The steady growth of API analytics since its inception has been explosive and This growth reflects organisations’ broader need to holistically assess the business and digital transformation impacts of API programs.
So we prepared this guide to act as your one-stop guide to understanding the complexities of API Security testing. Let’s dive in.
Table of Contents
ToggleWhat is API Security testing?
API security testing is the process of evaluating the security of an API by revealing any vulnerabilities that may grow to be a threat to data exchange between applications and interfere with normal operations.

API security testing also involves static API Security tests, Dynamic API security tests, and software composition analysis (SCA).
- Static API Security Tests: This API security testing method helps identify API security issues by examining the source code of an application.
- Dynamic API Security Tests: These tests simulate real-world attacks, including SQL injection attack tests, testing parameter tampering, input fuzzing, using random data in the API, etc.
- Software Composition Analysis (SCA) Tests: SCA is particularly important for using open-source components in APIs and is used to identify any known vulnerabilities in the libraries or frameworks you use.
Would you like to know how API security testing is handled by experts? Visit here to find out more.
API Security Standards
API gateways are equipped with security measures to ensure secure API testing processes. The API security testing compliances they follow include:
1. TLS
As of January 2021, over 89% of loaded pages were in HTTP format. Most businesses prefer to use HTTP because of its feasibility. Let’s be blunt here, if you are one among the 89%, you are compromising security for a few bucks or because of the certainty that the data is consumed internally.
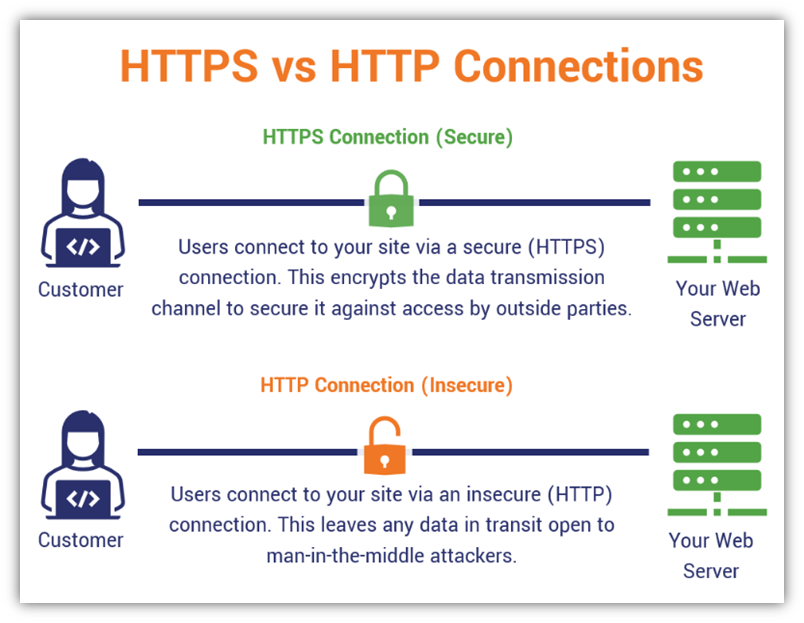
But If someone gains unauthorised access to your network, your plain HTTP serves them all your confidential data on a platter.
The alternative here is to use TLS 1.3 or HTTPS URLs. It provides an encrypted end-to-end data transfer.
2. Protection Against Traffic Spikes
In terms of website performance, it’s crucial for sites to be prepared for traffic spikes. In other words, if a site isn’t prepared for a sudden traffic increase, it could slow down or negatively impact user experience.
Here is where API gateways enter the scene.
They protect the sudden spike by setting limitations in the backend so that only a certain number of requests are processed. Sometimes client systems may be doing load tests or they can be legitimate clients or a DDoS attack. Having this security policy would ensure accurate management of these spikes in API calls.
3. Authentication, Authorization, and Identity
To safeguard your APIs from unauthorised access, certain fundamental measures are necessary. Depending on the type of API and its specific use case, one of the following strategies should be implemented:
- For APIs that require end-user authentication and consent, they should be secured using the OAuth2 Authorization Code Grant or OpenID Connect. These form the conventional security framework for authorization and user identity. You can find more information about these on their respective protocol pages — OAuth2 and OpenId Connect.
- In situations where user context or consent is not needed, and the consumer is either a trusted internal application or a partner application, the OAuth2 Client Credentials Grant is recommended for API security.
- If an API serves clients that are unable to execute OAuth2 token flows for any reason, it’s essential to apply at least API Key security. This ensures that client applications are authenticated. API keys can be accepted in either the request header or as a query parameter.
4. Protection Against Parser Attacks
APIs often receive JSON or XML payloads in requests. In these situations, there’s a risk that an attacker might try to send data that could overload the parsers in the backend services.
These types of attacks are intended to overload and disrupt the parsers, leading to server downtime and potential DoS attacks. As a result, any API that anticipates JSON or XML payloads should implement schema or structure-level validation to safeguard the parsers.
5. Preventing SQL Injection, HTML Script Injection and Other Injection Attacks
SQL Injection, HTML Script Injection, Java Exception Injection, and various other code injection attacks are frequently encountered. In these content-based attacks, intruders aim to access data that should be off-limits to them. Regrettably, APIs often lack the necessary safeguards to ward off such attacks, leaving backend services exposed.
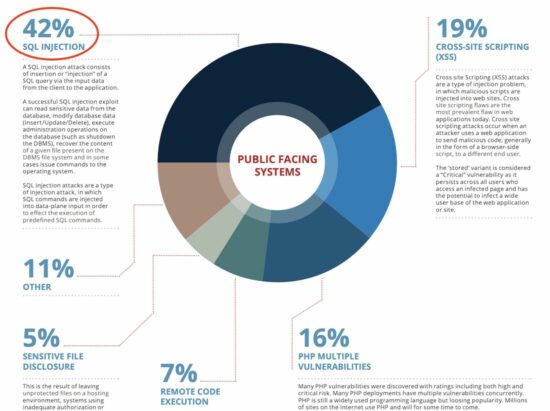
Image source
To mitigate this, APIs should be configured with common regular expressions that can be validated against incoming data. There are readily available Regex patterns that can match data containing SQL, HTML, and other injection syntaxes. It’s advisable to conduct a general validation on the incoming data using these patterns.
6. Masking and Encrypting Sensitive Data
As a general guideline, all confidential data should be either obscured (i.e., partially or entirely replaced with ***) or encrypted/tokenized. Information such as credit card numbers, bank account numbers, and national ID numbers are deemed sensitive personal data.
Every country has its own set of data protection regulations, such as PCI, HIPAA, GDPR, etc. It’s crucial for API gateways to ensure that they are not recording any such data in clear text in either debug or system logs. Additionally, to prevent misuse, OAuth2 tokens or API keys should not be logged in clear text.
7. Data Signature Verifications
Why do experts predict the exponential growth in the digital data signature market?
An incoming data in the payload or query needs to be thoroughly evaluated. We can never brush off a chance of a proxy server or an intermediate system between the client and the API layer, it opens up possibilities for a Man in the Middle (MITM) attack or other attacks that tamper with request data.
A client can easily create a signature of the request as a header or payload. With a shared key or a private key (the corresponding public key should be available to the server). The API gateway can then recreate the signature based on incoming data and verify if the newly generated signature matches the one in the request.
OWASP API Security Top 10 2023
While working with OWASP API security testing risks are bound to show up. Here are some common threats that you might come across:

Also Read: OWASP TOP 10
| Risk | Threat level | Detectability | Impacts |
| Broken Object Level Authorization | API endpoints vulnerable to broken object-level authorization can be exploited by attackers who manipulate the object’s ID within the request. | In certain situations, unauthorised individuals gaining access to the property of an object can result in a rise in privileges or the complete takeover of an account. | Under certain circumstances, unauthorised access to objects can also lead to a full account takeover. |
| Broken authentication | The authentication mechanism is an easy target for attackers as it’s exposed. | Prevalence: Common Detectability: Easy The misconceptions held by software and security engineers regarding authentication boundaries and implementation complexity contribute to the prevalence of authentication issues | Attackers are able to gain total control over other users’ accounts within the system, thereby accessing personal data and conducting sensitive actions on their behalf. |
| Broken object property level authorization | APIs generally expose endpoints that return all properties of an object. This is especially true for REST APIs. However, in the case of other protocols like GraphQL, it may be necessary to create specific requests to specify which properties should be returned. | Prevalence : Common Detectability : Easy You just need to inspect API responses to identify sensitive information in returned objects’. | APIs generally expose endpoints that return all properties of an object. This is especially true for REST APIs. However, in the case of other protocols like GraphQL, it may be necessary to create specific requests to specify which properties should be returned. |
| Unrestricted resource consumption | In API-based applications, the issue of inadequate server tracking of client states is widespread. Instead, these applications heavily rely on parameters like object IDs sent by clients to determine which objects to access. Fortunately, the server response generally provides enough information to gauge the success of a request. | Prevalence: Common Detectability: Easy It’s not uncommon to encounter APIs that fail to impose restrictions on client interactions or resource usage. By crafting API requests, such as those that include parameters dictating the quantity of resources to be returned, and conducting an analysis of response status, time, and length, one can identify potential issues. | The exploitation of these vulnerabilities can result in a Denial of Service (DoS) due to resource exhaustion. However, it can also cause an escalation in operational costs associated with infrastructure, such as increased CPU usage and expanded cloud storage requirements.. |
| Broken function level authorization | To exploit these vulnerabilities, an attacker would need to make valid API calls to an API endpoint that they shouldn’t have access to, either as anonymous users or regular users without special privileges. | Prevalence: Common Detectability : Easy The lack of or improper validation of such Uniform Resource Identifiers (URIs) are common issues. Regular API requests and response analysis will be necessary to detect the issue. When the response is not returned (Blind SSRF), detecting the vulnerability requires more effort and creativity. | Administrative functions are prime targets for these types of attacks and may result in data exposure, data loss, or data corruption. |
| Unrestricted Access to Sensitive Business Flows | Exploitation typically involves gaining an understanding of the business model supported by the API, identifying sensitive business processes, and automating access to these processes, which can cause harm to the business. | Prevalence: Widespread Detectability: Average Attackers manually determine which resources (e.g., endpoints) are involved in the target workflow and how they interact. If there are already mitigation mechanisms in place, attackers need to find a way around them. | Exploitation can harm the business in various ways, for instance, it can prevent legitimate users from buying a product or lead to inflation in a game’s internal economy. |
| Server Side Request Forgery | Generally, basic Server Side Request Forgery (SSRF), where the response is returned to the attacker, is easier to exploit than Blind SSRF, where the attacker receives no feedback on whether the attack was successful or not. | Prevalence: Common Detectability: Easy The lack of or improper validation of such Uniform Resource Identifiers (URIs) are common issue. Regular API requests and response analysis will be necessary to detect the issue. When the response is not returned (Blind SSRF), detecting the vulnerability requires more effort and creativity. | Successful exploitation might lead to enumeration of internal services (e.g., port scanning), disclosure of information, bypassing firewalls, or other security mechanisms. |
| Security Misconfiguration | Attackers often attempt to find unpatched vulnerabilities, common endpoints, services running with insecure default configurations, or unprotected files and directories to gain unauthorised access or knowledge of the system. | Prevalence : Widespread Detectability : Easy Security misconfiguration can occur at any level of the API stack, from the network level to the application level. Automated tools can be used to detect and exploit misconfigurations. | Security misconfigurations can lead to full server compromise. |
| Improper Inventory Management | Threat agents usually gain unauthorized access through old API versions or endpoints left running unpatched and using weaker security requirements. In some cases, exploits are available. Alternatively, they may gain access to sensitive data through a third party with whom there’s no reason to share data. | Prevalence : Widespread Detectability : Average Outdated documentation makes the process way harder to find and fix vulnerabilities. The lack of an assets inventory and retirement strategies leads to running unpatched systems, resulting in leakage of sensitive data. Unnecessarily exposed API hosts are common because of modern concepts like microservices. | Attackers can gain access to sensitive data easily. Sometimes Different API sometimes are connected with the same real data.Threat agents may exploit deprecated endpoints available in old API versions to gain access to administrative functions or exploit known vulnerabilities. |
| Unsafe Consumption of APIs | Exploiting this issue requires attackers to identify and potentially compromise other APIs/services that the target API integrates with. | Prevalence : Common Detectability : Average Lack of Vetting process to the data collected from third party APIs, compromising the data security due to insufficient security standards by them such as those regarding transport security, authentication/authorization, and input validation and sanitization. Attackers need to identify services that the target API integrates with (data sources) and potentially compromise them. | The target API determines the impact. Successful exploitation may lead to exposure of sensitive information to unauthorised actors, various kinds of injections, or denial of service.. |
API Security Tests to Run
Thorough set security tests are essential for detecting and addressing vulnerabilities in APIs. Knowing which API testing process to use is the first step in appropriately conducting API security testing.

Here are the primary API security test cases that should be carried out during API security testing
- Authentication and Authorization testing
- Input Validation testing
- Parameter Tampering testing
- Error Handling Testing
- Security Misconfiguration testing
- Rate Limiting and Throttling testing
- Session Management and Token testing
- Business Logic testing
- Third-Party Integration testing
- Compliance and Regulatory testing
Alright, it’s time to bring this to a close!
API security is absolutely an inevitable part of software development. It ensures that systems function seamlessly and that their interaction with APIs is intended or not. Learning the fundamentals is crucial before you deep dive into the complexities of API security testing. Understanding the various frameworks, strategies, and techniques involved, is essential.
Through this guide, you will get an overview of the world of API security testing. Bookmark this guide to confidently start the API security process. One thing to keep in mind is that it is not a one-time task; it’s a continuous process that requires consistent attention to keep your APIs secure and efficient. Engaging with API Penetration Testing Services India provides the continuous monitoring and testing needed to maintain a robust API security posture.









1 thought on “API Security Testing: A Comprehensive Guide [2025]”
Pingback: API Security Testing: A Comprehensive Guide [20...