Key Takeaways:
- VAPT is a complete security check-up of your SaaS and it behaves more like a hacker in order to locate the points of weakness that may allow one user to get access to the information of another. This will assist your team in solving issues in the beginning and maintaining the data of all tenants separate and secure.
- Periodic testing will prevent attacks, with high frequency of running VAPT, your company will be able to identify and rectify them before anyone attempts using them. This helps in making your software strong and your customer information safe.
- VAPT assists to adhere to the UAE data protection regulations, security assessment provides evidence that your system is employing the appropriate safety tools in protecting information of users. That way, it is simpler to go through audits and demonstrate to your clients that your platform is credible.
- Consistent monitoring creates trust with your users, in case your customers are aware that you test your platform to ensure that it is safe, then they are more assured that they can use it. Such trust will be able to make your service stand out among others in the market.
Table of Contents
Toggle- A Complete Guide to Building Secure Multi-Tenant SaaS Platforms
- Why Data Isolation is Critical in SaaS Platforms?
- Understanding VAPT in Multi-Tenant SaaS Environments
- Common Vulnerabilities in Multi-Tenant SaaS Platforms
- How VAPT Strengthens Data Security and Tenant Isolation?
- Key Compliance and Regulatory Considerations
- Sustainable SaaS Growth Depends on Proven Security Controls
- VAPT for SaaS Platforms FAQs
A Complete Guide to Building Secure Multi-Tenant SaaS Platforms
VAPT for SaaS platforms has become a critical foundation for securing multi-tenant architectures, where a single weakness can expose multiple customers to systemic risk.
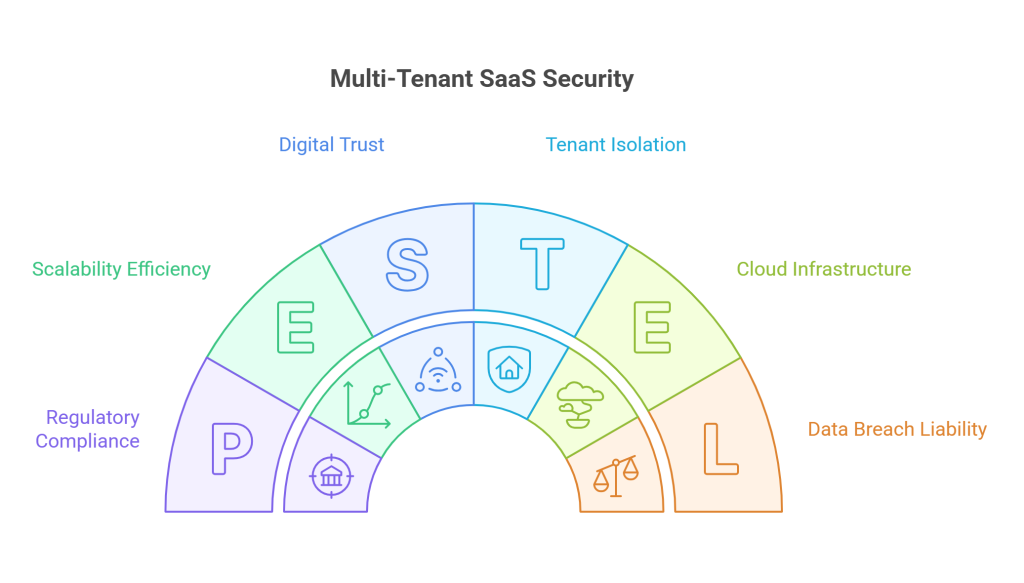
Multi-tenant SaaS security refers to the security practice that secures a cloud application in which several customers (tenants) utilize the same infrastructure, databases and resources used by UAE enterprises.
It concentrates on ensuring that the data and activities of every tenant remain separated although they are operating on the same system.
Digital trust has become a primary factor in the modern enterprise landscape including UAE markets. For organizations built on a multi-tenant Saas architecture, the responsibility of safeguarding client data is no longer just a technical requirement, it is a high level priority.
As businesses scale, the logical walls that separate one customer’s sensitive data from others are under constant scrutiny from both regulators and advanced threat actors.
Operating a multi-tenant saas platform in UAE offers unparalleled efficiency and scalability. However, this shared infrastructure creates unique attack surfaces too.
A single oversight in authorization logic or a minor configuration error in the cloud can lead to a catastrophic cross-tenant breach. In 2026, the question is no longer whether your platform is functional, but whether your tenant isolation is truly unbreakable.
For SaaS providers, the path to long-term sustainability lies in proving that their architecture is resilient enough to handle the complexities of the modern threat landscape.
Why Data Isolation is Critical in SaaS Platforms?
Data isolation stands as the backbone of privacy in the cloud for UAE organizations, preventing unauthorized access and keeping each user’s information safely apart.
It is the technical framework that ensures that even though multiple organizations share the same hardware and software resources, their data remains strictly segregated.
It is important to understand that while multi-tenancy optimizes resource usage, it inherently increases the risk of data leakage when evaluating multi-tenant vs SaaS.
Without a strong isolation of cyber security, a platform risks a data bleed incident. This occurs when a user from one organization is mistakenly granted access to the records, financial data, or personal information of another.
This is not merely a software bug, it is a fundamental failure of the service provider’s promise to the UAE client.
Maintaining rigorous isolation is the only way to ensure that the disruptive tenant or a malicious actor within the system cannot compromise the integrity of the entire platform.
Understanding VAPT in Multi-Tenant SaaS Environments
VAPT in Multi-Tenant SaaS leads us to a critical strategic question: What is VAPT and why is it essential for multi-tenant SaaS platforms?
VAPT (Vulnerability Assessment and Penetration Testing) is an efficient security methodology designed to identify and exploit vulnerabilities before they can be leveraged by an attacker.
For SaaS platforms, the VAPT process is significantly more complex than a standard network scan. It requires a deep understanding of application logic and user permission structures.
Also Read : Top SaaS Security Testing Tools Every CTO Should Evaluate in 2025
When Wattlecorp conducts VAPT for SaaS platforms in UAE, our experts simulate the behavior of an advanced adversary.
We focus on Horizontal Privilege Escalation, the ability of one tenant to move sideways into another’s environment. We don’t just look for missing patches; we look for the unseen flaws in how your application decides who gets to see what.
- Are the API keys properly scoped to specific tenants?
- Does the database layer enforce isolation, or is it solely dependent on the application layer?
- Can a standard user manipulate requests to view administrative data?
Common Vulnerabilities in Multi-Tenant SaaS Platforms
The most common vulnerabilities in multi-tenant for SaaS Products are:
- Critical Data Breaches: SaaS platforms rely on gathering and storing vast amounts of user information and they are the prime targets for exploitation. A single leak of sensitive records doesn’t just result in immediate financial loss; it triggers a chain reaction of legal penalties and a permanent loss of customer trust.
- Weaknesses in Access Management: It is complicated to establish security control on who can see what in multi-tenant setups. When such protocols are unstructured or not properly configured, it leaves an unlocked door to unauthorized users to compromise security walls, install malicious software or extract personal information.

- Targeted Ransomware Extortion: When hackers have control of your system infrastructure or confidential data, they take control of your data. They then hold this data and demand huge amounts of money in exchange with decryption keys that may freeze company operation for weeks.
- The Risks of Shared Infrastructure (Multi-Tenancy): The multi-tenant SaaS architecture is cost-effective, but there is a neighbour risk. One account breach can act as a point of entry into the data storage of all the other customers using the same server provided that security boundaries of the tenants have not been taken care of.
How VAPT Strengthens Data Security and Tenant Isolation?
SaaS providers in UAE must move beyond basic defenses and adopt a strong VAPT strategy that stops attacks before they happen to stay secure in these modern threats.
Here are the essential pillars for maintaining a secure platform serving UAE enterprises:
- Routine Security Checks: You shouldn’t wait for a breach to find your weak spots. By scheduling regular SaaS penetration testing, you can find and fix holes in your code before hackers do. It is much easier to fix a flaw early than to deal with a data leak later.
- Strict Access Rules: Using Multi-Factor Authentication (MFA) and setting a clear role for each user ensures that people only see the information they need for their specific jobs. This keeps your most sensitive data locked away from unauthorized eyes.
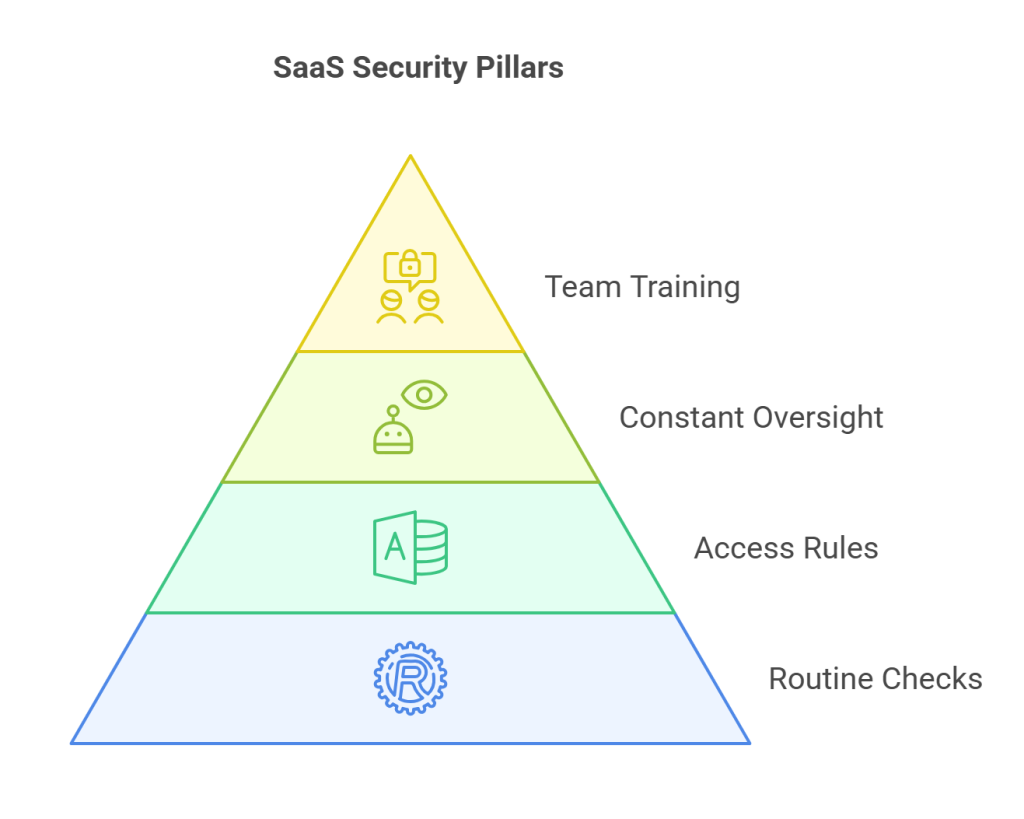
- Constant Oversight: Using tools for real-time monitoring gives you a clear view of your system. Ensure to notify immediately if someone tries to log in from an unauthorised system or moves large amounts of data and can act fast to stop them.
- Team Training: Your employees are your first line of defense. Most data leaks happen because of a simple human mistake, like clicking a bad link. Regular, simple training on how to spot scams and manage passwords can turn your staff into a strong shield for your company.
Key Compliance and Regulatory Considerations
To SaaS providers that are located in the Middle East, cybersecurity has become a legal obligation.
The UAE Federal Data Protection Law has also established high standards for Data Processors, whereby they are required to have technical measures to secure the privacy of the UAE residents.
Non-compliance may lead to severe legal fines and operating licenses. However, compliance should be viewed as more than a hurdle, it is a mark of quality.
Also Read : Aligning VAPT Practices with UAE’s Data Protection Regulations
Regular VAPT for SaaS platforms provides the documented evidence that your organization meets these high standards.
In cities like Dubai and Abu Dhabi, where digital transformation is a national priority, having a certified security posture is often the prerequisite for securing high-value contracts with government and semi-government entities.
Wattlecorp delivers expert VAPT services in UAE to secure multi-tenant SaaS platforms through rigorous tenant isolation testing.
Sustainable SaaS Growth Depends on Proven Security Controls
Scale is the ultimate goal for any SaaS business, but scale without security is a liability. As you grow from a few early customers to a large global audience, the complexity of your multi-tenant saas architecture grows exponentially.
Therefore, managing your shared software system becomes more difficult and which is why Wattlecorp provides the expert help needed to secure your expansion.
At Wattlecorp, we offer specialized VAPT services in the UAE designed to meet the rigorous demands of the modern cloud. We provide more than just a report; we ensure the technical clarity needed to build a resilient, compliant and trustworthy platform.
You can ensure that your business is prepared for the challenges of tomorrow by identifying and fixing vulnerabilities today.
VAPT for SaaS Platforms FAQs
1. What is VAPT for SaaS platforms?
VAPT for SaaS is a specialized security audit that combines automated vulnerability scanning with manual penetration testing. It is designed to find flaws in application code, API security, and tenant isolation that could lead to unauthorized data access for UAE enterprises.
2. Why is data isolation crucial in multi-tenant SaaS?
Data isolation acts as a secure and private boundary for every client. Even within a shared environment, it ensures that each user’s information remains strictly inside its own space. A single technical mistake may allow one user to see the private records of another. Such an incident would likely result in a major data leak and a permanent loss of customer trust.
3. How does VAPT help in securing multi-tenant architecture?
VAPT serves as a complete checkup of your security framework for UAE SaaS platforms. Through acting like a real attacker, Wattlecorp assists to verify if there are any gaps that would let a user break the rules and access another customer’s data. This process allows your organization to find and fix these weak spots before they can be used by an actual threat.
4. What are the top vulnerabilities in multi-tenant SaaS?
The most common threats include BOLA (Broken Object Level Authorization), insecure API endpoints, and privilege escalation, all of which can allow attackers to jump between tenant environments.
5. How to ensure compliance with data protection laws in the UAE?
To remain compliant with the UAE Federal Data Protection Law, SaaS providers must conduct regular security assessments. VAPT provides the necessary documentation to prove that your platform uses high-level technical measures to protect personal data.