With the ever-evolving Internet of Things (IoTs) and the convenience they offer, there is a need to address IoT security threats. Today, in the workplace as well as at home, we are heavily dependent on IoT applications, but IoT-enabled devices are very susceptible to cyberattacks that can result in the alteration of data or data losses.
Most IoT devices are developed for a singular purpose, thus limiting their memory storage, and no interface can be implemented, hence their lack of built-in security. Due to the diversity of devices and exposure to the public internet, attackers easily penetrate the system. To prevent such unauthorized access, proper security measures are to be deployed.
This article discusses the IoT security risks, the best practices, and the necessary steps to implement a secure IoT ecosystem. There are security measures to be taken by IoT device manufacturers and end users to enhance IoT security.
Table of Contents
ToggleWhat Is IoT Security?
IoT security refers to the security practices and strategies used to protect all the connected devices in the IoT ecosystem from breaches and cybersecurity threats.
The best practices for IoT security involve monitoring and identifying threats, and data breaches on all the connected IoT devices.
An IoT device is a physical entity that comprises sensors, and software, The device is connected to at least one network interface or exchanges data with other devices via communication networks.
To manage IoT devices internally and externally, they are controlled by the Command & Control Center, which manages configuration, authentication tasks, maintenance, and addressing vulnerabilities. Data transfer between the devices is enabled by exposing application program interfaces (APIs).
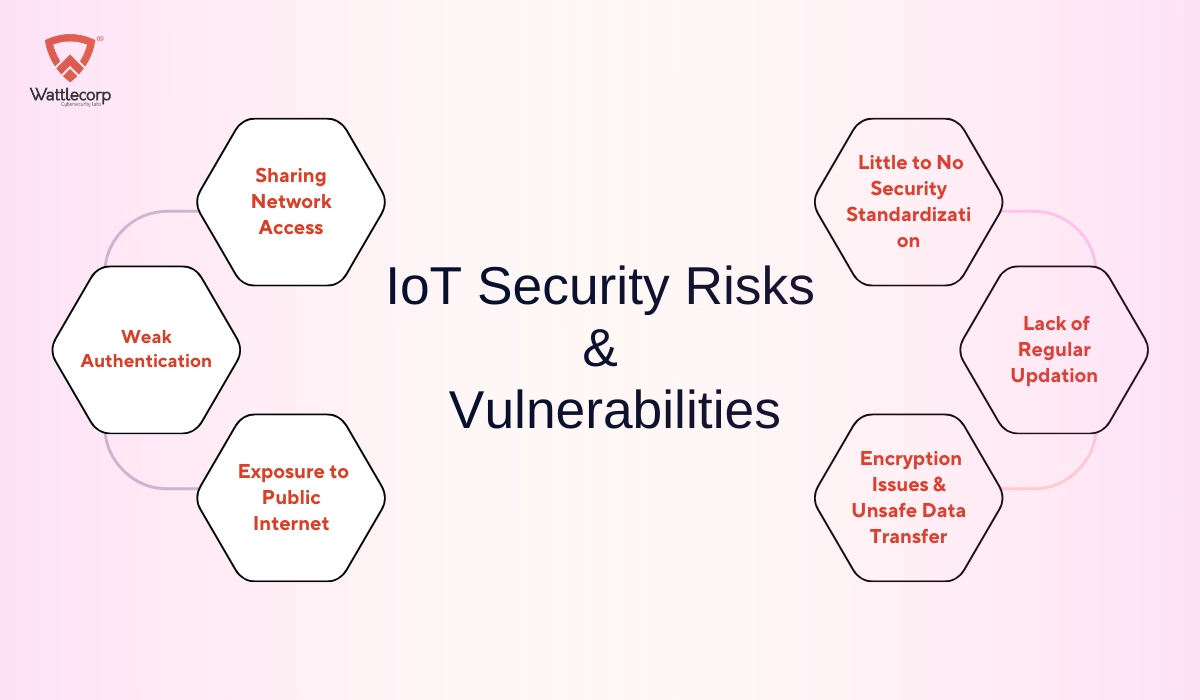
IoT Security Risks and Vulnerabilities
IoT devices are vulnerable to cybersecurity threats, but most of these threats can be mitigated with proper security awareness and by following basic security precautions.
Sharing Network Access
IoT devices often use the same network, such as WiFi or LAN, so that another device can be used to hack into IoT devices, making them susceptible to data breaches. Whenever your network or application connects or shares data with a device, they are very vulnerable to attacks as the device could be infected with malware.
Weak Authentication
Weak passwords, default passwords that remain unchanged, and devices that do not deploy proper authentication can be very prone to cyberattacks. Most home router manufacturers often use easily crackable passwords, which is a serious issue for IoT devices. Often, hackers integrate IoT devices with weak authentication into a botnet to spread malware or distributed denial of service (DDoS) attacks.
Exposure to Public Internet
Even if you keep your IoT device and the cloud application secured, since the mobile networks used by IoT devices constantly interact with cloud applications, every communication between the cellular network and the cloud application passes through the public network, which is highly prone to cyberattacks. Any form of malware can spread due to the exposure to public internet.
Little to No Security Standardization
Unlike other devices or networks, IoT ecosystems do not have an industry-authorized standard to follow; hence, the security guidelines are all entrusted in the hands of companies.
It is also impossible to ensure a consistent protocol or security standard for the devices and platforms within the IoT ecosystem.
Lack of Regular Updates
Outdated software and no security updates can leave IoT devices prone to security risks. Whenever the data transfer or connectivity becomes slower in your device, it can be easily attacked, so you need to regularly update them. Properly updating firmware easily mitigates such security risks.
Encryption Issues & Unsafe Data Transfer
Many IoT devices use unencrypted data for regular data transmission Also, transferring sensitive data via unsecured networks can make the device vulnerable to cyberattacks, making it easier for third parties to access sensitive data as well as credentials.
C&C Center and API Vulnerabilities
Man in the Middle (MITM), SQL code injections, and distributed denial of service (DDoS) are some of the vulnerabilities that mostly threaten C&C centres and APIs. Botnets are often used to perform DDoS attacks to spread malware and steal data.
Physical Security Risks
When IoT devices are stolen or physically handled by attackers, this can lead to unauthorized access to sensitive data, Make sure that such malicious actors can’t physically access your IoT devices.
Best Practices for IoT Security In 2024
By employing best practices for IoT security, you can easily block unnecessary access. The following are some of the best for IoT device security used in different industries.

1)Healthcare
Apart from other regular IoT devices, the healthcare industry deals with very sensitive devices such as pacemakers, devices, and wearables that closely monitor a patient. Any form of security breach can leak patient data and security attacks could even threaten patient life. To avoid potential breaches, ensure network security by providing network segmentation and facilitating separate networks for medical monitoring devices.
2)Businesses
System downtime and security risks due to data breaches can be colossal for the reputation of a company since sensitive data regarding the company as well as its customers is at stake. Make sure you prioritize security during the development and management of the IoT ecosystem Also, seek the advice and guidance of professionals when it comes to IoT security.
3)Automobiles
Ensure the vehicle is equipped with intruder detection system and firewalls to thwart unauthorized access. With the outburst of self-driving cars, the use of IoT technology also grows, as does the risk associated with it.
An attacker can use a multimedia system to connect to the network and devices in a car thus, it is important to isolate connected devices.
How to Secure Your IoT Devices?
Many security measures can be deployed to safeguard your IoT devices from potential cyberattacks.
- To counter weak authentication, make sure your manufacturer facilitates multiple-step authentication, uses strong default passwords, and sets parameters that lead to secure user-generated passwords
- Monitor the activity and performance of devices regularly.
- Make sure you can remotely disable connection if IoT devices are physically tampered with.
- To protect information in data, use strongly encrypted data during regular data transmission and storage.
- Segment devices by providing separate networks to each device, this can help secure the networks.

- Deploying Zero-trust architecture denies any random access, as users will have to undergo continuous validation and authentication.
- Software and firmware have to be regularly updated to minimize downtime and properly secure the system.
- One of the major reasons behind such security risks is the lack of awareness regarding best practices and proper security steps
- Ensure there are limited network endpoints
- Most IoT devices have limited computational ability, the end user should purchase a device with specific security software that suits their need
Things to Consider While Choosing an IoT Platform
IoT security platforms can help secure and manage IoT devices.
- Ensure communications can be secured and the data will not be compromised while storing with the platform’s APIs
- The platform’s design should be able to protect the network and application.
- Make sure the servers, storage, and network devices are physically secured
- IoT platforms should use a standard authentication and authorization process for access control
- When handling a security event, the IoT platform should enable applications to write audit logs, which are stored as they are and not externally modified after being written.
Security threats are ever-evolving, so there is a need for modified security solutions and best practices. IoT devices have become so common, specifically due to their convenience, smart workspace with automation, and connection to cloud applications, This has also made IoT security the need of the hour.
Reach out to an IoT security testing service provider and also schedule regular IoT security tests during events like purchasing new IT devices or when updating or reconfiguring existing devices.Providing in-built security on IoT devices can be a tedious task since there are no universal security guidelines or standardization. Proper software updates, secure authentication, and segregating device networks, can thwart some security risks.
Manufacturers, as well as end users, are responsible for implementing proper security measures to safeguard IoT devices. The primary security practice anyone should employ is to have proper awareness regarding IoT security risks and vulnerabilities.
Frequently Asked Questions (FAQ’s)
IoT devices often need more built-in security, and most IoT devices can be manufactured on a limited budget, so developing secure practices is not deployed. API or C&C center vulnerabilities, lack of encryption, insecure data transfer, lack of standardization, etc. are some of the challenges that make IoT devices more prone to malicious attacks.
By scanning your network, you can identify the active devices connected to the IoT network. All the IoT devices connected to your network have unique MAC addresses, Keep an inventory of the already connected MAC addresses and regularly update them to identify new IoT devices.
The first step to consider is to make sure the manufacturer you buy IoT devices from has installed built-in security in the device, ensure the platform is certified for compliance with ISO 27001, ISO 27017, and ISO 27018, use a secure password, implement a zero-trust IoT architecture, and limit network end-points. The key to implementing best security practices is to start by constantly educating people about the cybersecurity risks faced by IoT devices.








