Table of Contents
ToggleHow to Ensure Data Privacy Compliance with NCA ECC in Saudi Arabia?
The National Cybersecurity Authority (NCA) in Saudi Arabia was established with the vision of creating a unified security baseline across different sectors. NCA ECC guideline mandates strict measures to strengthen the security readiness of an organization and reduce risks that arise from security threats.
With an increasing concern over cybersecurity and data protection, the NCA ECC framework helps businesses to effectively implement data privacy compliance.
Read through to understand how the NCA ECC intersects with data privacy, how to implement it, and why it’s vital for any organisation operating in Saudi Arabia.
What is NCA ECC Compliance?
In 2018, Saudi Arabia’s National Cybersecurity Authority (NCA) introduced
Essential Cybersecurity Controls (ECC), based on different international cybersecurity standards. It was established as a cybersecurity requirements guide that assists government organizations that operate critical national infrastructures to become cybersecurity resilient.
In 2023, the ECC guidelines were modified to adapt global best practices. The primary aim of NCA ECC compliance is to ensure that government entities and private sector organizations adhere to Saudi data privacy laws.
The National Cybersecurity Authority introduced ECC-2 in 2024, in which a tier-based compliance model was adopted. Based on the risk exposure, organizations are classified under 3 tiers:
- Essential
- Advanced
- Minimal
This helps organizations of different sizes to meet the cybersecurity standards based on their threat exposure and not follow an ideal model.
The ECC framework is structured into:
- 5 main cybersecurity domains
- 29 subdomains
- 114 specific controls, which were later reduced to 108 controls in ECC-2
The following are the National Cybersecurity Authority ECC’s 5 major domains:
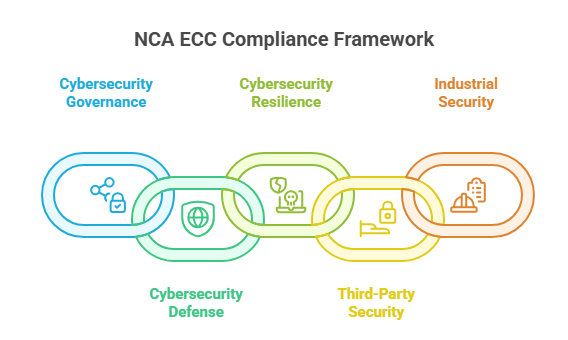
- Cybersecurity Governance
- Cybersecurity Defense
- Cybersecurity Resilience
- Third-Party and Cloud Computing Security
- Industrial Control Systems Security
Complying with ECC guidelines is mandatory for businesses that operate in Saudi Arabia, as this can ensure data protection and resilience in cybersecurity posture. The consequence of non-compliance begins with regulatory restrictions, penalties, and sanctions for a longer period.
Data Privacy: Crucial to NCA ECC Framework
In order to align with international best practices like GDPR, NCA ECC places more emphasis on data privacy and protection. With the Saudi Personal Data Protection Law (PDPL) that came into effect in 2023, NCA ECC risk assessment simply becomes a guideline to fulfill data privacy requirements.
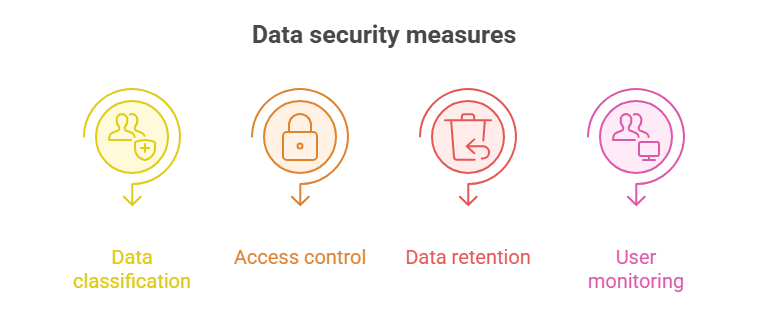
Key intersections of NCA ECC and data privacy:
- Data classification, which is defined according to the NCA data classification guidelines
- Access control and encryption
- Data retention and disposal policies
- User activity monitoring and incident response
From 2018 to 2024: The Changes in ECC-2
ECC-2 scope extends to extra-territorial application, as there is more Saudi governmental involvement in FDI initiatives. Another important mandate regarding ECC-2 is more Saudization. As per the mandate, all cybersecurity positions within organisations are to be occupied by qualified Saudi professionals.
Also Read : Cybersecurity and Data Privacy Regulations: Understanding the Connection
Who Needs to Comply With NCA ECC Compliance?
ECC has a larger reputation; NCA ECC compliance can increase stakeholders’ and clients’ trust in your organization. The following are businesses that need to adhere to NCA ECC guidelines.
- Government Entities: Those that deal with sensitive data
- Private Sector Organizations: Those handling sensitive data or essential services
- Digital Service Providers: Those offering cloud, software, and IT services
- Semi-governmental entities & critical infrastructure providers
Compliance is assessed by an accredited body through cybersecurity audits and risk assessments. Non-compliance can lead to regulatory penalties, increasing the risk of exposure to cybersecurity threats.
The Goal Behind ECC
- To achieve Saudi Vision 2030, KSA released the Personal Data Protection Law in 2023 as part of continuing the progress Saudi Arabia’s NCA put forward the ECC guidelines to enhance the cybersecurity infrastructure of organizations.
- To ensure all entities, including government, private, and critical national infrastructure organizations, develop preventive and detective controls to address emerging threats.
- To boost trust among stakeholders by ensuring the safety of their data.
NCA ECC Implementation: Data Privacy Compliance Roadmap
Though NCA ECC is a baseline guidance for cybersecurity requirements, it provides enough breathing space for organizations to choose how they want to implement them.
NCA ECC implementation requires continuous effort with constant monitoring, periodic assessment, and regular document updation.
1. Conduct a Gap Analysis
Before beginning NCA ECC implementation, organizations must conduct a detailed NCA ECC risk assessment to identify existing vulnerabilities. To assess your readiness and gaps use the official NCA ECC checklist.
2. Build a Data Classification Strategy
Classifying data is one of the first steps toward compliance. The NCA ECC Saudi guidelines mandate a structured approach to identifying and labelling sensitive data.
Include:
- Public
- Internal
- Confidential
- Restricted
This classification helps determine the appropriate security and access controls, ensuring that data is protected according to its level of sensitivity.
3. Align Controls with Business Processes
Each of the NCA ECC controls must be integrated into your operational and technical environment.
Focus on:
- Employee awareness training
- Secure configurations
- Incident response planning
- Data backup and disaster recovery
4. Leverage ECC-Compliant Technologies
Implementing solutions that support the ECC NCA framework makes compliance easier and scalable.
Look for:
- DLP (Data Loss Prevention) tools
- IAM (Identity and Access Management)
- Encryption at rest and in transit
- SIEM (Security Information and Event Management) systems
The Common Challenges in NCA ECC Compliance
You may have noticed that getting your organization to adhere to NCA ECC compliance is no small feat. Some of the common challenges you are more likely to face are as follows:
1. Lack of Resources
Depending on the business and size of the organization, the requirements your organization needs to meet may vary. Small businesses that struggle with resources need to partner up with the best NCA ECC compliance services, like Wattlecorp, that provide ECC documentation in both Arabic and English.
Also Read : The Risks Of Unsupported OS: Protect Your Data and Privacy
2.Integration With Legacy Systems
This is where continuous infrastructure upgrade makes sense. If you have an old IT infrastructure, implementing new cybersecurity tools and measures can be tedious. This also goes true on a cultural level; training your employees on cybersecurity is essential to meet NCA ECC compliance, which can take time and a lot of muscle work.
3. Evolving Cybersecurity Threats
Cybersecurity threats are on a constant rise; your business strategy should reflect constant vigilance over the threat. To stay ahead of emerging threats, conduct a quarterly audit. Wattlecorp experts can help you with threat assessments tailored to the NCA ECC Saudi landscape.
With the growing cybersecurity risks and ever-evolving Saudi data privacy laws, you need to align your business strategy such that it adheres to the national cybersecurity authority ECC framework. Wattlecorp provides professional NCA ECC consulting services that can guide you through the process.
Wattlecorp is your one-stop destination for achieving and maintaining cybersecurity and data privacy excellence in Saudi Arabia. Our services span internationally, with a proven track record of successful cybersecurity services, especially in Saudi Arabia.
Complying with the NCA Essential Cybersecurity Controls is mandatory for all businesses. For expert NCA ECC consulting services, choose Wattlecorp’s cybersecurity services.
NCA ECC FAQs
1. How does NCA ECC ensure personal data protection?
By complying with NCA ECC regulations strengthens the cybersecurity infrastructure is strengthened, which prevents security breaches and ensures personal data protection. Since the scope of ECC-2 includes both governmental and private sectors that deal with sensitive personal data, adherence to NCA ECC compliance improves cybersecurity readiness and safeguards personal data.
2. What is the NCA ECC–2 2024 framework?
The 2024 updated version of Saudi Arabia’s National Cybersecurity Authority ECC-1:2018 (ECC-1) is ECC-2. ECC-2 is established to strengthen the evolving cybersecurity needs of KSA, along with streamlining more control to the authority when it comes to data localization.
3. What are the differences between NCA ECC and global data privacy laws?
The major differences can be categorized as follows:
| Key differences | NCA ECC | Global data privacy laws |
| Scope | The scope is to establish cybersecurity readiness, and the data protection is only considered as a subset feature. | The primary focus is on regulating how personal data is collected, processed, stored, and shared. |
| Application | It is considered mandatory for both Saudi governmental entities and private sector operators. | Applicable for private companies and foreign businesses. |
| Enforcement Framework | Compliance is backed by Saudi Arabia’s National Cybersecurity Authority. | Backed by an independent data protection authority. |