Table of Contents
Toggle- What cybersecurity approach should UAE businesses choose in 2025?
- Recent UAE Cybersecurity Developments That Impact Your Decision
- What is VAPT and when should UAE businesses use it?
- How can UAE businesses benefit from VAPT’s structured approach?
- What are Bug Bounty programs and how do they work in the UAE?
- What Are The Crowdsourced Advantages For UAE Businesses?
- Comparing VAPT vs. Bug Bounty for UAE Businesses
- When shold UAE businesses choose VAPT?
- When should UAE businesses choose Bug Bounty programs?
- Can UAE businesses integrate VAPT with Bug Bounty
- Integrated Approach Benefits
- How to choose the right cybersecurity approach for your UAE business?
- Expert insights on UAE cybersecurity strategy integration
- Current UAE Cybersecurity Market Trends
- Helping You Decide Between VAPT And Bug Bounty
- The Optimal UAE Cybersecurity Strategy
- Bug Bounty vs VAPT FAQs
What cybersecurity approach should UAE businesses choose in 2025?
The rapidly evolving digital landscape of the modern world places UAE businesses at unprecedented and sophisticated cyber threats. According to the State of the UAE Cybersecurity Report 2025, 21% of cybersecurity incidents targeted banks and financial services in the region, while ransomware attacks in the UAE increased 32% year-over-year in 2024. As cybersecurity experts warn, the question isn’t whether your UAE business will be targeted it’s when.
With the UAE’s cybersecurity market growing at a CAGR of 16.4% from 2020 to 2025 and the nation advancing its digital transformation goals under the UAE Centennial 2071 plan, businesses must make critical decisions about their cybersecurity strategies.
In light of these facts, the conversation drifts to two prominent approaches – VAPT (Vulnerability Assessment and Penetration Testing) and Bug Bounty programs.
But which one does your UAE business genuinely need? This is up for discussion.
Recent UAE Cybersecurity Developments That Impact Your Decision
• Latest National Bug Bounty Program Launch
In January 2025, the UAE Cybersecurity Council launched the ‘National Bug Bounty Program‘, to promote cybersecurity culture and protect the country’s digital transformation efforts and achievements. A move like this documents the government’s commitment to adopting crowdsourced security testing, opening new opportunities for UAE businesses to leverage bug bounty programs.
Additionally, in January 2025, the UAE Cybersecurity Council partnered with du and brought in 100 international ethical hackers as part of the GISEC Bug Bounty Program. This event showcased the growing regional acceptance of crowdsourced security testing.
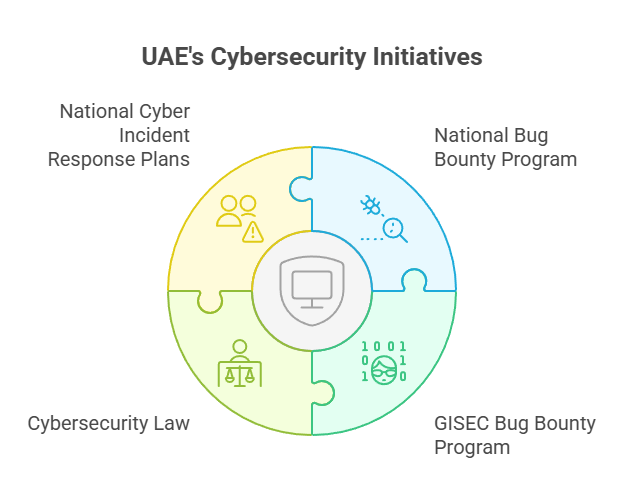
• Evolving Regulatory Framework
The UAE’s cybersecurity law has established a comprehensive legal framework to address concerns regarding the abuse and misuse of online technologies. An initiative like this is meant to strengthen security efforts and prevent online crimes committed through information technology networks and platforms. The UAE Cybersecurity Council continues to develop legal and regulatory frameworks covering all types of cybercrimes to establish robust ‘National Cyber Incident Response Plans‘.
What is VAPT and when should UAE businesses use it?
What exactly is VAPT?
VAPT (Vulnerability Assessment and Penetration Testing) is a systematic and methodical approach to cybersecurity evaluation. Both automated vulnerability scanning and manual penetration testing are involved here to ensure proper identification, assessment, and mitigation of security vulnerabilities. In the end, you derive optimal security for your digital infrastructure.
How can VAPT secure UAE businesses?
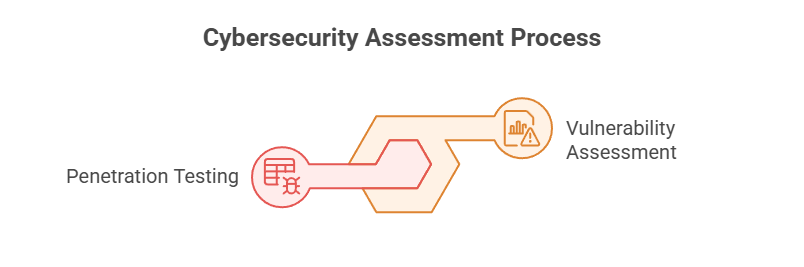
Through a comprehensive security testing methodology, VAPT embodies two complementary components.
- Vulnerability Assessment: This is the stage where you identify known vulnerabilities followed by creating a comprehensive inventory (detailed list) of detected security weaknesses, noting down their potential severity and impact.
- Penetration Testing: Exclusively entails ethical hackers, who can efficiently simulate real-world attack scenarios when exploiting identified vulnerabilities, albeit in a controlled environment.
How can UAE businesses benefit from VAPT’s structured approach?
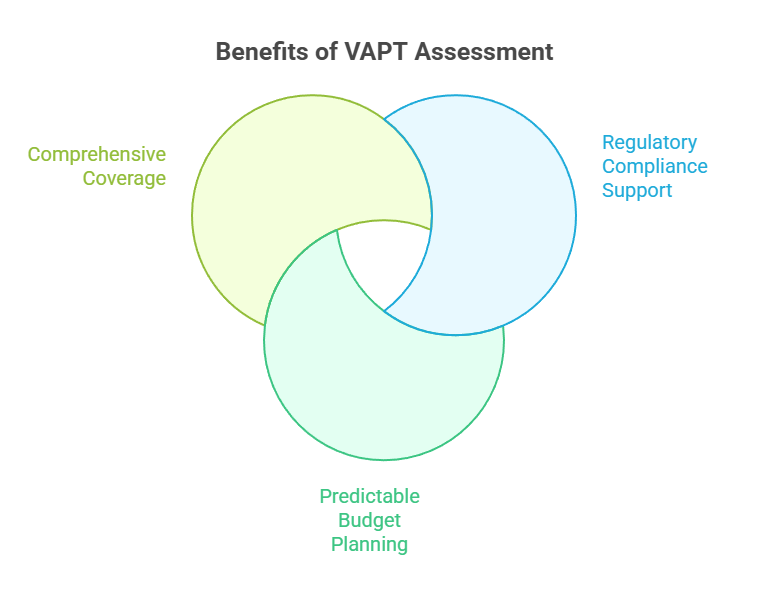
Businesses operating in the UAE derive several compelling advantages through VAPT assessment.
- Regulatory Compliance Support: In offering a structured approach to enhancing security for organizations, VAPT assessment helps the latter demonstrate due diligence in their cybersecurity efforts. Offering compliance support with UAE’s evolving cybersecurity regulations is one of the prime objectives of the VAPT assessment.
- Predictable Budget Planning: Fixed timelines and scoping make budget planning straightforward. When combined with detailed reports, these offer actionable remediation guidance.
- Comprehensive Coverage: A systematic approach offers a thorough examination of digital assets. Extremely beneficial for industries facing strict regulations, like banking, healthcare, and government sectors.
What are Bug Bounty programs and how do they work in the UAE?
What is a Bug Bounty program?
Bug bounty programs are a way for organizations to reward ethical hackers and security researchers—through cash or recognition—for responsibly finding and reporting vulnerabilities in their systems and apps.
In short, Bug Bounty suggests a fundamentally different approach to cybersecurity that leverages the collective expertise of global security researchers.
Why are Bug Bounty programs gaining popularity in the UAE?
Bug Bounty programs have gained significant popularity in the UAE owing to:
- Emphasis placed on innovation and digital transformation.
- Cybersecurity threat awareness.
- Cost-effectiveness associated with crowdsourced security testing.
It’s the continuous security testing that the Bug Bounty programs allow by adopting diverse perspectives that makes them stand apart from the traditional security assessment approaches.
Security researchers from around the world examine your systems by using varied methodologies, tools, and attack vectors. You gain a more comprehensive security assessment – something that internal teams or traditional VAPT assessments tend to miss.
What Are The Crowdsourced Advantages For UAE Businesses?
In case as a business operating in the UAE, you are adopting crowdsourced security testing services, say the Bug Bounty program, you’ll derive advantages that will also prove valuable for you in:
- Edge-case vulnerability discovery: Uncovering unique attack patterns and novel exploitation techniques.
- Continuous security validation: Bug Bounty’s ongoing vulnerability detection and prevention capabilities help ward off new threats as they emerge when systems evolve.
- Access to global expertise: If you are a UAE business entity and are constantly seeking ongoing security services from the worldwide security research community, you’re likely to gain access to global expertise.
The UAE Cybersecurity Council’s National Bug Bounty Programme aims to protect its vital infrastructure at the highest level possible. A move of this kind will help create momentum for private-sector adoption of the Bug Bounty Programme.
Local businesses can leverage this growing ecosystem and contribute to the UAE’s overall cybersecurity posture. They should, however, ensure that their efforts align with the Cyber Security Council’s vision to protect UAE cyberspace, maintain confidence in digital infrastructure, and build a cyber-resilient society.
Comparing VAPT vs. Bug Bounty for UAE Businesses
Spotting the key differences between VAPT and Bug Bounty programs
| Aspect | VAPT | Bug Bounty |
| Timeline | Fixed duration (2-8 weeks) | Continuous/ongoing |
| Cost Structure | Predictable, upfront investment | Variable, pay-per-vulnerability |
| Coverage | Comprehensive, systematic | Unpredictable, researcher-dependent |
| Expertise | Professional security firms | Global researcher community |
| UAE Compliance | Structured reporting for regulations | Supplementary evidence |
| Scope Control | Precisely defined boundaries | Potentially broader, harder to control |
| Local Support | UAE-based security firms available | Growing regional researcher pool |
When shold UAE businesses choose VAPT?
VAPT will effectively work in instances that:
- Regulatory compliance needs for organizations requiring structured documentation to adhere to UAE cybersecurity regulations.
- System implementations, such as new digital infrastructure, applications, etc.
- Budget-conscious organizations seeking a predictable security investment plan.
- Highly regulated industries, such as financial services, healthcare, and government entities.
When should UAE businesses choose Bug Bounty programs?
Bug Bounty programs apply in scenarios that include:
- Mature security programs: Organizations possessing established incident response capabilities.
- Public-facing applications: Companies operating websites, mobile apps, or customer portals.
- Continuous security validation: Businesses wanting ongoing security testing as systems evolve.
- Innovation-focused companies: Organizations seeking cutting-edge vulnerability discovery.
Can UAE businesses integrate VAPT with Bug Bounty
– Is it possible to use both VAPT and Bug Bounty programs together?
Absolutely. Rather than viewing VAPT and Bug Bounty programs as competing alternatives, forward-thinking UAE businesses are discovering the power of integration. This dual approach leverages the structured thoroughness of VAPT with the innovative discovery capabilities of Bug Bounty programs.
Integrated Approach Benefits
– What are the advantages of combining both approaches?
When you integrate VAPT into Bug Bounty, you derive several synergistic benefits, especially in terms of:
- Comprehensive baseline establishment: VAPT provides systematic vulnerability identification and compliance documentation.
- Continuous innovative discovery: Bug Bounty programs help identify novel threats and edge-case vulnerabilities.
- Regulatory compliance: Structured VAPT documentation helps comply with UAE cybersecurity requirements.
- Ongoing validation: Bug Bounty discoveries help deliver continuous security improvement.
– How should UAE businesses implement an integrated approach?
The most effective implementation strategy for integrating Bug Bounty into VAPT involves various stages:
- Start with VAPT: Establish a comprehensive security baseline by addressing fundamental vulnerabilities.
- Document compliance: Create and utilize VAPT reports to ensure regulatory compliance.
- Launch targeted Bug Bounty: Focus on specific applications or services after VAPT remediation.
- Maintain continuous cycle: Combine regular VAPT assessments with ongoing Bug Bounty programs.
How to choose the right cybersecurity approach for your UAE business?
What factors should UAE businesses consider when choosing between VAPT and Bug Bounty?
Considering the below-mentioned criteria will help you decide whether your business needs VAPT or Bug Bounty, or even both.
Business size and maturity considerations
Small to Medium UAE Enterprises:
• Start with VAPT to establish fundamental security baselines.
• Address obvious vulnerabilities with clear remediation guidance.
• Consider Bug Bounty programs after achieving security maturity.
Also Read : A Guide To PlayStation Bug Bounty Program: Unlocking the Secrets
Large UAE Enterprises:
• May benefit from Bug Bounty programs for sophisticated threat discovery.
• Require structured VAPT for maintaining compliance with innovative Bug Bounty to support ongoing validation.
• Require both approaches for comprehensive security coverage.
Industry-specific requirements in the UAE
Financial Services & Banking:
• VAPT essential for regulatory compliance documentation.
• Bug Bounty valuable for discovering sophisticated financial crime techniques.
• Both approaches recommended for comprehensive protection.
Healthcare Organizations:
• VAPT critical for meeting patient data protection compliance.
• Bug Bounty useful for identifying application-layer vulnerabilities in patient systems.
Government Entities:
VAPT is mandatory for systematic security assessment.
Bug Bounty programs align with national cybersecurity initiatives.
Technology & E-commerce:
Bug Bounty programs are particularly valuable for public-facing applications.
VAPT is essential for establishing infrastructure security baseline.
Expert insights on UAE cybersecurity strategy integration
According to cybersecurity professionals operating in the UAE market, combining structured vulnerability assessments with crowdsourced security testing helps build a highly comprehensive security strategy. While a systematic approach with VAPT assists in addressing known vulnerabilities and meeting compliance requirements, Bug Bounty programs help identify unforeseen threats through diverse researcher perspectives.
Also Read : All About Bug Bounty Hunting
This integrated perspective aligns with the UAE’s national cybersecurity vision and demonstrates the value of viewing these approaches as complementary rather than competitive, particularly for businesses operating in the dynamic UAE digital economy.
Current UAE Cybersecurity Market Trends
What trends shape UAE Cybersecurity in 2025?
Several key trends are influencing UAE cybersecurity decisions:
- Increased government support: The National Bug Bounty Program launched by the UAE Cybersecurity Council in 2021 shows its commitment to fostering innovative security approaches.
- Growing regional expertise: The UAE showcases an expanding pool of local cybersecurity professionals and ethical hackers.
- Rising threat sophistication: A 32% increase in ransomware attacks YOY (year-on-year) requires more comprehensive security strategies implementation.
- Digital transformation acceleration: UAE businesses are increasingly adopting cloud and digital services, which mandate ongoing security validation.
Helping You Decide Between VAPT And Bug Bounty
The choice between Bug Bounty programs and VAPT is more strategic than binary. Keeping this fact in view, the UAE businesses can effectively decide which to choose. Also, they need to understand the unique needs of their business operations. Considering parameters like regulatory requirements, resource availability, and risk tolerance when adopting a cybersecurity approach will help them speed up their decision-making in this regard.
The Optimal UAE Cybersecurity Strategy
For most UAE organizations, the optimal strategy involves:
- Foundation building: Leverage VAPT’s systematic approach to establish security baselines and ensure compliance.
- Continuous innovation: Incorporate Bug Bounty programs to derive ongoing discovery and validation capabilities.
- Regulatory alignment: Ensure that chosen approaches comply with the UAE cybersecurity Law.
- Resource optimization: Balance security investment with business operational requirements.
An integrated approach that fulfils the above requirements can align with the UAE Centennial 2071 objectives to attain cybersecurity excellence. Efforts like these can provide the flexibility to adapt and tackle evolving threats
As cyber threats continue to evolve and the UAE’s digital economy expands, businesses that embrace comprehensive security strategies by combining multiple approaches will be better positioned to protect their assets and build customer trust, also in contributing to the nation’s digital transformation goals.
The National Bug Bounty Program launched in proximity to the growing cybersecurity market in the UAE creates new opportunities for businesses to enhance their security posture by adopting innovative approaches. These developments though equally consider maintaining compliance with local regulations.
Ready to develop a cybersecurity strategy tailored to your UAE business needs?
Visit our penetration testing services in the UAE webpage of Wattlecorp to learn how VAPT, Bug Bounty programs, or an integrated approach can strengthen your security posture and help ensure compliance with UAE’s cybersecurity requirements. Our team is well aware of the local regulatory landscape and can help you effectively navigate the complex landscape of cybersecurity regulations your business may face in the UAE, going forward.
Having established a good rapport and trust with the clients we served, our success is that which reflects theirs. How? Through our qualified cybersecurity professionals’ capability, knowledge, and expertise – tested and verified by the organisations that we’ve served to date.
Still confused about the right security approach for your business? Connect and allow us to make this choice for you.
Schedule a Free Consultation and Let’s Help You Ace Your Security Journey!
Bug Bounty vs VAPT FAQs
1. What cybersecurity regulations do UAE businesses need to comply with in 2025?
UAE businesses must duly comply with the comprehensive cybersecurity law framework to prevent abuse and misuse of online technology. Additionally, there are sector-specific regulations that banking, healthcare, and government organizations should adhere to.
2. How much do VAPT services cost for UAE businesses in 2025?
VAPT costs in the UAE typically range between AED 15,000 and AED 150,000. However, these are determined by the scope, system complexity, and assessment duration.
3. Should UAE startups choose VAPT or Bug Bounty programs first?
For UAE startups, it’s wise to begin with VAPT to establish fundamental security baselines – also addressing obvious vulnerabilities. VAPT is a structured approach that offers clear remediation guidance without exhausting limited security resources. Bug Bounty programs can be introduced later as your startup grows – in security maturity and resources.
4. Are Bug Bounty programs suitable for UAE government entities?
Yes, they do. The UAE Cybersecurity Council’s National Bug Bounty Program demonstrates the nation’s commitment to promoting crowdsourced security testing. Many government.