For business entities like you operating in the UAE, you know how crucial it is to abide by the laws and regulations prevailing there. With modern businesses relying on web applications for all their routine tasks, it’s more than fulfilling compliance standards.
From customer portals and payment gateways to admin dashboards and APIs, everything runs through a web interface. However, with more tools, users, and data flowing through these systems than ever before, the attack surface has never been wider. This is why you need OWASP penetration testing to secure your web applications – something that goes far beyond plain generic scan.
As a founder or a tech leader, you ought to keep yourself abreast of the changing threat environment. This means adopting a security approach that allows you to think like an attacker, works like your dev team, and evolves as fast as your tech stack.
OWASP penetration testing goes beyond safeguarding your web applications. Your compliance status stays resilient with changing UAE regulations in 2025 and beyond.
Table of Contents
Toggle- OWASP Penetration Testing For Ongoing Web Application Security
- Why Is OWASP Penetration Testing Essential for Web Application Security in 2025?
- How OWASP Penetration Testing Protects Web Applications from Cyber Threats?
- Best OWASP Penetration Testing Strategies for Securing Web Applications
- The OWASP Web Application Penetration Testing Checklist
- How OWASP Penetration Testing Helps Startups and Enterprises Alike?
- A Closer Look Into The OWASP Penetration Testing Framework
- What Is The Future of OWASP Web Application Security Testing in 2025 and Beyond?
- OWASP FAQs
OWASP Penetration Testing For Ongoing Web Application Security
OWASP (Open Worldwide Application Security Project) is a nonprofit organization that’s been setting the gold standard for web application security testing for over two decades.
The OWASP Top 10 being one of their major resources can clearly list the most critical vulnerabilities found within web applications.
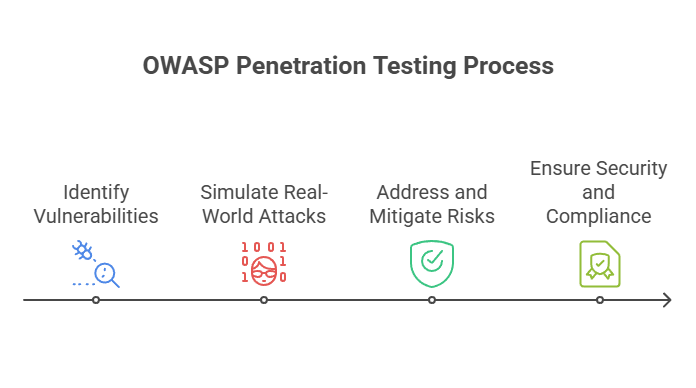
As a structured approach, OWASP pentesting secures web applications by utilizing a host of standards and tools.
Simulates real-world attacks by using the OWASP Top 10 and other risk models to identify, address, and mitigate vulnerabilities – before bad actors can enter and attack.
Think of it as a cheat sheet for what hackers are likely to exploit.
More than being about ticking boxes, it’s about understanding how your app could be broken, abused, or manipulated in the wild. Fixing those gaps before it’s too late is what OWASP Pentesting focuses on.
As a cybersecurity team at Wattlecorp, our expertise in offering varied sorts of penetration testing services have resulted in our clients achieving both security and compliance.
Why Is OWASP Penetration Testing Essential for Web Application Security in 2025?
Attackers have evolved. They’re using AI. They’re targeting APIs. They’re finding new ways to manipulate business logic and chain vulnerabilities.
At the same time, your own teams are deploying code faster by moving to the cloud. Adding third-party integrations. Using microservices.
The game has changed.
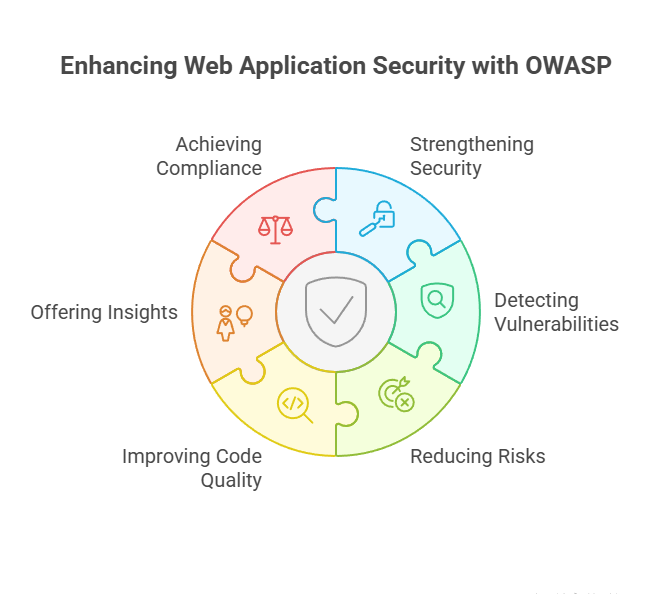
OWASP security testing for web applications is crucial in these scenarios to:
- Strengthen and enhance application security.
- Detect common vulnerabilities
- Reduce risks for businesses
- Improve code quality
- Offer actionable insights
- Achieve compliance.
With OWASP pentesting serving the above purposes, especially in meeting compliance standards in the UAE, ever wondered how? By helping your businesses identify and mitigate security flaws before they can be exploited.
You minimize risk of data breaches – achieving adherence to industry standards, such as ISO 27001, and ADHICS.
As per the UAE Cabinet’s comprehensive National Cybersecurity Strategy approved in 2025, this was targeted at enhancing the digital resilience of the nation. Establishing NSOC (National Security Operations Center) to monitor threats in real-time is central to this strategy. Equal importance is given to launching the national vulnerability disclosure program to promote responsible reporting of security laws.
The OWASP penetration testing for Web Applications security in the UAE is all about developing a hacker mindset to identify, assess, and nullify inherent vulnerabilities. Businesses operating here can effectively:
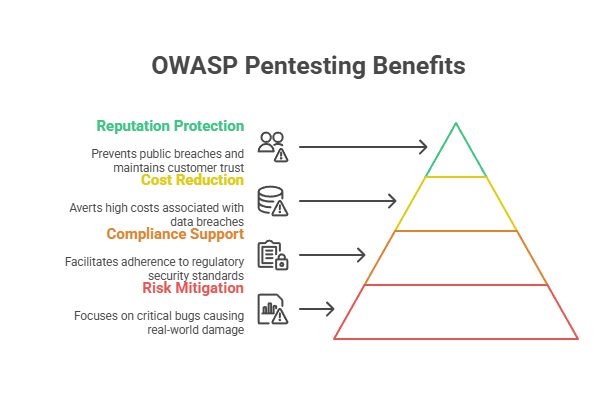
- Catch real risks: Not every bug is critical. OWASP pentesting focuses on the ones that could lead to real-world damage: data loss, unauthorised access, and financial fraud.
- Support compliance: Regulatory frameworks like SOC 2, PCI DSS, ISO 27001, and GDPR now expect regular and structured security testing. This is conveniently possible with OWASP.
- Reduce Breach Costs: The average cost of a data breach in the UAE in 2024 was $8.75 million. A security incident of this magnitude could’ve been averted by the OWASP penetration testing.
- Protect Reputation: One public breach can shake customer confidence, slow down deals, and trigger regulatory scrutiny. OWASP pentesting can prevent such consequences and protect your business reputation.
In short, OWASP web application penetration testing is not only a “nice-to-have.” It’s the guardrail to keep your business upright in an increasingly hostile digital landscape.
How OWASP Penetration Testing Protects Web Applications from Cyber Threats?
Here’s how OWASP pentesting works in practice.
Let’s say you run an eCommerce platform. You’ve got a login system, payment API, user accounts, product listings, and admin panel.
Without proper OWASP security testing for web applications, here’s what might go unnoticed:
- Your login page is vulnerable to brute-force attacks.
- The payment API leaks sensitive error messages.
- The admin panel becomes accessible due to inappropriate session checks.
- Business logic flaw lets users game the discount system.
- Misconfigured S3 bucket exposing customer invoices.
OWASP pentesting uncovers these flaws and shows you exactly how they could be exploited.
It doesn’t just give you a list of problems. It shows you where your application is weakest and prioritises fixes based on risk severity. No wonder for OWASP to outshine traditional testing approaches.
Also Read : OWASP Top 10 for LLM (Large Language Model) Applications
Best OWASP Penetration Testing Strategies for Securing Web Applications
If you want to get the most out of OWASP web penetration testing, here’s what works:
- Start with the OWASP Top 10
These are the ten most critical security risks for web applications. Things like injection flaws, broken access controls, insecure design, and security misconfigurations. Every test should check for these.
- Adopt the OWASP Testing Guide
This is the full playbook. It includes a detailed list of tests mapped to different components of your application—from authentication to data validation to session management.
- Use a Skilled Testing Team
Automated tools can help, but OWASP penetration testing is most effective when driven by human testers, who understand logic, context, and edge cases.
- Test Continuously, Not Just Quarterly
Web applications change constantly. Every new feature, integration, or environment shift can introduce new risks. Continuous testing—whether through managed services or internal pipelines—helps you stay ahead of potential risks and threats.
- Shift Left, Integrate Early
Embed security testing early in your CI/CD workflow. This aligns with OWASP security best practices and saves time and cost by catching flaws before they go live.
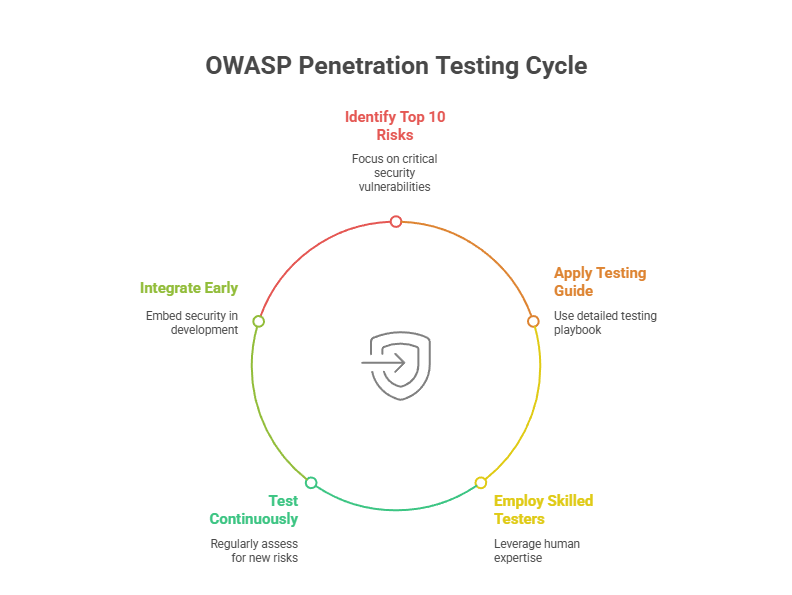
The OWASP Web Application Penetration Testing Checklist
For a more practical application of the OWASP web application penetration testing, apply the checklist below:
- Input validation testing (SQLi, XSS, Command Injection)
- Authentication and session management testing
- Access control and privilege escalation checks
- API testing for insecure endpoints
- Business logic abuse scenarios
- CSRF and clickjacking tests
- File upload and path traversal checks
- Cloud configuration reviews (S3, IAM policies, etc.)
- Logging and alerting validation
- SSL/TLS and cryptographic standards assessment
This is not an exhaustive list, but it gives you an idea of how deep OWASP web application security testing can go.
The OWASP Web Application penetration testing has high relevance in the context of the UAE’s establishment of the National Cybersecurity Academy to train professionals in cybersecurity skills. This is given the latter’s realization to address the growing need for a skilled workforce in this domain.
Initiatives, such as the Cyber Pulse program to raise cybersecurity awareness among citizens will also benefit from OWASP pentesting in the long run.
Also Read : OWASP API Security Top 10 (2024 Updated)
Why Is OWASP Security Testing for Web Applications Better Than Traditional Security Audits?
Here’s the difference.
Traditional security audits look at policies, configurations, and maybe a few external scans. Useful, but limited.
OWASP web application penetration testing dives into the application logic, user behavior, and underlying infrastructure. It finds flaws you can’t spot from the outside.
This is critical for modern businesses that rely on custom-built platforms, SaaS products, and complex integrations. These are not off-the-shelf products—they’re built piece by piece to cope with the unique and dynamic risk landscape.
How OWASP Penetration Testing Helps Startups and Enterprises Alike?
Whether you’re a seed-stage startup or a global enterprise operating in the UAE, you’re facing the same attackers. In fact, smaller companies are often more vulnerable because they lack dedicated security teams.
OWASP penetration testing helps level the playing field.
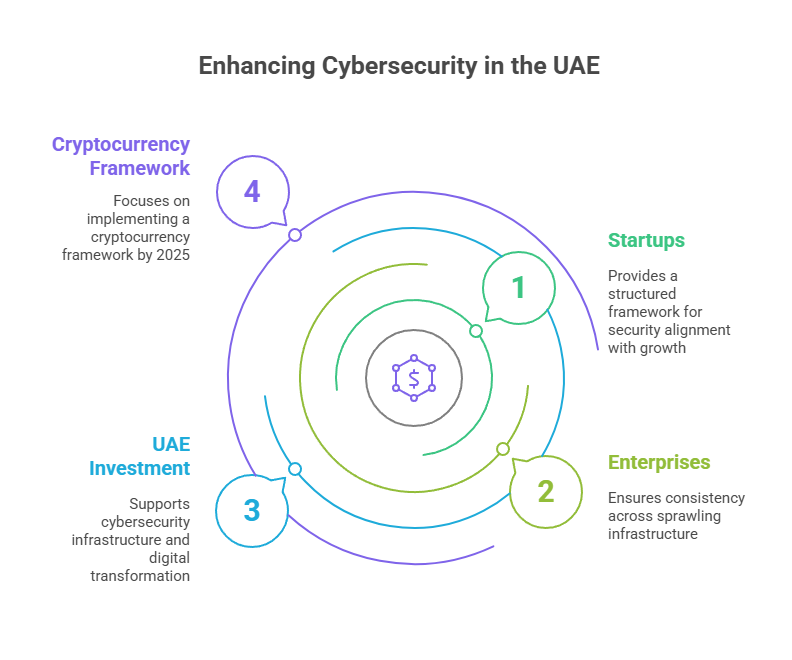
- For startups: A structured framework that aligns security with growth.
- For enterprises: Ensures consistency across sprawling infrastructure.
Either way, you’re investing in long-term resilience – being a business operating in the UAE.
As part of its efforts to sustain and underpin its cybersecurity infrastructure and digital transformation endeavors, the UAE has invested over $2 billion. An investment like this is meant to support development of new cybersecurity standards and policies. There is also a continued focus to implement a cryptocurrency framework in 2025.
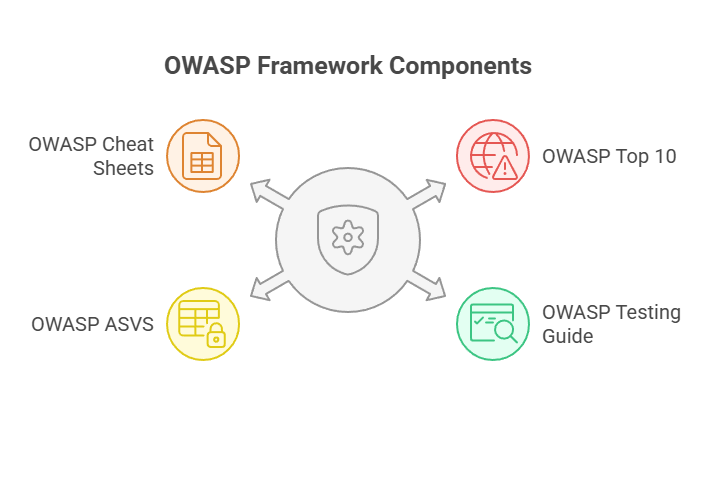
A Closer Look Into The OWASP Penetration Testing Framework
The OWASP penetration testing framework comprises a collection of guidelines, resources, and methodologies that shape pentest conduction.
It includes:
- OWASP Top 10: Focuses on the top 10 serious dangers associated with web applications.
- OWASP Testing Guide: Offers detailed testing techniques
- OWASP Application Security Verification Standard (ASVS): Helps define security requirements for development
- OWASP Cheat Sheets: Bite-sized guides on best practices (e.g., secure coding, authentication, session management)
This framework provides structure, consistency, and a shared language for security professionals, developers, and business leaders.
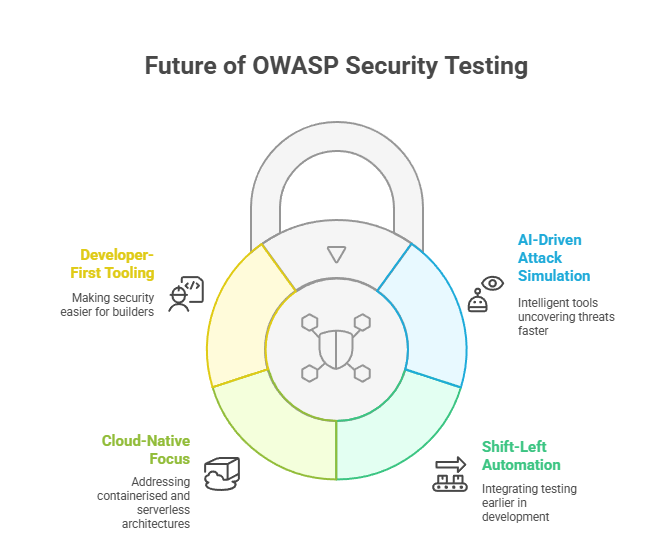
What Is The Future of OWASP Web Application Security Testing in 2025 and Beyond?
We’re in an era of automation, AI, and hyperconnectivity. Applications are more powerful, but also more complex. And complexity breeds vulnerability.
Here’s where OWASP penetration testing continues to evolve:
- AI-driven attack simulation: More tests will use intelligent tools to uncover threats faster.
- Shift-left automation: Development lifecycle will have testing integrated earlier into them.
- Cloud-native focus: OWASP tools and guides will increasingly address containerised and serverless architectures.
- Developer-first tooling: Making security easier for builders, not just auditors.
OWASP is already moving in this direction. Staying aligned with their resources is the best way to keep your application secure in a changing world.
‘Mohamed Al Kuwaiti, UAE government’s Head of Cybersecurity announced that UAE will establish a Cybersecurity Center of Excellence. The intent is to advance/enhance cybersecurity by leveraging AI through the Cyber Pulse initiative.’
By the time most businesses discover a breach, it’s already too late. The cost isn’t just technical. It’s legal, reputational, and sometimes existential.
With Wattlecorp’s OWASP web app security testing services, you stay ahead of potential threats – ensuring thorough control of all critical features of your applications.
OWASP penetration testing makes it certain that you:
- Know where you’re vulnerable
- Prioritize what to fix
- Align with compliance
- Build customer trust
- Sleep better at night
Whether you’re securing a small SaaS app or a massive customer-facing platform, OWASP web application penetration testing gives you a clear path forward.
Don’t wait for a breach to take security seriously. Build it into your product. Make it part of your process as dictated by the regional policies that govern you (here, UAE). That’s how you stay secure in 2025!
OWASP FAQs
1.How does OWASP penetration testing help prevent cyber threats for UAE businesses in 2025?
OWASP penetration testing identifies vulnerabilities that attackers are most likely to target. It simulates real-world attack scenarios to find weak spots in your web application—whether it’s broken access controls, injection flaws, or insecure APIs. By catching these issues before attackers do, you reduce the risk of data breaches, system compromise, and compliance violations.
2.How often should businesses conduct OWASP penetration testing?
At a minimum, you should test:
Before major releases
After significant code or infrastructure changes
Quarterly or bi-annually for mature products
Continuously for high-risk environments (e.g., fintech, healthcare)
The more dynamic your app, the more often you should test them.
3.How does OWASP penetration testing differ from regular security testing?
Regular security testing might involve vulnerability scans, policy checks, and automated tools. It’s good for a surface-level view.
OWASP penetration testing for UAE businesses goes deeper. It prompts you to develop an attacker mindset by mimicking app exploitation for weaknesses. It also hunts for logic flaws, chained exploits, and real-world consequences. It’s not just about finding issues—it’s about showing how they could be used against you.