryption as mandated by the Federal Decree‑Law No. 45 of 2021 (PDPL), enforced since January 2022.
With the financial institutions and telecom operators also falling under additional obligations by the Central Bank/TDRA, this requires them to strictly align their data encryption and operator-side leakage prevention with sector-specific regulations.”
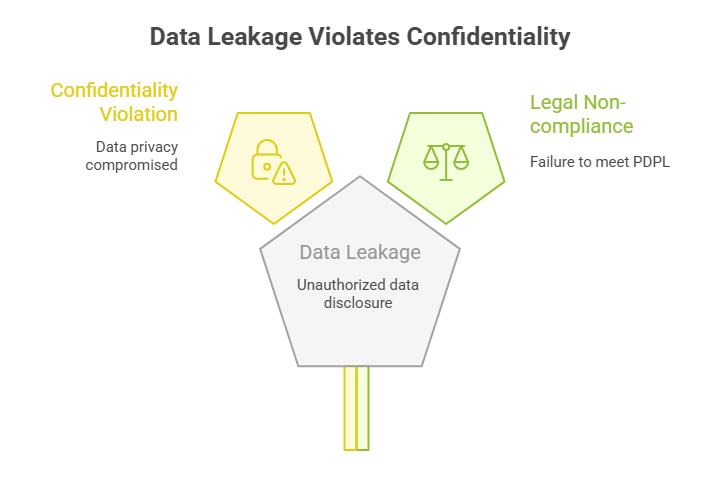
How to Check?
- Analyze the reliability and reputation of the operator
- Are there any breaches existing specific to the operator?
- Does the provider offer privacy and security proactively?
- Is personal data encrypted and anonymized?
- Are the privacy standards connected with the best practices?
- Who has the access to encryption keys and data?
- What are the audit methods used?
What are the Countermeasures?
- Use proper methods for authentication, access management, and authorization
- Adopt multi-factor authentication
- Avoid local accounts
- Use strong encryption for every stored personal data, including mobile media
- Anonymize personal data and use it for testing/marketing
- Use pseudonymization i.e., data can be connected only to a person using a third-party service
3. Insufficient Data Breach Response
As an organization handling user data, if you fail to inform your users regarding a potential breach or information leak, this means you’ve a poor response to such grave issues.
No matter how intentional or unintentional these events are, if you don’t care to mitigate the situation by reducing identified leaks, you’re only causing the risk to prevail – and multiply.
Also Read : OWASP API Security Top 1 0 (2024 Updated)
Every data breach incident should be notified to the UAE Data Office, also to data subjects to a certain extent – mandates PDPL. However, formal timelines may await Executive Regulations.
Also, Federal Decree‑Law No. 34 of 2021 (Cybercrimes Law) and complementary updates require mandatory incident reporting to authorities for cyber incidents.
How to Check?
- Are incident response plans in place?
- Is the plan up for regular testing?
- Is there a CERT (Computer Emergency Response Team)?
- Do you adopt incident monitoring?
- Do you notify the individuals and relevant parties in time?
- Organizations that undergo a privacy breach should convey the nature and scope of the breach to the affected.
- Have you established a company-wide policy for breach notifications?
What are the Countermeasures?
- Develop and maintain an incident response plan
- Test the incident response plan consistently
- Incorporate privacy-specific incidents in the test
- Have an expert CERT team
- Monitor personal data leaks and loss regularly
- Validate and notify the breaches to the responsible incident manager
- Determine the nature, composition, and scope of the breach
- Decide on how to investigate to ensure effective management of the evidence
- Gather and review all breach response documentation and assess the reports
4. Consent on Everything
This risk signifies that you are inappropriately using or aggregating consent for legitimate processing.
Consent is not collected for each purpose, instead, it is on ‘everything’. The concerns with getting consent also add to the insufficient information and the non-transparent policies.
For example, personal data purchases get imported into the application in which the consent is unknown or not sufficiently capable of verification.
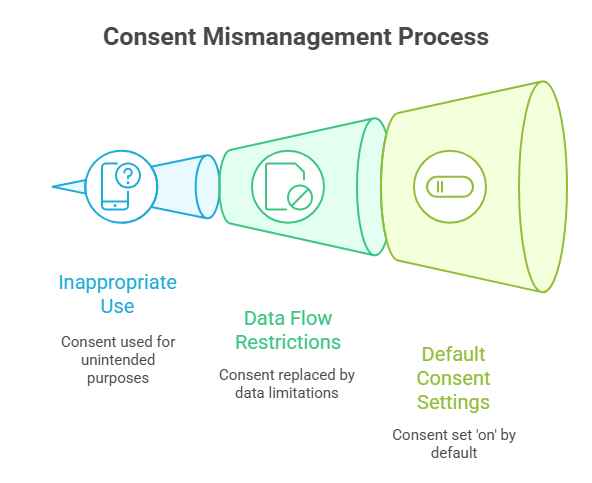
How to Check?
- Is consent inappropriately utilized for legitimate processing?
- Is the consent replaced by data flow restrictions?
- Is the default setting ‘on’ for consent in those purposes that don’t necessarily serve the context?
What are the Countermeasures?
- Get the consent individually for each purpose (for instance, using a website and profiling to carry out advertising )
- Ensure that the consent is voluntary
Efforts to combat phishing and cybercrime through the public awareness campaigns launched by the UAE authorities (specifically, UAE Banks Federation) targets both businesses and citizens to underpin the significance of transparent and user-centric privacy policies – thus, complementing their regulatory updates”.
5. Non-Transparent Policies, Terms and Conditions?
As a business, especially one operating in the UAE, you are bound to offer adequate information on how you process user data. This ranges from data collection to deletion. If you fail to make the data easily accessible or understandable to non-legal persons, these will signify ‘non-transparent policies, terms and conditions.
How to Check?
- Ensure that the policies, terms, and conditions are easy to find
- Know who processes the data and manages the data transfers
- What is the retention time?
- Is it understandable to non-lawyers?
- Does the process follow KISS (Keep It Short and Simple)?
- Explain what data is collected and for what purpose
- Use a readability score to find how hard the text is to read
- Are the privacy rules communicated actively?
What are the Countermeasures?
- Terms and conditions should be particularly dedicated to the use and data processing of the site
- Not too long and easily understandable to the non-lawyers
- Offer an easily understandable summary of terms and conditions
- Use of pictograms for visual aid
- Individual T&Cs for data processing and use
- Using release notes to understand the change history of T&Cs
- Take note of the users who consented to which version and the time they could move to the newer versions
- Know the purpose of collecting the information
- Offer a list of cookies and widgets to define the use, for example, data sharing, and advertising
- Have an opt-out button to focus users
Also Read : Why Do UAE Businesses Need OWASP Web Application Penetration Testing in 2025?
6. Insufficient Deletion of Personal Data
Not able to effectively or promptly delete the personal data after terminating the particular purpose or upon request.
For example, customer data is automatically deleted after a long period of inactivity. Hotmail adopts this process, where user profiles get deleted followed by a year of inactivity.
How to Check?
- Evaluate the data retention and deletion policies
- Assess their appropriateness
- Request deletion protocols
- Test the deletion request processes
- Check for transparency. Find which data is deleted, when, which is not deleted, and why.
What are the Countermeasures?
- Implement a data deletion concept
- Deploy and document data retrieval, data archival, and data deletion
- Delete personal data on rightful user request
- If detection is not available due to technical constraints, go for secure locking
- Reduce the risk through real deletion
- Collect evidence to verify the deletion based on the policy
- Consider all the data in the backups and share them with the third parties
- Consider cryptographic wiping of the backed-up and archived data
- Delete the user profiles that have long inactive periods
7. Insufficient Data Quality
When you use incorrect or outdated user information, you run the risk of insufficient data quality. This can happen due to ambiguous instructions while processing data collection, likely technical errors, and incorrect data linking.
For example, an update form is fed to the website, which enables the user to update their personal data whenever needed. A shop that confirms if your address and account data are valid before you complete the order is called CRM clearing.
How to Check?
- Ask the operator how this is ensured and personal information is up-to-date
- Find possibilities to update personal data in the application
- Is there regular checking to validate whether the data is up-to-date?
- How long is it likely that the information is updated and usually differs?
What are the Countermeasures?
- Have a procedure that validates user data
- Adopted process to update the personal data with inputs after a particular period
- Approve data if the user triggers a critical action
- Offer a form to let users update their data
- Make sure you forward the information to any third parties or subsystems that earned the user data in the prior session
- Have consistency checks against copy/paste and typographical errors
8. Insufficient or Missing Session Expiration
This risk gets triggered if you cannot effectively enforce the session termination. It can cause additional user data collection without the consent or awareness of the user.
For example, Facebook does not have an automatic session expiration. Here, the user needs to log in manually. If the user does not log out actively, and if somebody else uses the device, they can manipulate the user’s profile.
How to Check?
- Is it easy to find and promote the logout button?
- Does an automatic session timeout exist for applications? (< 1 week usually, but <1 day for critical applications)
- Do you have session timeout lengths aligned with the length required to finish the transaction?
- A service can support different combinations of session, sensitivity, and length. Are the timeout lengths adequately tuned to the sensitivity required for the session accesses?
What are the Countermeasures?
- Set an automatic session expiration. This could change based on the criticality of the data and application
- Session timeout should not be set for more than a week and should be reduced for critical use cases as mentioned
- Keep one day as the default setting for medium criticality
- Session timeout needs to be configured by the user as per their needs
- If the user has not used the logout button to end the last time session, the user should get a reminder message during the next login
- If you can’t logout or if the logout doesn’t completely terminate the session, data continues to be collected
9. Inability of Users to Access and Modify the Data
Users lack the ability to access, modify, or delete the data specific to them.
For example, the information degrades with time and leads to inaccuracies, which can adversely impact an individual.
How to Check?
- Is it possible to view your own data?
- Is it possible to request changes in data and updates?
- Are updates forwarded or accepted by third parties?
What are the Countermeasures?
- Allow direct access, change and delete data through a user account
- Offer other means to get, modify, and delete user-specific data
- Perform timely user requests and consider third parties
- Track user requests
10. Data collection not required for user-consented requirements
Collecting demographic, descriptive, or any user-specific data is not required for system purposes. This also applies to the information for which the user doesn’t provide consent.
For example, a webshop offers advertisements to the users. This can be disabled, however has the default setting on. It should be disabled by default from a privacy point of view, and the user should opt in for personalized product recommendations.
How to Check?
- List personal data the application collects
- Request description of purpose
- Check whether the collected data is needed to fulfill the need
- If data is collected and not required for the primary purpose, ensure that the consent to gather and process the data was offered and documented
- Are the individuals asked if the purpose has changed
- Are the OWASP compliance checks for personal data collection in place?
What are the Countermeasures?
- Determine the purpose of personal data collection
- Collect only personal data required to satisfy the purpose
- Collect as little data as possible unless the user opts otherwise
- Offer the data subject an option to offer additional data voluntarily to enhance the service
- The purpose for collecting personal data is specified no later than during the data collection
- Adopt Conditioned Collection: Collect personal data only if they are needed for a user feature
Governance, Standards & International Alignment
- UAE Cybersecurity Council (est. 2020) presides over cross-sector coordination, intelligence sharing (via the “Crystal Ball” platform), and preparedness for national incidents.
- The 2025 cabinet-endorsed National Cybersecurity Strategy is committed to enhancing cybersecurity by offering AED 7 billion (~USD 2 billion) to strengthen efforts in there. These will include defining legislative roadmaps for cryptography policies, ensuring critical infrastructure protection, and encouraging public‑private‑people partnerships.
UAE organizations need to know, understand, and implement the OWASP top 10 privacy risks to ensure web application security. OWASP compliance helps businesses save user data by prioritizing and mitigating the risks specified there through adopting robust privacy controls. Businesses can use countermeasures to build trust with customers and prevent costly data breaches. In short, if you adopt a user-centric data privacy policy, you’re more than likely to retain customer trust besides meeting OWASP compliance when securing your web applications.
At Wattlecorp, we provide you with expert advice in cybersecurity. Whether it be to achieve the best comprehensive security solutions or stay compliant with data privacy policies, our team is there to guide you through every process to help you safeguard your critical systems, applications, and other valuable assets against privacy risks.
Note that only if you keep your systems and applications safe can you ensure data protection for your users that paves the way for your business continuity.
So, how compliant are your applications and systems with data privacy standards?
OWASP Top 10 Privacy Risk FAQs
1.How does the OWASP Top 10 Privacy Risks differ from the OWASP Top 10 Security Risks?
OWASP Top 10 Privacy Risks are way different from OWASP Top 10 Security Risks. While Privacy Risks emphasize protecting personal data, Security Risks lay focus on securing the web applications.
2.How does compliance with GDPR, CCPA, and other privacy regulations in the UAE align with the OWASP Top 10 Privacy Risks?
Compliance with the CCPA and GDPR goes hand in hand with OWASP Top 10 Privacy Risks with the help of reliable data protection measures. These should eliminate risks like data breaches, unauthorized access, and inadequate data deletion. The regulations require organizations to execute security measures and maintain appropriate data handling to avoid legal hassle.
3.What is privacy violation vulnerability?
Privacy violation in the UAE arises whenever sensitive information, like the users, location, associations, or interactions, is linked to a particular individual. It is important to determine where and how the private data gets exposed and apply access controls to make sure that only the authorized team has the access to the sensitive information.