Imagine if you could read the minds of real-world hackers before they start attacking your business. It will be a proactive step from your side to protect your systems, applications, and data. Tackling the continuously evolving cyber threat landscape requires thinking like a hacker.
This is where VAPT (Vulnerability Assessment and Penetration Testing) creeps in. The purpose of VAPT is to identify and mitigate potential security threats by evaluating, assessing, and prioritising risks based on their severity and impact. When carried out with all experience and expertise, VAPT helps keep cyberattacks out of harm’s way,
With more and more businesses opting for real-world attack simulations with threat-led VAPT to strengthen their cybersecurity posture, this blog sets out to explore why this technique is in demand. It also explains the role of ethical hackers-cum-pen testers in this endeavour.
Table of Contents
Toggle- What is Threat-Led VAPT?
- Advantages Of Threat-Led VAPT
- Case Study To Convey The Significance Of Threat-Led VAPT
- How ‘Ethical Hacking’ Helps Simulate Real-World Attacks: Process Explained
- Role of Threat-Led Penetration Testing In Strengthening Cyberdefence For Organisations
- Choosing the Right Threat-Led VAPT Provider
- Threat-Led VAPT FAQs
What is Threat-Led VAPT?
Being an advanced form of VAPT, threat-led VAPT or threat-led penetration testing (TLPT) holds considerable significance in undertaking a proactive security assessment. It involves a focused approach with security assessments, particularly modelled to understand and tackle real-world threats. In essence, threat-led VAPT requires putting yourself in a hacker’s shoes.
The role of ethical hackers/penetration testers in carrying out threat-led vulnerability assessment and penetration testing is pivotal to preventing actual exploitation. By conducting threat intelligence and analysis to simulate real-world attacks, ethical hackers help strengthen your security posture. The threat intelligence and analysis process is also effective in monitoring emerging threats and evaluating their potential risks. This helps organisations proactively identify and mitigate vulnerabilities by getting to know the tactics, techniques, and procedures that malicious hackers employ.
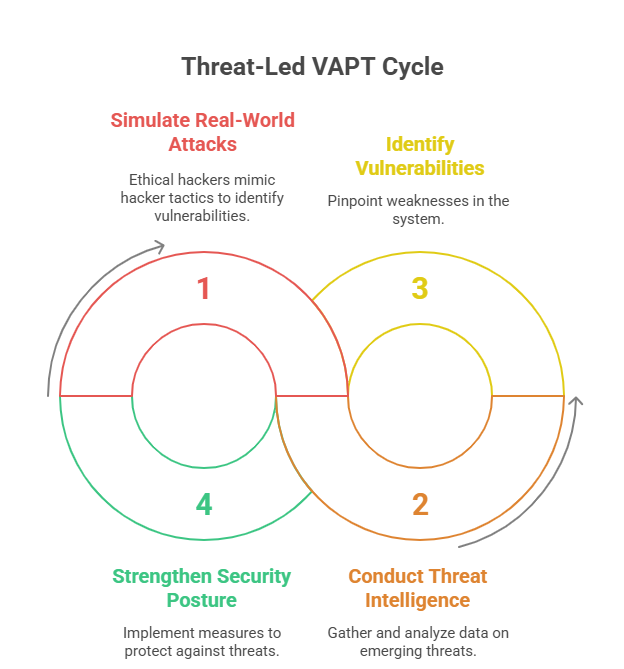
Why Should You Prefer Threat-Led VAPT?
Again, threat-led VAPT focuses on simulating real-world attacks by relying on specific tactics, techniques, and procedures (TTPs) that hackers utilise. This allows penetration testers to conduct more robust security assessments, which paves the way for proactive risk mitigation.
To understand why you should consider undertaking threat-led VAPT over traditional penetration testing, you should know how these differ from each other. Experts mention that the three parameters help differentiate traditional and threat-led VAPT.
- Focus
Traditional VAPT: Can identify a wide range of potential security flaws in applications, networks, and systems.
Threat-Led VAPT: Helps simulate real-world attacks or exploits which are based on specific threat actor profiles or attack vectors.
- Approach
Traditional VAPT: Adopts generic-cum-automated processes for scanning potential vulnerabilities.
Threat-Led VAPT: Mainly relies on threat intelligence mechanisms and analysis to design and execute penetration tests.
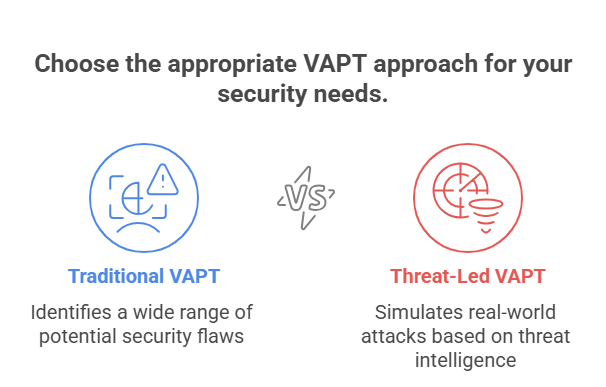
- Goal
Traditional VAPT: Aims to offer a comprehensive list of vulnerabilities that are likely to be exploited.
Threat-Led VAPT: Targets those vulnerabilities which real-world hackers can potentially exploit.
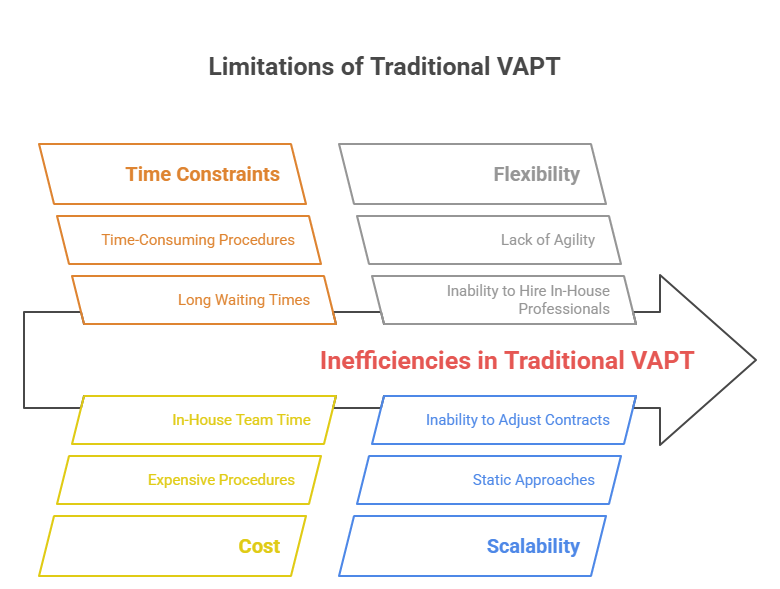
Traditional VAPT processes also come with certain limitations. Let’s get to see what these are:
- Takes Too Long to Get an Appointment For Penetration Testing: Traditional penetration testing companies make their clients wait for a considerable period of time. The waiting time can range from weeks to months.
- Expensive Procedures: Not only are traditional penetration testing procedures expensive, but they also take valuable time for in-house teams when they can instead focus on daily tasks.
- Lacks agility and flexibility: Traditional VAPT is bound by a lack of flexibility. This means that an organisation’s in-house VAPT professionals cannot be hired to undertake third-party penetration testing.
- Nonscalability: The static nature of the approaches made in traditional penetration testing limits it from attaining scalability. This static nature makes it rigid enough to prevent any adjustments for changes within a contract.
Advantages Of Threat-Led VAPT
When compared to traditional VAPT, threat-led VAPT offers a score of advantages. Some of these include:
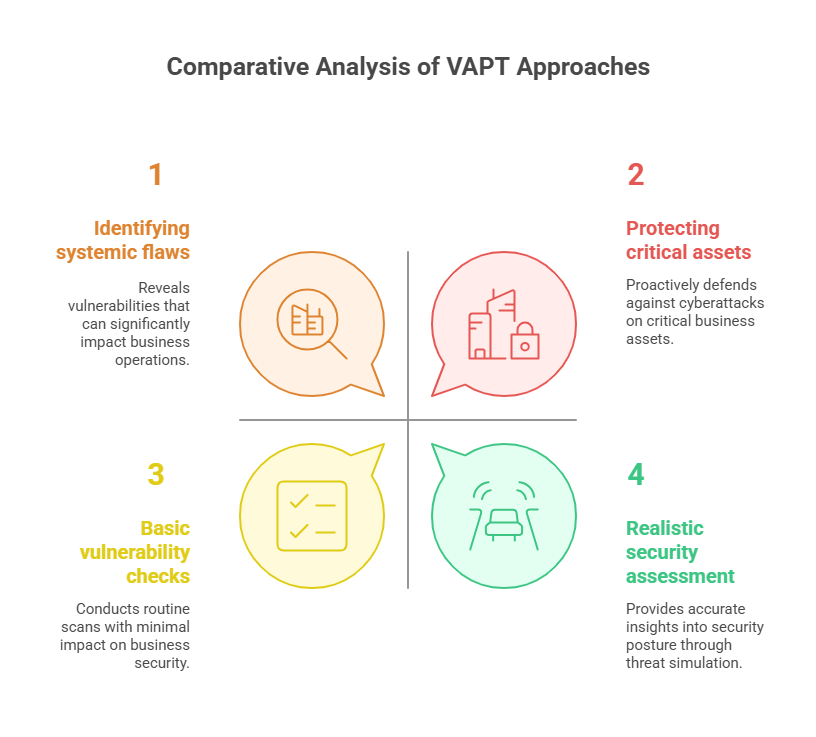
- Protecting business-critical assets
Its ability to identify vulnerabilities that can highly impact the most critical assets of a business makes threat-led VAPT stand apart from its traditional VAPT. By targeting intellectual property, financial and customer data, TLPT proactively defends them against actual cyberattacks.
- Simulates Advanced Persistent Threats (APT)
Threat-led VAPT goes beyond conducting basic vulnerability scanning by simulating real-world APT-related attacks. Potential tactics include social engineering, physical security testing, and network exploitation. A mature, manually-driven pentest can uncover the same vulnerabilities. The difference lies in understanding the threat-context & breadth.
While traditional pentests frequently reveal systemic flaws, TLPT adds real-world threat context and endurance that standard point-in-time tests lack.
- Provides a realistic security assessment.
Threat-led penetration testing offers a more accurate assessment of the security posture of an organisation. Focusing on realistic threats takes credit for this. This further goes on to enable effective resource allocation and prioritise remediation efforts.
Case Study To Convey The Significance Of Threat-Led VAPT
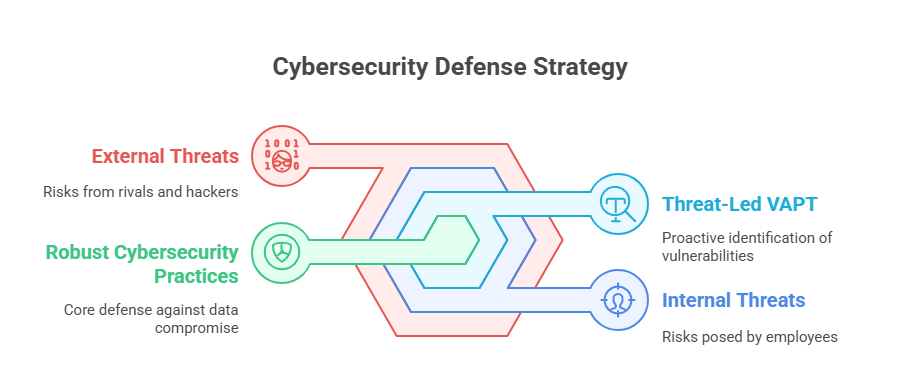
General Electric, one of the US multinational companies, was involved in a notorious cybercrime, where an employee allegedly stole over 8000 sensitive files through a data breach. An incident spanned not one or two, but eight long years!
The intruder’s intent to extract commercially sensitive data was to start a rival company, serving as an engineer to the concerned firm. Persuading the IT administrator to grant access to critical information rightly conveyed that organisations cannot always be sure of their security.
Lesson Imbibed: Hackers are there everywhere. While some of them may be your business rivals spying on your processes, at other times, they may also be your own in-house employees – knowingly or unknowingly triggering data compromise. Adopting robust cybersecurity practices by implementing threat-led VAPT is your first line of defense.
How ‘Ethical Hacking’ Helps Simulate Real-World Attacks: Process Explained
The answer is the same – think like a hacker. The so-called ‘ethical hackers’ (let’s refer to them as white-hat hackers) adopt a comprehensive approach to exploit vulnerabilities in your systems and networks. The intent is not to harm them, but to strengthen security.
Let’s now see what ethical hacking involves.
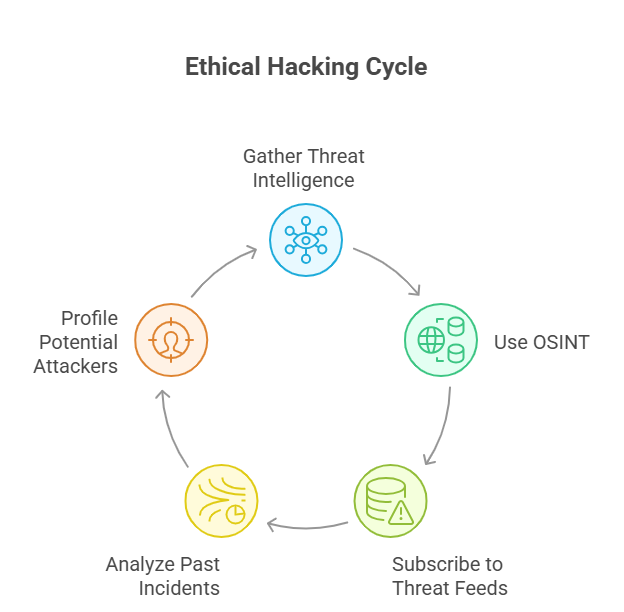
- Threat Intelligence Gathering
Purpose: To collect information about potential vulnerabilities, threats, and attack patterns and gain an understanding of the risk landscape.
Methods involved:
- Open Source Intelligence (OSINT): Involves collecting data from publicly available sources like news articles, social media, and forums. OSINT happens to be a highly valuable tool because it enables white-hat hackers to gather information in a quick, efficient, and cost-effective manner. It also helps offer up-to-date data on emerging threats.
- Threat Feeds: Subscribing to databases and services that share information about known vulnerabilities and threats.
- Analysing Past Incidents: This method examines previous security breach incidents and associated vulnerabilities to identify patterns and trends of attacks.
- Profiling potential attackers: Helps identify and categorise potential attackers for a better understanding of their characteristics, tactics, and motivations.
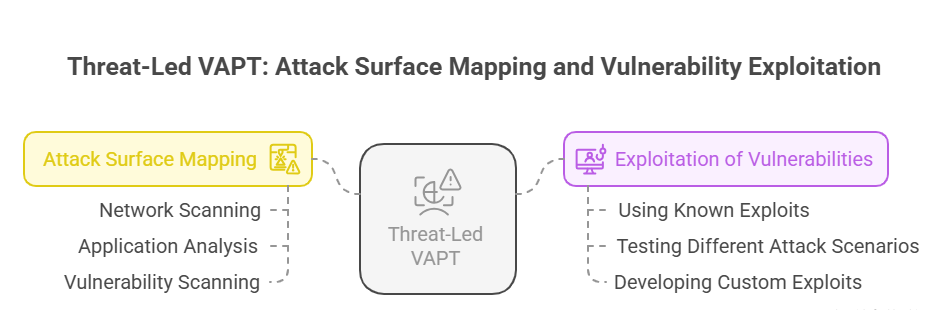
- Attack Surface Mapping
Purpose: To identify potential entry points and attack vectors that may invade an organisation’s applications and systems.
Methods of attack surface mapping include:
- Network Scanning: Assists with mapping out the network infrastructure and checking devices, services, and ports for detecting and exploiting vulnerabilities.
- Application Analysis: Examines the structure and functionality of applications to identify potential security flaws.
- Vulnerability Scanning: Utilises specific tools to identify vulnerabilities within the hardware, software, and network configurations. These include vulnerability scanners, (Nessus and OpenVas; network scanners (Nmap), and web application security (Burp Suite and OWASP ZAP).
- Exploitation of Vulnerabilities
Purpose: To demonstrate how identified vulnerabilities can be exploited to acquire unauthorised access to systems and data.
Methods to exploit vulnerabilities include:
- Using Known Exploits: Helps conduct exploits for known vulnerabilities by utilising publicly available tools and techniques, such as BurpSuite, Nmap, Nessus, etc.
- Testing Different Attack Scenarios: Assesses the effectiveness of security controls’ by simulating various attack scenarios through a process called BAS (Breach and Attack Simulation).
- Developing Custom Exploits: Creates new techniques to exploit lesser-known vulnerabilities. These include network scanning, penetration testing, and social engineering to examine various aspects of a system’s defense in a detailed manner.
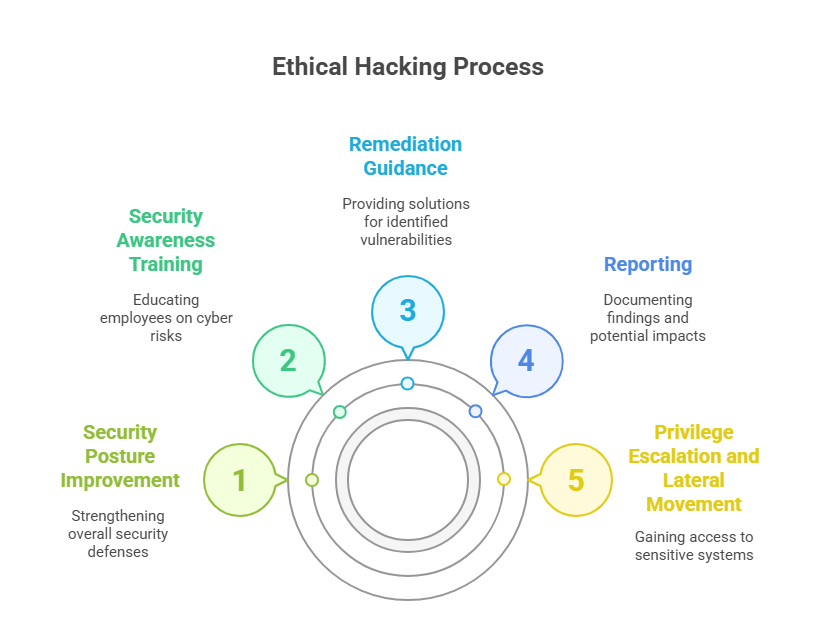
- Privilege Escalation and Lateral Movement
Purpose: To escalate privileges once access to sensitive data and systems is gained by moving laterally within the network.
Methods involved
- Privilege Escalation: Gaining higher-level access, such as administrator or root access, by exploiting vulnerabilities.
- Lateral Movement: Accessing more systems and data by moving sideways from one compromised network to device and so forth. This allows for escalating access privileges and reaching the ultimate target, namely vulnerability exploitation.
- Reporting and Remediation Guidance
Purpose: Documenting the findings of the ethical hacking assessment and providing recommendations for remediation of identified risks and subsequently improving/strengthening the security posture.
Methods Involved
- Detailed Reports: Create comprehensive reports for vulnerabilities that were identified, including methods of exploitation, and outlining the potential impact of the vulnerabilities.
- Recommendations for Remediation: Providing specific guidance to fix the security flaws and improving security controls.
- Conducting Security Awareness Training: Educating employees on cyberattack risks by demonstrating ways to protect systems and networks.
Remember that the ultimate objective of the ‘ethical hacking’ process by mimicking real-world cyberattacks is to proactively defend your systems and network.
Role of Threat-Led Penetration Testing In Strengthening Cyberdefence For Organisations
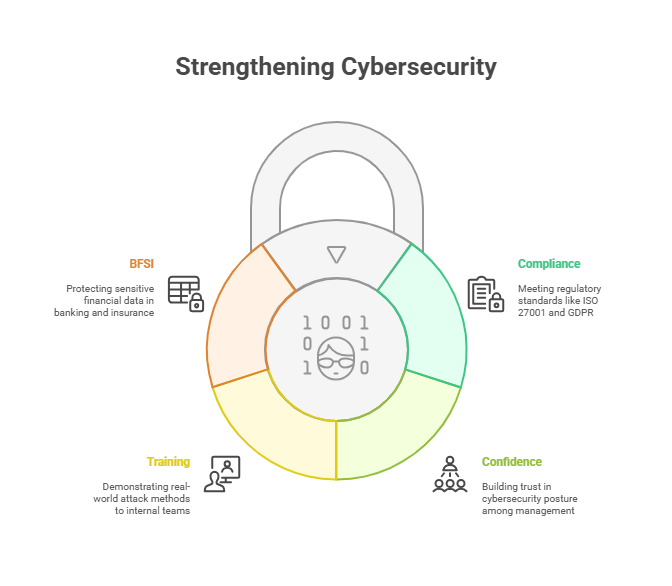
The role of threat-led penetration testing is critical to strengthening cybersecurity for organisations. With the cyber threat landscape evolving relentlessly, companies need to execute cyber defence strategies that will enable them to:
- Meet compliance and regulatory requirements (ISO 27001, GDPR, HIPAA, etc.).
- Build management confidence in enhancing cybersecurity posture.
- Demonstrate real-world attack methods to internal teams as part of training.
Industries that Must Consider Threat-Led VAPT
Every organisation, regardless of its industry, is meant to implement threat-led VAPT to maintain security. Industries that should mandatorily consider TLPT include:
- BFSI (Banking, Financial Services, and Insurance)
Banking, financial institutions, and insurance companies handle large volumes of user and employee-sensitive financial and personal information. Due to this, they are likely to face constant threats from cybercriminals.
With the increasing cost of cybercrime events rising from $8 trillion in 2023 to $10.5 trillion in 2025 due to ransomware attacks, mandates BFSI to adopt cyberattack simulation techniques.
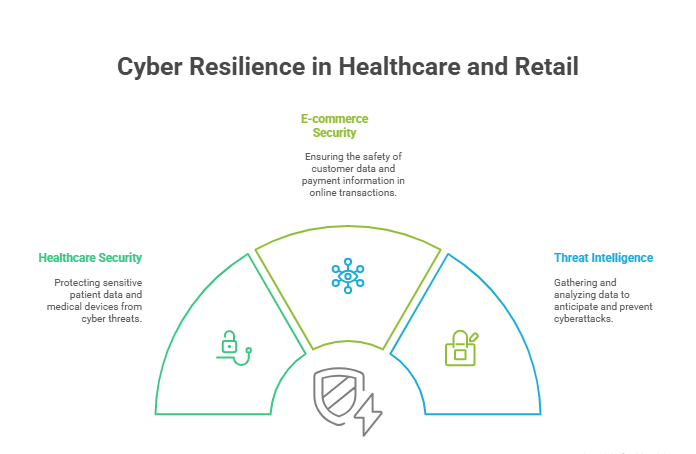
- Healthcare
The healthcare sector has undergone significant changes, thanks to digital evolution. From electronic health records (EHR) to facilitating telemedicine platforms, these are some of the healthcare transformations.
However, with cyberattacks manifesting as ransomware, data breaches. IoT vulnerabilities, etc., are likely to disrupt the sensitive operations. These include maintaining EHR and securing Iot-enabled medical devices, to name a few.
To prevent healthcare facilities from undergoing any legal penalties due to using outdated software and hardware, they must integrate advanced penetration testing strategies. This is mandatory as far as ensuring a smooth and efficient healthcare operation and service is concerned, including proper diagnosis and care rendition.
- E-commerce and Retail
The industry faces constant threats from hackers. These include hacking sensitive customer data and accounts. Since earning customer trust is crucial for seamless operations and service, the E-commerce and Retail sector is supposed to integrate TLPT.
It is equally critical to ensure payment information security. The E-commerce and retail sector should implement a threat intelligence model to simulate real-world cyberattacks. Efforts such as these can significantly help improve their resilience against advanced cyber threats.
Choosing the Right Threat-Led VAPT Provider
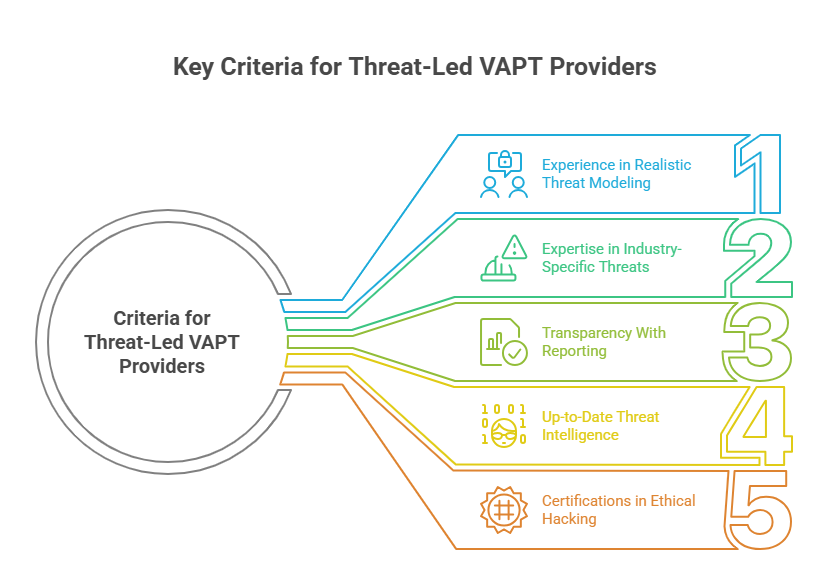
If you are looking for a threat-led VAPT provider, you should focus on the following criteria:
- Experience in Realistic Threat Modeling: Should possess a strong understanding of security risks before developing a threat modeling system to proactively address potential vulnerabilities.
- Expertise in Industry-Specific Threats: Be able to understand the unique security vulnerabilities and attack vectors prevailing in a specific sector.
- Transparency With Reporting And Remediation Support: Effectively offer transparent and clear reports on security status with recommendations for strengthening the security posture.
- Up-to-Date Knowledge On Threat Intelligence Techniques: Analyse threat actor tactics, techniques, and procedures (TTPs). Utilising specific threat intelligence tools will not only help understand hacker strategies, but will also effectively render the defense mechanisms to avert potential cyberattacks in the future.
- Certifications In Ethical Hacking: Hiring a certified ethical hacker is essential to carry out threat-led penetration testing in all effectiveness and efficiency. The expertise and knowledge of the concerned experts allow them to take a more comprehensive approach to identifying and mitigating security vulnerabilities.
Traditional penetration testing can no longer withstand the complexities of the constantly evolving cyber threat landscape. To beat them calls for a more advanced approach to penetration testing. Threat-Led VAPT is the need of the hour as it can prudently and effectively help beat the highly sophisticated threat vectors.
How Wattlecorp Conducts Ethical Hacking
Our expert VAPT professionals can ethically hack your business’s security posture by carrying out an in-depth evaluation.
The process involves:
- Reconnaissance: Understanding your IT infrastructure and network. These include apps, servers, websites, workstations, WAN, LAN, endpoints, and other network components.
- VAPT: Simulate real-life hacking attempts by breaching your network through internal and external methods, stopping short of actual exposure.
- Reporting and Remediation: Compiling findings through a detailed report to mention vulnerabilities and their possible impact upon exploitation.
- Retest: The vulnerabilities, once detected, are analysed for their potential impact and chance of occurrence. This is followed by offering expert suggestions to remediate and improve security posture for your systems, network, and applications.
You can connect with us to have your network security tested or to analyse your servers. At other times, it would be to check your endpoints or workstations. Whatever your security needs, our VAPT, with its expert white-hat hacking techniques, is there to solve and protect your business from cyberattacks.
Your commitment to ensuring data security for your clients and stakeholders is our priority. Be assured that your data privacy is in our safe hands, helping you to stay adherent to compliance requirements.
Let our ethical hacking method help expose your vulnerabilities before the black-hat hackers exploit them“
Book a free consultation to build a threat-led penetration testing strategy for your business and keep hackers away!
Threat-Led VAPT FAQs
1.What is a Threat-Led VAPT assessment?
Threat-Led VAPT assessments or threat-led penetration test (TLPT) are a type of cybersecurity assessment that aims to evaluate an organisation’s resilience against advanced cyber threats. Also known as a form of Red Teaming, threat-led VAPT/TLPT simulates real-world cyberattacks.
2.How does threat-led VAPT simulate real-world attacks?
Threat-led VAPT simulates real-world cyberattacks by using threat intelligence to inform attack scenarios. It primarily involves ‘red teaming’ a process that appoints teams to exploit vulnerabilities and bypass security controls. The primary intent is to strengthen your cyberdefense strategies.
3.What are the ethical hacking techniques involved in threat-led VAPT?
The key ethical hacking techniques in threat-led VAPT involve:
– Reconnaissance & Information Gathering: Collects all necessary information regarding the target system, application, or network to understand its strengths and vulnerabilities. Includes processes, such as footprinting, OSINT (open source intelligence), network scanning, and vulnerability scanning.
– Exploitation & Penetration Testing: Simulating a cyberattack by identifying and exploiting vulnerabilities in a system or network. Includes password-cracking, SQL injection, cross-site scripting, etc. to undertake the process.
– Post-exploitation: The phase following successful exploitation of a computer system, network, or application. This is a vital phase in ethical hacking, which focuses on what happens after you gain system access. Moving laterally, gathering intelligence, and maintaining persistence while avoiding detection are what post-exploitation involves.
– Threat intelligence & scenario development: Involves threat intelligence gathering, scenario development, and red teaming exercises to simulate attacks in a controlled environment.