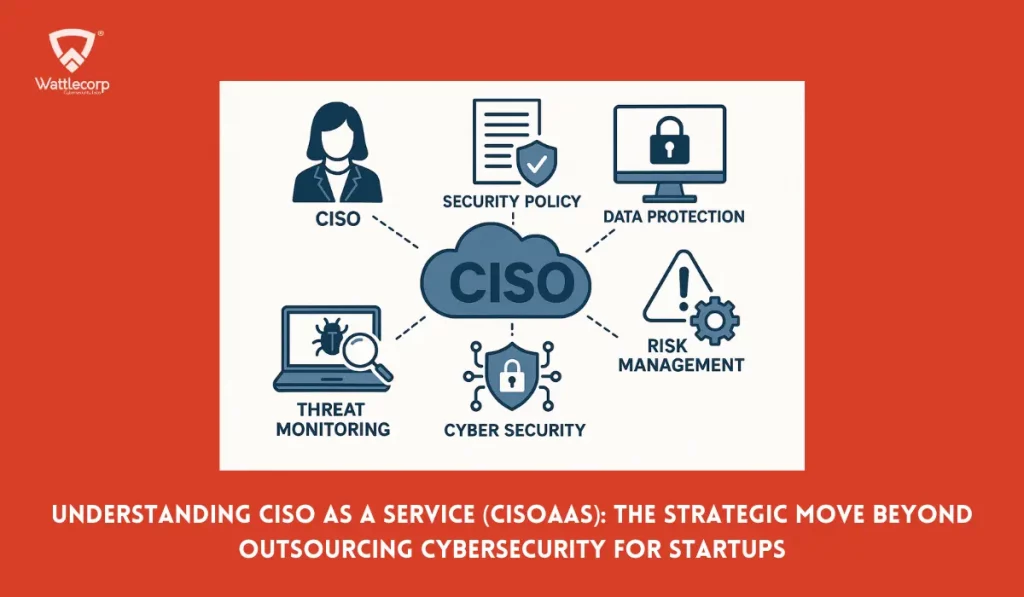
The rapidly evolving digital landscape is likely to make businesses like yours fall into an increasing array of cybersecurity threats.
While many organisations understand the importance of robust cybersecurity, not every business can afford or justify a full-time Chief Information Security Officer (CISO). This is where you can rely on CISO as a Service (CISOaaS) — a virtual, flexible, and cost-effective model that gives your business – access to high-level security leadership without requiring to hire a full-time CISO executive.
But what exactly is CISOaaS and why is it becoming an essential strategy for businesses today? Here, we’ll dive into the essentials of CISOaaS, explore its benefits, and discuss how you can integrate it into your organisation
Table of Contents
Toggle- The Evolution of the CISO Role: CISOaaS Model Explained
- The Emergence of CISOaaS
- Benefits of Adopting CISOaaS
- Evaluating the Need for CISOaaS: Indicators That Your Organisation Needs CISOaaS
- Selecting the Right CISOaaS Provider: Key Considerations and Criteria for Evaluation
- Strategies for Seamless Collaboration
- Potential Challenges and Considerations: Addressing Concerns Related to Data Confidentiality and Control
- Embracing CISOaaS as a Strategic Advancement
- Future Trends in CISOaaS: The Evolving Landscape of Cybersecurity and the Role of CISOaaS
- CISO as a Service FAQs
The Evolution of the CISO Role: CISOaaS Model Explained
Significant changes have been made to the Chief Information Security Officer (CISO)’s role over the years. Traditionally, CISOs focused more on the technical aspects of delivering cybersecurity services. These included defending against cyberattacks and ensuring compliance with regulations. However, today’s CISO is much more advanced. Apart from being a technical expert, they can influence key decision-making, driving key business strategies, risk management, and the overall security culture of an organisation.
As cyber threats become more sophisticated, organisations will need strategic security leadership that can well align with your business objectives. While full-time CISOs have become a crucial part of large enterprises, this is technically not practical or affordable for many smaller businesses or organisations with limited resources. To repeat, the concept of CISOaaS gains prominence in this scenario.
The Emergence of CISOaaS
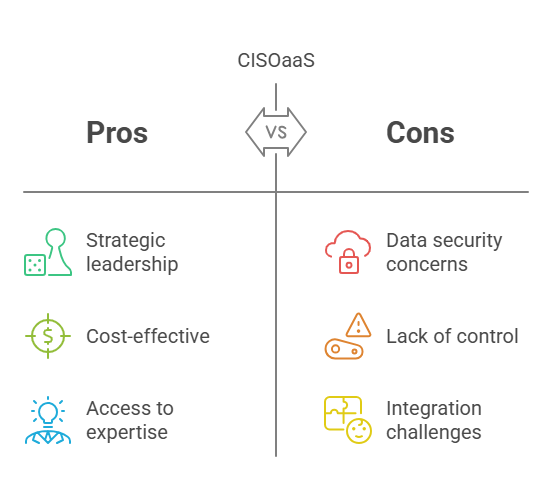
CISOaaS, also known as Virtual CISO (vCISO) or Fractional CISO, has emerged as a growing trend in terms of outsourcing CISO responsibilities.. By allowing you to access the knowledge and expertise of a seasoned security executive, it spares you the burden of having to hire a full-time CISO. The CISOaaS providers offer the same strategic oversight, leadership, and risk management that in-house CISOs provide, but on a flexible, part-time, or contract basis. This gives you the leadership you need to keep costs manageable.
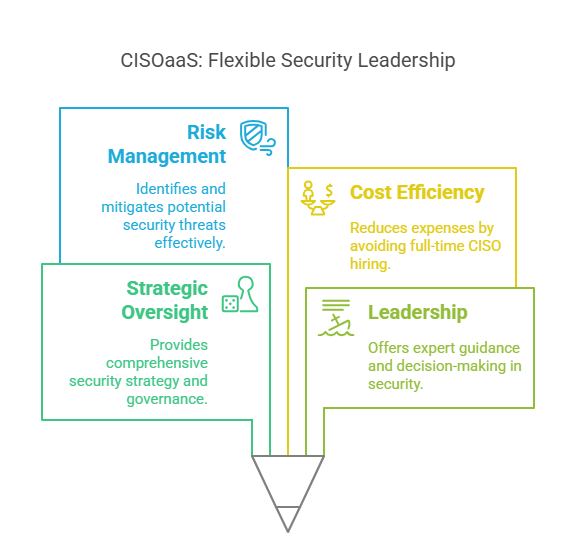
Benefits of Adopting CISOaaS
1. Cost-Effectiveness and Scalability
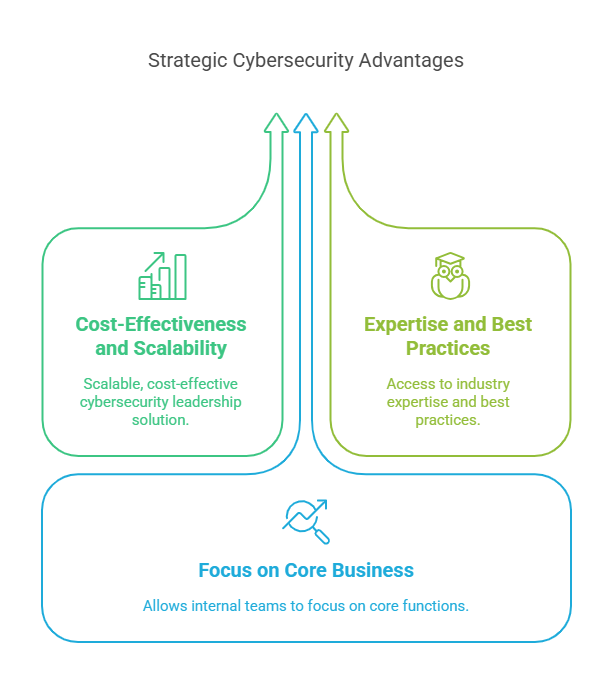
Cost-effectiveness and scalability serve as the highly notable advantages of CISOaaS. This benefit rules over the full-time CISO positions, which typically come with high salaries, bonuses, and benefits. Thus, for SMBs or enterprises needing specialised cybersecurity leadership, but don’t have the financial resources to hire a full-time CISO, CISOaaS offers a scalable solution. You only pay for the services you need, making it a flexible option for your business to thrive at various stages of its growth.
2. Access to a Broad Range of Expertise and Industry Best Practices
CISOaaS providers are known for their excellent knowledge and industry-specific expertise they showcase. They work across a range of organisations and industries, and this experience allows them to implement best practices and offer tailored advice and services based on the latest cybersecurity trends. By leveraging the knowledge and service of CISOaas, you can stay ahead of emerging threats, use advanced tools, and implement proactive security measures—all without needing to invest heavily in training or hiring multiple specialists.
3. Enhanced Focus on Core Business Functions
When you outsource your CISO responsibilities, your internal teams are free to focus on what they do best. Instead of worrying about the complexities of cybersecurity, your employees can concentrate on their areas of expertise. What your CISOaaS provider should do at this juncture is to help ensure that your organisation’s cybersecurity strategy aligns with your business objectives. Such a division of labor helps you operate more efficiently and effectively.
Evaluating the Need for CISOaaS: Indicators That Your Organisation Needs CISOaaS
Not every organisation needs CISOaaS, but if any of the following applies, it is high time that you start considering the following:
- Your team lacks in-house cybersecurity expertise.
- The growing risks of cyber threats tend to cause significant concerns for you.
- You need strategic cybersecurity leadership, but can’t justify a full-time hire.
- Compliance requirements are tough to manage in-house.
- Assessing Internal Capabilities vs. External Expertise
CISOaaS helps fill the gap in scenarios if you lack a full-fledged internal team or if it doesn’t have the needed level of expertise to effectively manage complex cybersecurity challenges. You should, however, make sure that CISOaaS complements your internal efforts and processes, and doesn’t replace them. It will also help if you take stock of your internal capabilities to determine whether external expertise is necessary or not.
Selecting the Right CISOaaS Provider: Key Considerations and Criteria for Evaluation
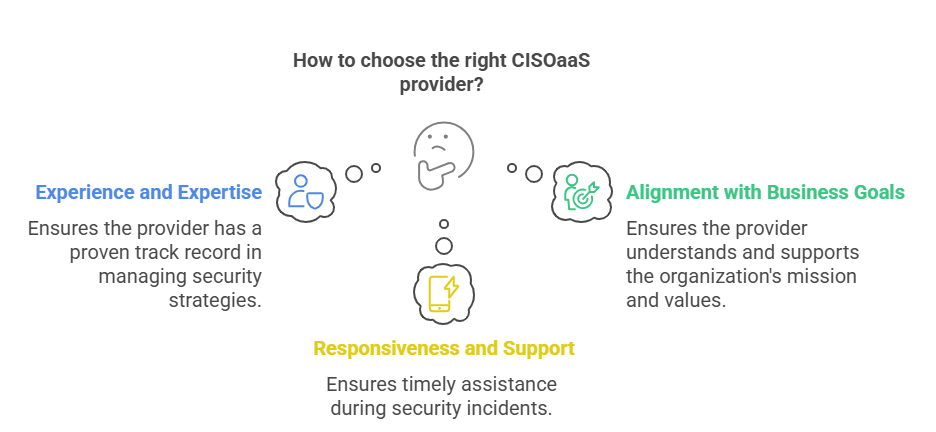
Choosing the right CISOaaS provider requires you to bear the following points in mind:
- Experience and Expertise: Look for a provider with proven experience in your industry and a successful track record of managing large-scale security strategies.
- Alignment with Business Goals: The vCISO provider is expected to understand the mission, values, and security needs of your organisation.
- Responsiveness and Support: Your provider should readily provide the timely support, especially when security incidents erupt.
Strategies for Seamless Collaboration
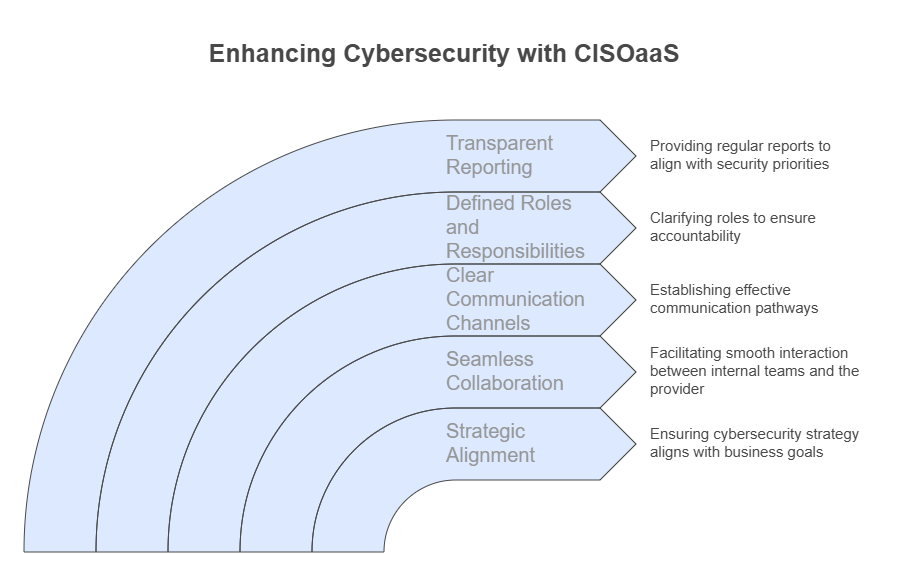
A good CISOaaS provider’s cybersecurity strategy should align with your broader business objectives. This will automatically ensure that security is seamlessly integrated into your day-to-day operations.
For CISOaaS to work effectively for your business, you must ensure seamless collaboration between your internal teams and the external provider. Also, setting clear communication channels and expectations from the beginning helps with smooth integration of CISOaaS into your business processes. Also, conducting regular meetings and preparing transparent reports will allow you and your CISO vendors to align with security priorities.
- Establishing Clear Communication Channels and Expectations
Creating a definitive framework allows your CISOaaS provider to effectively interact with your internal teams. Also, defining success metrics, timelines, and responsibilities upfront with the CISOaaS provider will help ensure a smooth collaboration.
- Define Roles and Responsibilities
You need to make sure that your CISOaaS provider understands their responsibilities and also integrates them into the security polities of your organisation.
Case Studies: Referring to success stories of organisations that successfully implemented CISOaaS
Many businesses, SMBs in particular, have found success with CISOaaS. For example, a growing fintech startup turned to a Fractional CISO to oversee their cybersecurity efforts. The result derived was a robust security strategy, improved threat management, and enhanced regulatory compliance—all without the cost of hiring a full-time CISO.
- Lessons Learned and Best Practices
There exists a strategic approach to successfully implementing CISOaaS – one that effectively integrates external expertise into your internal processes while allowing you to focus on long-term business goals.
Also Read : Proactive Threat Management For SaaS Business
Potential Challenges and Considerations: Addressing Concerns Related to Data Confidentiality and Control
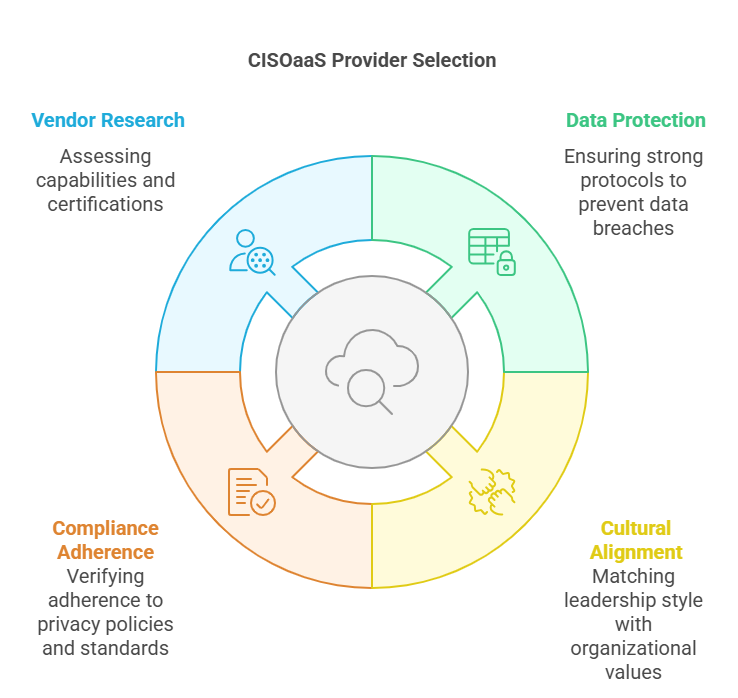
Outsourcing cybersecurity leadership can pose significant risks to sensitive data – primarily, data breaches. This may occur due to losing control over security practices. Make sure that your CISOaaS provider has strong data protection protocols on hand and also understands how important it is to maintain confidentiality.
- Ensuring Alignment with Organisational Culture and Values
It is also important for you to align your CISOaaS provider’s leadership style with your organisation’s culture and values. Doing so helps prevent miscommunication and sets the stage for long-term success. All these endeavours render a good cultural fit.
- Maintaining Strong Adherence To Data Privacy And Compliance
The responsibilities of ensuring whether your CISO provider adheres to data privacy policies and compliance requirements is up to you. Time and again, you need to assess how they handle those necessary underlying policies and guidelines, including compliance standards. How they respond to security incidents and what procedures they follow also should be taken into consideration..
- Undertaking Thorough Research For Selecting The Right Vendor
Prior to hiring your potential CISO vendor, you should know their capabilities. It does a lot good when you are adequately assured of their knowledge, proven level of experience, and expertise. Adding credibility to these is knowing the kind of security certifications they hold and ensuring these are compatible with the accepted compliance standards.
Embracing CISOaaS as a Strategic Advancement
Adopting CISOaaS is more than just outsourcing—it’s a strategic move that allows your business to avail specialised expertise and leadership while remaining flexible and cost-effective. If you want your businesses to thrive in this ever-evolving digital landscape thronged with the constant challenges of cybersecurity threats, turning to CISOaaS’ assistance is the only critical solution.
Also Read : vCISO vs CISO: Which One Is Right for Your Business?
Future Trends in CISOaaS: The Evolving Landscape of Cybersecurity and the Role of CISOaaS
As cyber threats become more advanced, what lies beyond is a continuous expansion of the virtual CISO role. We can spontaneously expect a greater reliance on automation, AI-driven threat intelligence, and proactive security frameworks.
The vCISO service offerings from Wattlecorp’s side comprise a whole list, including providing expert guidance for building a comprehensive cybersecurity strategy. We also assure supporting your broader organisational objectives by aligning your security needs in all aspects of your business – IT and operations.
Predictions for the Integration of AI and Automation in CISOaaS Offerings
The cybersecurity landscape continues to evolve, thanks to AI and machine learning. To provide more robust real-time threat detection and response capabilities in the future, CISOaaS offerings will, in all likelihood, leverage these technologies. Wattlecorp’s efforts at protecting your business – SMB or otherwise, also include protecting your sensitive data. Understanding your security needs as our first priority, our vCISO services include encryption and secure cloud migration.
Availing vCISO provides an array of benefits compared to what you can derive when hiring CISO. From offering strategic advice to deriving practical support, vCISO services help ensure expertise, flexibility, and cost-effectiveness. Wattlecorp, one of the leading cybersecurity service providers in India and the Middle East, continues to deliver world-class security services in all efficiency and efficacy. Having built a huge clientele, including Fortune 500 companies, such as Bentley, Walmart, Mercedes-Benz, etc, Wattlecorp has once again proven its knowledge and expertise in providing trustworthy cybersecurity solutions to its clients across the globe.
Being at the forefront of addressing current cybersecurity-related concerns for many of its clients, this UAE-based cybersecurity service provider has also acquired prominence in offering the best vCISO services in the region. Need help with strengthening your cybersecurity posture, but are worried about the expenses your business may incur? Confide in us for all your security-related concerns, and we’ll have our team deployed to your service in no time!
While we process your request, you can, in the meantime, visit our service page, to explore the range of services we have at our disposal. You will also benefit from learning what our vCISO services comprise. Schedule a vCISO and Stay Ahead of Evolving Cyber Threats with us!
CISO as a Service FAQs
1. What exactly is CISOaaS?
CISOaaS (Chief Information Security Officer as a Service) provides businesses with access to top-level cybersecurity leadership without the need for a full-time executive.
2. How does CISOaaS differ from outsourcing?
CISOaaS focuses on outsourcing the roles and responsibilities of a CISO (Chief Information Security Officer). Such an outsourcing facilitates organisations to access/avail cybersecurity expertise and leadership in all its meaning. Whereas, outsourcing in general deals with delegating different processes of a business that make up for its overall operation.
3. Who should consider adopting CISOaaS?
SMBs, enterprises without full-time CISO needs, or any organisation wanting to enhance its cybersecurity posture can benefit from CISOaaS adoption.
4. What are the key benefits of CISOaaS?
Notable benefits to adopting CISOaaS have included:
-Cost-effectiveness
-Scalability
-Access to expert knowledge
-Ability to focus on core business activities.
5. How do I choose the right CISOaaS provider?
You need to look for the following qualities while choosing the one:
-Relevant industry knowledge and experience
-A proven track record
-Relevant certifications
-Ability to align with the goals and values of your organisation.