All about Brute Force Attacks

A common technique used by cybercriminals to gain unauthorized access into user profiles is brute force attacks. It is a well-known technique not just among ethical hackers, but also among knowledgeable people outside the field. But what is brute force?
What are Brute Force Attacks?
The basic form of brute force attacks is checking a large list of usernames and passwords to get the right combination of lists and usernames. This is done by cross-checking both entries to find the right one. These days, cybercriminals gather a huge amount of information about the target and create a wordlist using that information. The process has been automated using these methods.
In web applications, brute force attacks are used to find hidden pages within a website or application. This is done by creating a wordlist of the known pages and then attacking the authentication.
Tools and Techniques for Brute Force
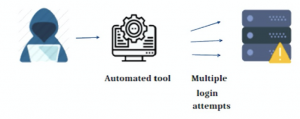
While brute force refers to the mode of attack that gains unauthorized access, that isn’t the technique or tool used for the same. There are different tools and techniques used for brute force attacks.
The different types of brute force attacks depend on the way it does repeat checking for passwords. Some of the common brute force attack mechanisms include Dictionary Attacks
, Rainbow Table Attacks, and Credential Stuffing. Dictionary attacks refer to the creation of a wordlist and then checks individually from the list, also known as a dictionary to find the right one.
Read More about Top 3 Steganography Tools
A Rainbow Table Attack finds the hash function corresponding to the password with the target user and then is used to access the database. The most common type of attack is called Credential Stuffing. Credential Stuffing finds the right username and password which is available based on data breaches that had happened on the dark web. The lesser amounts of time consumption and increasing success rate make Credential Stuffing reliable software.
Just like the technique used for brute force, there are a few tools as well. Some of the well-known brute force tools include THC-Hydra, John the Ripper, and Aircrack-ng. THC-Hydra is well known due to its simplistic nature and ability to brute-force more than 50 protocols across multiple operating systems. The ability of John the Ripper to detect and dynamically play across different websites makes it a good addition. Another good tool used for WiFi password cracking is Aircrack-ng which is a packet sniffer used in networking. Another example of a tool in brute force is Dirbuster, specializes in web application attacks.
Eviction and Avoiding
Brute force attacks can be easily identified with frequent monitoring of the logs. In cases where multiple failed login attempts are detected by the presence of multiple failed logins from the same IP address. Login attempts with multiple username attempts from the same IP address point to the same. These are all examples of situations where brute force attacks have taken place.
While there are no surefire ways to get rid of brute force attacks, there are possibilities to reduce the attempts and make it difficult for such attacks to be successfully done. The best bet is to create a complex password for your accounts so it gets difficult to obtain. Another way is to create different passwords for different accounts. In cases where you have only one password, cybercriminals have instant access all others once one of them is logged in. Using Recaptcha helps in avoiding multiple login attempts.
Read More about How to Create a Strong Password
Contributors: Sherin Saji, Labeeb Ajmal