The growth in SaaS adoption has increased SaaS security concerns. With these, SaaS companies face unique security challenges that mostly go unnoticed.
Performing a comprehensive SaaS Risk Assessment is highly essential to identify, mitigate, and eliminate the biggest SaaS risks and further enhance data protection and compliance status.
In this blog, we’ll discuss SaaS security concerns that are often overlooked and explore the security gaps that can put SaaS organisations at risk.
Table of Contents
Toggle- SaaS Security Challenges: Avoiding Common Pitfalls
- The Biggest SaaS Security Gaps That SaaS Companies Often Overlook
- Staying Ahead of Security Gaps in SaaS with Effective Risk Management
- Overcoming Cloud Compliance Challenges To Level Up SaaS Security
- Proactive SaaS Risk Assessment for Stronger Security
- SaaS Risk Assessment FAQs
SaaS Security Challenges: Avoiding Common Pitfalls
SaaS companies face innumerable security challenges. These range from safeguarding customer data to ensuring compliance with evolving regulations.Amid the pressing security concerns that challenge SaaS businesses, there also exist the most common ones. These when overlooked or ignored can significantly widen the security gap.Some of the common pitfalls have been discussed below:
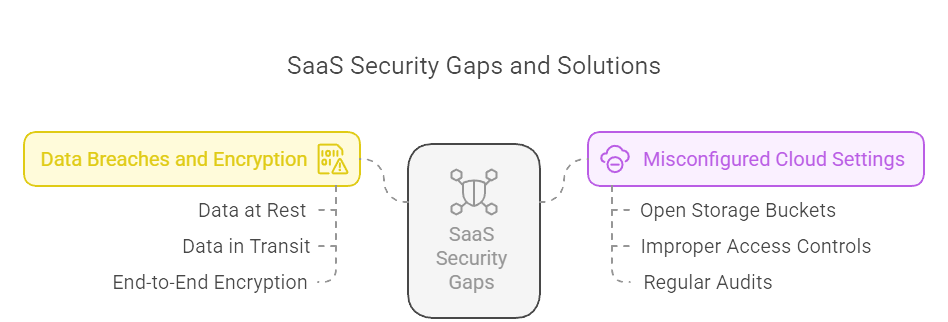
1. Data Breaches and Insufficient Encryption
If you don’t encrypt your sensitive data appropriately, it will become highly vulnerable to interception – both during storage and transmission.A significant portion of SaaS security gaps can be attributed to the failure to implement strong encryption for data at rest and in transit.To emphasise, if you are a SaaS business, you should implement end-to-end encryption. At the same time, securely storing the associated encryption keys can well guarantee user data protection.
2. Misconfigured Cloud Settings
The tendency of SaaS providers to rely on cloud infrastructure for scalability and flexibility puts SaaS platforms at increased risk for exposure to misconfigured settings.Common scenarios include open storage buckets and improperly applied access controls inviting unauthorised access to sensitive data. Regularly auditing cloud environments can help close these SaaS platform data security gaps.
3. Weak Access Control and Authentication Protocols
If you do not implement proper or adequate access controls and authentication protocols for your SaaS platforms, these will get exposed to both insider threats and external attacks.You also need to enforce sufficient identity management and Multi-Factor Authentication (MFA) for your critical systems and data. Failing to do so can invite unauthorised access.
4. Weak API Security
Application Programming Interfaces (APIs) are fundamental to SaaS service offerings. This is because they allow different software applications and services to seamlessly connect and exchange data with each other.Inadequately secured APIs are a sure-shot way for cybercriminals to attack.As a SaaS business, you are bound to ensure adequate testing of APIs to identify security gaps. Engaging in these efforts are vital to protecting them against common vulnerabilities, including injection attacks.
The Biggest SaaS Security Gaps That SaaS Companies Often Overlook
It is a common occurrence, where many SaaS providers miss out on some of the biggest SaaS risks while they are busy focusing on basic security measures.However, the more commonly these occur, the higher the chances for the associated security gaps to become wider. If you fail to address them, they can bring forth significant legal repercussions, financial loss, and reputational damage – both for your organisation and the clients/customers relying on you.Let’s now look into some of the biggest SaaS security gaps that are often ignored.
Also Read : Server Hardening: The Backbone of SaaS Security
1. Lacking Comprehensive Incident Response Plans
It is disappointing to note that a well-defined incident response plan is often overlooked or at the most, underestimated in SaaS security.If you don’t have an adequate strategy in place, it will not only bring forth data breaches, but will also lead to extended downtimes, data loss, and reputational damage.What you need to do is to prioritise prompt detection of security issues, containment, communication, and devising proper remediation measures to effectuate incident response plan.
2. Insufficient Security for Multi-Tenant Environments
Many SaaS platforms operate in multi-tenant environments, where multiple customers share the same infrastructure.As a SaaS company, you should set up proper security isolation between yourself and other tenants to avoid data leakage and direct access to your customer’s data. This will help you ensure secure isolation in multi-tenant architecture and proper segmentation, which are crucial to mitigating risks.
3. Inadequate Employee Training and Awareness
Regular employee training and awareness programs are crucial to avert major security vulnerabilities happening due to human error.Most SaaS companies fail to provide adequate or proper cybersecurity training to their employees. No matter the reason, inadequate training and awareness programs do pile up security risks.Employees, especially in client-facing roles, should be regularly and promptly educated regarding phishing attacks, social engineering, and proper data handling procedures.
Also Read: Why Your SaaS Business Needs an Annual Security Program
Staying Ahead of Security Gaps in SaaS with Effective Risk Management
To address these SaaS security gaps and strengthen security, SaaS companies must adopt a comprehensive risk management strategy.Following are the strategic options that you can consider to boost your SaaS security:
1. Adopt A Zero-Trust Security Model
The zero-trust model is core to the ‘never trust, always verify’ principle. It aims to ensure proper authentication and authorisation when accessing sensitive data.The Zero-Trust Security Model applies to all users inside and outside an organisation’s network perimeter.The zero-trust architecture optimally reduces the risk of internal threats and unauthorised access.
2. Continuous Monitoring and Penetration Testing
Penetration testing adds a layer of protection for SaaS. By facilitating comprehensive scanning as a proactive measure, penetration testing saves SaaS applications from potential exploitation by cyber thefts . By continuously monitoring your SaaS platform for unusual activity, you can detect potential threats early. Penetration testing (or ethical hacking) is another essential tool for identifying vulnerabilities before attackers can exploit them.Regular testing ensures your defenses stay up-to-date and resilient to new threats.
3. Automate Compliance and Security Audits
Automated compliance reporting and security audits help reduce human error to a significant extent. Compliance with industry regulations is, therefore, guaranteed through this.Automation for your SaaS businesses helps you stay updated on evolving cloud compliance challenges and regulations, including GDPR, HIPAA, and SOC 2.Automation exclusively supports real-time monitoring and adaptation.
4. Invest in Security Awareness Programs
Regular training programs on cybersecurity protocols, phishing prevention, and safe data handling are critical to minimising human error.Educating your employees about SaaS security risks and security best practices carries its own benefits when it comes to reducing vulnerabilities.
Overcoming Cloud Compliance Challenges To Level Up SaaS Security
Cloud compliance challenges are as complex and ever-evolving for SaaS companies as it does for any other organisation.If you fail to adhere to data privacy regulations, you are at significant risk of data breaches. Paying hefty fines, facing reputational damage, and loss of customer trust are the potential causes.Here are a few suggestions you can consider to help you overcome the various challenges associated with meeting cloud compliance requirements.
1. Implement Robust Data Protection Measures
In order to protect your sensitive data, you need to implement robust data protection measures in all its worth. Be it offering SaaS solutions or any other services on cloud, every business is meant to adopt security practices that are best in the industry. Here’s a quick breakdown of the benefits you can derive with undertaking strong data protection measures:
Prevent Unmanaged Third-Party Access and Data Exposure: Helps ensure regulatory compliance through data encryption and inputting secure access controls.
Conduct Regular Security Audits: Can effectively avoid shadow IT and remove obsolete security measures.
2. Use Third-Party Security Certifications
Partnering with third-party auditors to certify your platform through industry-recognized standards is a significant way to reassure your customers.It also signals existing regulatory bodies that your platform is secure and compliant. ISO 27001, SOC 2, CSA STAR, HIPAA, and PCI DSS are some of the most recognised third-party security certifications for SaaS companies.
3. Stay Updated on Legal Requirements
Regulatory requirements are evolving constantly. Staying up to date on relevant laws and adopting best practices for compliance ensures that your SaaS company can avoid penalties and maintain trust with your users.

Proactive SaaS Risk Assessment for Stronger Security
Proactive SaaS Risk assessment is essential for detecting and closing potential security gaps within your SaaS applications.By assessing and mitigating security vulnerabilities, proactive risk assessments for SaaS also involve managing associated risks in all efficiency and efficacy.Through ensuring strong cloud compliance and adopting best practices for SaaS risk management, you can safeguard your platforms, protect customer data, and maintain regulatory compliance.
SaaS Risk Assessments are pivotal to addressing and prioritising common SaaS security concerns before they become highly and complicatedly vulnerable.Implementing the aforementioned and discussed security measures can significantly close security gaps within SaaS applications.At Wattlecorp, our team of vibrant, knowledgeable and certified VAPT professionals can expertly detect, assess, prioritise, and mitigate potential security vulnerabilities that may threaten your business regardless of their nature.
From conducting risk assessments to helping you achieve regulatory compliance, we offer customised solutions for the type and extent of protection your business needs.We also offer Cyber risk management for SaaS through our dedicated and 24/7 active cybersecurity team. In understanding the increasing security concerns underlying SaaS applications and services, our SaaS security assessment services intend to offer you fool-proof solutions as part of our annual security program.So, do not hesitate. Call us or visit our website to Book a Free Consultation and we’ll deploy our dedicated cybersecurity team at your service instantly.Let this be the start of your new and worry-free SaaS Security journey with us!
SaaS Risk Assessment FAQs
1. What are the risks associated with misconfigured cloud settings?
Misconfigured cloud settings come with a bundle of risks. Some of these include sensitive data exposure to unauthorised access and resultant data breaches (as in open storage buckets and improperly applied access controls).Regular audits and configuration reviews can help mitigate these risks and enhance the security posture for cloud-based SaaS applications.
2. How can continuous monitoring and penetration testing improve SaaS security?
Employing automated tools guided by human intervention to facilitate real-time monitoring, also assessing security vulnerabilities by undertaking mock cyber attacks, certified VAPT professionals can gauge the possibility of malicious intrusion.The above processes and associated tools help mitigate potential security vulnerabilities before they can be exploited and attacked, thus improving security posture for SaaS.
3. What is a zero-trust security model?
A zero-trust security model operates on the principle of “never trust, always verify.” It requires all users and devices to be authenticated and authorised before accessing sensitive data. This practice significantly helps reduce the risk of internal threats and unauthorised access.