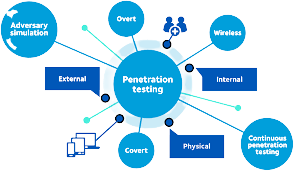
Penetration testers were prominent and were one of the best ways to find out the various vulnerabilities present in a system along with reports of the severity of risks posed by each of them. Then came along automated vulnerability scanners which found the same vulnerabilities at a cheaper price. In a world leaning towards automation and cheap labor, there came the million-dollar question – Do we need penetration testers when we have vulnerability scanners?
Before we step out to answer this question, we would need to understand the differences between penetration testers and vulnerability scanners, the pros, and cons, and some other things. A clear picture of both sides is required to give a whole verdict. Let us go to find the answer.
Vulnerability Scanners
As mentioned earlier, a vulnerability scanner is an automated tool. It scans the system for vulnerabilities and reports them once the scan is done. There are two types of vulnerability scanners – internal and external.
Internal vulnerabil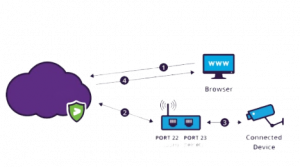
External vulnerability scanners are done outside the network. This is done to know about vulnerabilities in the firewall. This type of scan is done from an external point to check for any weak points in the firewall that would be a vantage point for cybercriminals to enter the system.
The Pros and Cons of Vulnerability Scanners
Pros –
- It is quite affordable at around 100$ per year, depending on the scanning vendor
- It is automatic and can be scheduled for daily, weekly, or monthly scans
- It is completed quickly
Cons –
- Companies need to manually check the risk factor associated with each vulnerability
- Doesn’t mention the exploitability of each vulnerability
So while vulnerability scanners find out the vulnerabilities present in the system, there is no way to find out the risks they pose. Those vulnerabilities could be random bugs that just show extra whitespaces or severe holes in the code that act as backdoors for cybercriminals to enter and leave at their whims. The only way to analyze the severities would be to employ additional tools or testers.
Penetration Testers
Now that we’ve analyzed vulnerability scanners, let us learn about penetration testers and the crux of this question we need to answer. One major difference between vulnerability scanners and penetration testers is the medium through which is done. Penetration testers are highly skilled ethical hackers while vulnerability scanners are automated tools.
Penetration testers, like vulnerability scanners, scan the network for vulnerabilities but take the extra mile. Penetration testers then check the exploitability of each vulnerability like cybercriminals to know the severity of the vulnerability, making it an even more efficient process. Penetration Testers are recommended annually or bi-annually for every company.
Pros and Cons of Penetration Testers
Pros
- Since the test is manual and done in real-time, the results are more accurate
- Most plans include retesting once the remediation is done
- Annual tests are needed and after major changes to the code
Cons
- Since each vulnerability is manually tested, it takes longer from around a day to 3 weeks.
- The cost is much higher than vulnerability scanners and is around 150 times higher, costing $1500 – $1600 per scan
The inspection of each vulnerability does give penetration testers an extra edge over vulnerability scanners. While they are not needed regularly, such tests are required to check for any compromising issues that can be unknowingly done while bringing about a major change to any part of the application.
The Verdict
Vulnerability scanners are an interesting tool as they conduct quick scans with instantaneous results. While knowing about vulnerabilities is a good thing, proper actions can be taken only after knowing the severity of each of them. Since penetration testers need to step in to play at this junction, penetration testers remain relevant as long as the exploitation of vulnerabilities, penetration testing is still needed to understand the flaws in a system.
Contributors : Derin Shyju