With more and more businesses in the modern era becoming reliant on digitalization with technological innovations, this tendency has put the CTOs and founders of SaaS under significant stress due to security concerns owing to the former’s use of SaaS (Software-as-a-Service) applications.
The extent to which we hear about incidents of data breaches, service interruptions, trouble with managing sensitive customer data, and many other things concerned, question our immunity to the risks of cyber threats and attacks.
As if these are not enough, there may ensue interruptions to vital company operations for businesses reliant on SaaS solutions. Scenarios such as these critically warrant a proactive approach to utilizing cutting-edge SaaS Security Testing Tools and solutions in the coming years.
Wattlecorp as a cybersecurity service provider has realized the extent of the urgency to safeguard relevant software applications of its clients – that of the SaaS entrepreneurs given the critical nature of SaaS security testing.
Additionally, as far as guaranteeing compliance matters in the event of increasing cyber threats, Wattlecorp professionals consider it their obligation to assist SaaS entrepreneurs in effectively integrating SaaS Security Testing tools and techniques by 2025.
This blog examines the best SaaS security testing tools and techniques that CTOs can consider in 2025, which will result in creating a safe, reliable, and compliant SaaS ecosystem.
Table of Contents
ToggleSaaS Security: Scoping The Significance
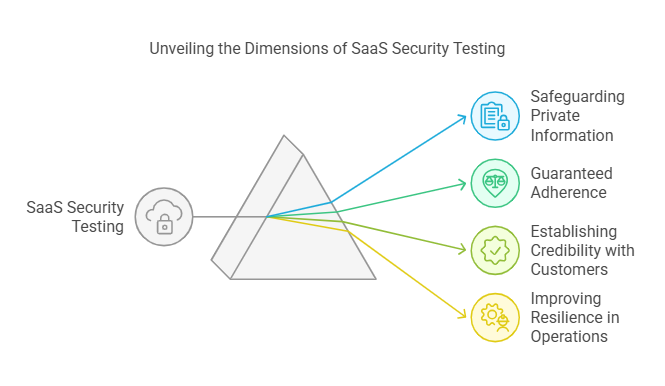
From ensuring quality to acquiring the ability to function appropriately and efficiently across different business environments, these criteria significantly stress the significance of undertaking SaaS Security Testing in all its effectiveness.
- Safeguarding Private Information: Cloud-based SaaS platforms store and process large chunks of sensitive data. Doing so places them at increased risk of data breach with resultant monetary losses due to legal repercussions, and eroded consumer trust. By adopting the best technologies and practices for SaaS security testing and ensuring these meet compliance standards, SaaS companies can strengthen their data protection efforts, thus minimizing the occurrences of breaches.
- Guaranteed Adherence
Complying with regulation is typically mandated by businesses seeking to avoid backlash and ensure that their corporate actions are legalized. Compliance comes along with some monitoring not just to the company itself but equally to its policymakers in order to check on things such as GDPR, HIPAA, and SOC2 based rules and so on. - Establishing Credibility with Customers
It is needless to point out here that customers exhibit more confidence when they start utilizing a secure platform. This tendency essentially necessitates SaaS entrepreneurs to incorporate SaaS security testing tools and techniques to acquire a dependable and trustworthy SaaS application. - Improving Resilience in Operations
The chances of security risks for contemporary SaaS apps functioning in dynamic business settings are high, especially when making regular modifications.
A logical implication is to carry out regular security testing for SaaS applications by leveraging effective and secure technologies. While this process helps minimize inherent security risks, it can also effectively guarantee seamless operations.
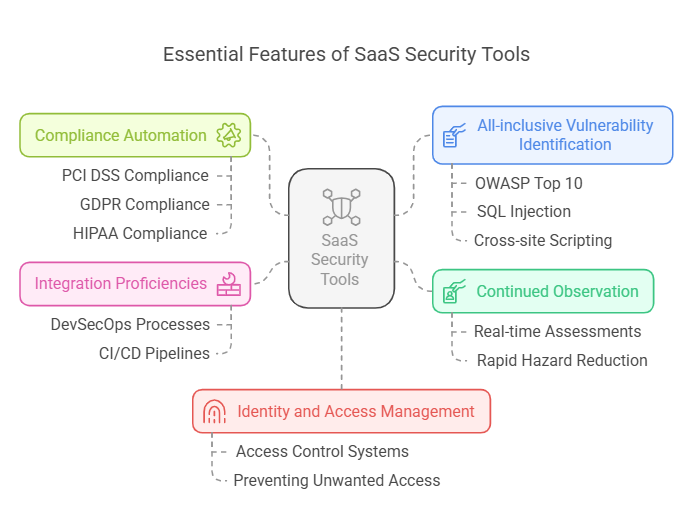
Key Features of SaaS Security Tools
The available SaaS Security Tools are expected to embed the following features to optimally secure SaaS platforms:
- Continued Observation: Mandates real-time assessments to identify security vulnerabilities and facilitate rapid hazard reduction.
- Compliance Automation: Necessitates making automated assessments for regulatory adherence to PCI DSS, GDPR, and HIPAA.
- Integration Proficiencies: Ensuring smooth integration with DevSecOps processes and CI/CD pipelines for automated security testing.
- Promoting All-inclusive Vulnerability Identification: Examples of highly prevalent vulnerabilities that can be identified through SaaS security testing are likely to include OWASP’s Top 10 vulnerabilities, such as SQL injection and cross-site scripting (XSS).
- Identity and Access Management: Preventing unwanted access to protect sensitive user information by reinforcing access control systems.
Top 10 SaaS Security Testing Tools For CTOs To Evaluate in 2025
Whether you are a SaaS entrepreneur or a CTO, you are expected to utilize the essential security tools to improve the security posture of your SaaS operations. To this end, the following security tools have been testified and listed by Wattlecorp cybersecurity professionals:
1. Burp Suite
One of the top security tools that helps find web application vulnerabilities, Burp Suite is adept at identifying threats like SQL injection, cross-site scripting, and configuration errors.
Vital Features
- Helps conduct traffic inspection and interception on a real-time basis.
- Efficiently combines automated vulnerability detection with manual testing alternatives.
- Promotes in-depth reporting for efficient vulnerability detection and management.
Why It Matters?
Burp Suite being a vital tool is also versatile and easy to use by being adept at detecting vulnerabilities during the development phase of SaaS applications.
2. Zed Attack Proxy or OWASP ZAP
By facilitating continuous testing of web interfaces, Zed Attack Proxy/OWASP ZAP – an open-source penetration testing tool, ensures a perfect base for SaaS setups.
Vital Features
- Scans for vulnerabilities on a passive yet automatic note.
- Effectively integrates CI/CD pipeline for ongoing security testing.
- Possesses adaptable detection features.
Why It Matters?
- Functions in coherence with the founders’ requirements for SaaS security.
- OWASP ZAP also offers an affordable yet efficient solution for protecting web-based SaaS applications.
Also Read: Future-Proofing SaaS Security: The Role of an Annual Security Program
3. Veracode
A cloud-based platform that helps provide software composition analysis (SCA), dynamic analysis (DAST), and static analysis (SAST) to find vulnerabilities early in the development lifecycle.
Vital Features
- Checks for vulnerabilities in runtime environments and codebases.
- Incorporates automated scanning into DevSecOps processes.
- Offers backing for important regulatory requirements and compliance with necessary standards.
Why It Matters?
Veracode guarantees adherence to SaaS compliance and security testing tools, thereby assisting CTOs in addressing security concerns before deployment.
4. Nessus
A most preferred tool for vulnerability detection and compliance tests that can also handle security requirements of SaaS applications and infrastructure.
Vital Features
- Thoroughly scans for existing vulnerabilities with detailed reports and documentation and recommendations for fixing them.
- Helps undertake HIPAA, PCI DSS, and GDPR compliance tests.
- Detects obsolete parts and configuration errors.
Why Is It Important?
Nessus is a top option for CTOs because it guarantees that your SaaS applications and infrastructure are free from serious security risks.
5. Qualys
Being a cloud-native security technology, Qualys perfectly aligns with multi-cloud SaaS setups to provide continuous vulnerability detection and management.
Vital Features
- Conducts vulnerability scans in real time using threat intelligence.
- Facilitates automated checks for policy compliance.
- Provides API assistance for smooth integrations.
Why It Matters?
Qualys helps streamline vulnerability management and compliance for SaaS apps running in intricate cloud infrastructures.
6. Checkmarx
Checkmarx identifies vulnerabilities in the early phase of the development process of a SaaS application, also specializing in static-application security testing.
Vital Features
- Helps analyze static code for security threats.
- Effectively integrates with IDEs and CI/CD workflows.
- Supports a variety of programming languages.
Why It Is Important?
By incorporating security into the development process, Checkmarx keeps vulnerabilities out of production.
7. Tenable.io
Also a cloud-native vulnerability management system like Qualys, Tenable.io casts an intuitive eye for security flaws and noncompliance in SaaS apps.
Vital Features
- Provides vulnerability assessments in real-time.
- Effectively interacts with threat intelligence feeds.
- Offers comprehensive reports to monitor compliance.
Why Is It Important?
- As a highly effective SaaS security testing tool, Tenable.io scrupulously manages vulnerabilities upon detection.
- Additionally, for its comprehensive asset discovery ability, combined with its deep vulnerability scanning capabilities, and many more, including user-friendly dashboards, makes security posture assessment of your SaaS platform easy and time-saving.
- Tenable.io’s compatibility with SaaS platform security testing tools is a feature you cannot miss as a SaaS entrepreneur or CTO.
8. Snyk
A developer-focused tool, Snyk is especially helpful for SaaS applications by effectively scanning, prioritizing, and fixing vulnerabilities in source codes, open-source dependencies, infrastructure, and container images.
Key Strengths:
- A highly effective SaaS Security Testing Tool for developers, Snyk can seamlessly integrate into development workflows.
- Provides real-time detection of vulnerabilities in code, containers, open-source dependencies, etc.
- Can rapidly identify and remediate security issues in every stage of the development lifecycle.
Why Snyk Matters?
Ensures effective protection for third-party components frequently used in SaaS development.
Also Read : Do SaaS Security Checklists Actually Work? Separating Fact from Fiction
9. Acunetix
Primarily designed to assess web application security, Acunetix offers automated web application security scans to detect vulnerabilities, such as cross-site scripting and SQL injection.
Important attributes
- Checks for OWASP Top 10 threats in web apps and APIs.
- Gives actionable reports to developers.
- Helps assess security in real-time.
Why It Is Important?
Acunetix is a targeted solution for web-based SaaS applications that effectively assists CTOs in risk mitigation.
10. Micro Focus Fortify
By conducting both static and dynamic security testing for web apps, Fortify offers a complete solution to provide and enhance SaaS platform security.
Vital Features
- Helps obtain a thorough evaluation of underlying vulnerabilities.
- Promotes workflow integration with DevSecOps.
- Recommends practical and reliable remedial measures.
Why It Matters?
Throughout the application lifecycle, Fortify guarantees ongoing security testing.
Evaluating Top Techniques for Security Testing in SaaS
In conjunction with the available tools for security, CTOs and SaaS entrepreneurs can also consider the following techniques:
- Include Early Security Testing with tools such as Veracode and Checkmarx in the development process.
- For undertaking real-time evaluations to enhance continuous monitoring, consider tools, such as Qualys and Tenable.io
- Utilize Veracode and Nessus for conducting automated compliance checks.
- Educate teams by using employee-training resources, such as CybeReady to bolster human-aided defence.
SaaS platform security has become a part of a proactive and multifaceted strategy In 2025. CTOs are more than ever expected to detect vulnerabilities to uphold compliance and safeguard confidential information by implementing the aforementioned and discussed top SaaS security tools for founders.
Wattlecorp’s team offers the best SaaS security testing tools and technologies, such as Burp Suite, OWASP ZAP, Veracode, Snyk, etc, to serve the ongoing security assessment needs of SaaS companies in today’s cybersecurity environment.
Whether you are concerned about developing reliable apps for your clients and are simultaneously seeking to make appropriate security testing investments for incorporating security and compliance into your SaaS application, give a call directly or book an appointment with us on our SaaS Security Program webpage to offer your users a more dependable and secure SaaS environment.
Frequently Asked Questions
1. How can I pick the best tools for SaaS security testing on my platform?
To choose the best tools for securing tests of SaaS solutions and applications, a foremost step is reaching agreement on the well-defined requirements that one thinks represent the best for them. Furthermore, the person can also think about running some DevSecOps processes paired with CI/CD pipelines through tools such as Veracode and Nessus. This also makes sure that GDPR and HIPAA compliance is secure. For real-time threat detection, Tenable.io or Burp Suite is another option. All in all, choose tools that can effectively help you achieve your SaaS security testing objectives, facilitate scalability, and successfully handle critical security issues.
2. How frequently should security testing be done for SaaS?
SaaS should undergo security testing regularly. Understanding the critical nature of integrating security in software development for cloud-based applications, these can be well served with tools like Qualys or Tenable.io. Apart from assisting in post-deployment monitoring, security testing tools, such as Burp Suite or Acunetix effectively help run dynamic testing prior to deployment of the applications. While Checkmarx facilitates Static Code Analysis during the development phase.
Additionally, when SaaS applications start utilising real-time security testing, this makes it easy for them to detect and nullify security vulnerabilities both during and post-development in the shortest time possible.
3. Can open-source tools like OWASP ZAP adequately ensure SaaS security?
Yes, they can. Since vulnerability scanning and penetrYes, they can. Since vulnerability scanning and penetration testing happen to be the pillars for undertaking security analysis and compliance checks in software development, there is no doubt that the same kind of security test will apply to SaaS platforms, applications, and solutions during and after post-deployment. You need to, however, note that an extensive feature set is not available for expansive SaaS solutions. Consider combining enterprise-grade programs like Qualys or Veracode with open-source technologies for strong security to address compliance, monitoring, and thorough risk assessments.