Table of Contents
Toggle- Implementing Privacy by Design: How to Ensure Compliance with Saudi Arabia’s PDPL
- Introduction to Personal Data Protection Law (PDPL) of Saudi Arabia
- Key Objectives of KSA PDPL Compliance?
- Scope and Applicability of PDPL Saudi Arabia
- Enforcement Authorities for Saudi Arabia PDPL Compliance
- Core Principles of Saudi Arabia Personal Data Protection Law PDPL Compliance
- Rights of Data Subjects Under the PDPL
- Penalties For Non-Compliance with KSA PDPL
- How to Prepare For Saudi PDPL Compliance Implementation?
- Here’s how to prepare for PDPL compliance implementation:
- PDPL Compliance FAQ’s
Implementing Privacy by Design: How to Ensure Compliance with Saudi Arabia’s PDPL
In this digitally evolving world, protecting confidential and sensitive personal data has become an inevitable priority. As data is highly vulnerable to breaches, Saudi Arabia has launched PDPL Compliance, i.e; Personal Data Protection Law. This complete legal framework aims to safeguard privacy and secure personal data.
PDPL Saudi Arabia imposes obligations on private and public entities to give high control over their personal data. In this blog, let’s learn the major compliance needs under PDPL and the practical measures to be implemented for companies to adhere to PDPL Compliance while operating within the Saudi market.
Introduction to Personal Data Protection Law (PDPL) of Saudi Arabia
Saudi PDPL Compliance was launched in 2021 under Royal Decree M/19. This compliance describes personal data as any data that can be used to identify a specific individual, irrespective of its form or source. It can also be data that can directly or indirectly be used to identify a person’s name, ID, addresses, contact information, licenses, personal details, bank or card numbers, records, images, or videos of the individual.
Also, the sensitive personal information such as genetic data, ethnicity, criminal status, religious identity, health information, etc; is also subject to mandatory controls as these are potentially damaging.
This unified framework constitutes the way confidential data needs to be collected, processed, stored, or shared along public/private networks.
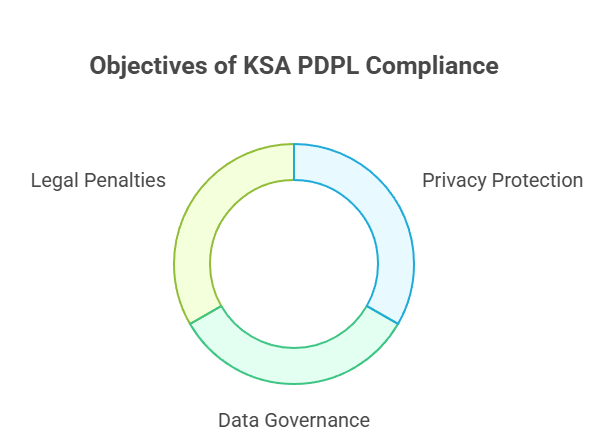
Key Objectives of KSA PDPL Compliance?
• To protect a person’s privacy and the authority over their personal information.
• To control and oversee how the organizations gather, utilizes, stores, or discloses the personal and critical data.
• To impose legal penalties in case of violations, like fines and criminal liabilities.
Scope and Applicability of PDPL Saudi Arabia
Any company/business managing the confidential data of Saudi residents should adhere to PDPL regulations. It has a wide reach that covers many areas including healthcare, employment, finance, and more. It involves a Data Protection Officer to manage data handling records. This helps to prevent fines and secures personal data.
Also Read : Ensuring Data Privacy Compliance: Essential Steps for Your Business
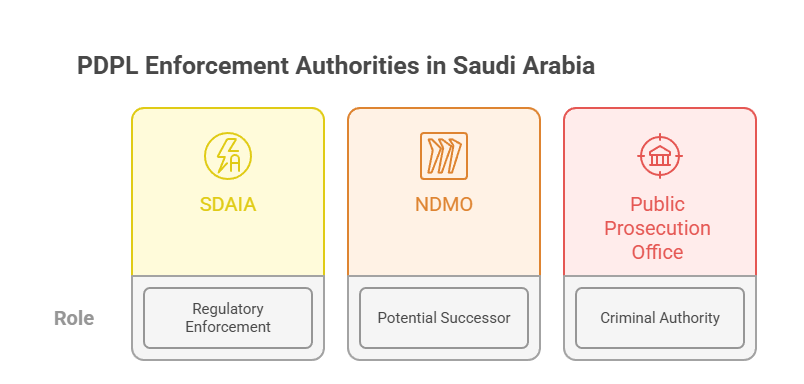
Enforcement Authorities for Saudi Arabia PDPL Compliance
• Public Prosecution Office: Manages criminal investigations and prosecutions related to the illegal use of personal data.
• NDMO (Potential Successor): The National Data Management Office takes over from SDAIA afterwards.
• SDAIA ( Regulatory Enforcement): The Saudi Data and AI Authority oversees PDPL enforcement for the first two years.
Core Principles of Saudi Arabia Personal Data Protection Law PDPL Compliance
Saudi Arabia PDPL revolves around various foundational principles for personal data management depending upon transparency, fairness, necessity, accountability, and several other factors as follows:
1. Lawful Basis & Fairness
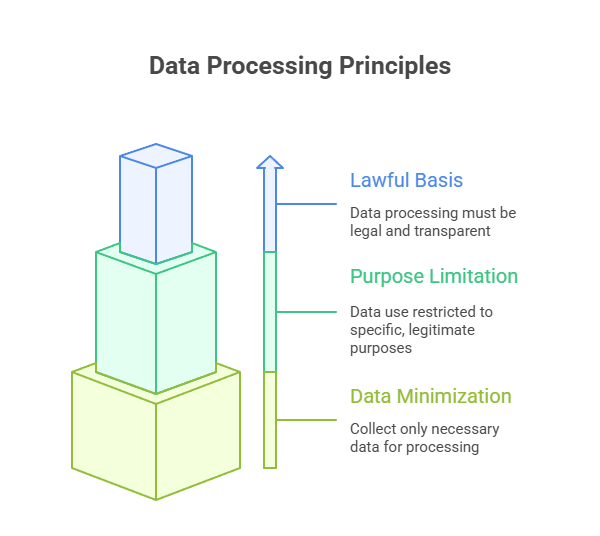
Data Controllers should gather and process personal data fairly, legally, and transparently. It must achieve valid consent or depend on lawful practices like legal or contractual obligations. This is subject to safeguards and exclusions for sensitive information. Also, consent is not always necessary where other lawful bases are applicable.
2. Purpose Limitation
Data Controllers should gather and process personal information to manage legitimate, specific, and particularly stated purposes. Any processing that could deviate from the actual purpose demands a lawful and renewed consent and should fall under any exception as PDPL mentions. Processing should not hinder or contradict any legal obligations.
3. Data Minimization
Data Controllers should collect and retain only limited data that helps attain a particular and lawful processing need. They should document the necessity of every data collected. Any irrelevant, unwanted or extreme form of data collection is not encouraged as stated in Implementing Regulation Article 19.
4. Purpose, Relevance & Accuracy
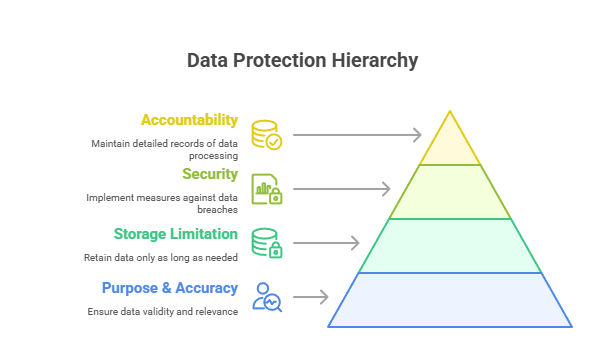
Data Controllers need to confirm that the personal data is valid, up-to-date, and true to serve the purpose of processing. As per Article 14 PDPL, Data Controllers should verify data quality before processing. If the data is found to be outdated or invalid, PDPL Article 17 mandates the Controller to make corrections and notify all entities that received the data previously.
5. Storage Limitation
Data Controllers should retain personal details only for the period for which it is required to fulfil the actual collection requirements. If the purpose no longer exists, data needs to be destroyed securely with no undue delay. An exception arises only when a specific legal, judicial requirement, or regulatory decision applies. Even under such circumstances, data needs to be deleted after the lawful basis ceases.
6. Security
Data Controllers should deploy accurate technical, organizational, and administrative processes to secure personal data against any potential breaches, illegal access, and misuse. Controllers are responsible for following security standards issued by the NCA ( National Cybersecurity Authority) or cybersecurity best practices to minimize data breach risks.
7. Accountability
Data Controllers should keep accurate and detailed records of every personal data processing operation. These records should be readily accessible for SDAIA and include information like data categories, use of processing, recipients, data transfers outside KSA, timelines of retention, etc.
Rights of Data Subjects Under the PDPL
As per PDPL, individuals can enjoy several rights regarding their personal data. Organizations must inform users about these rights and make sure they can exercise these within 30 days.
• Individuals have the right to be informed about the legal functional basis for processing their personal information.
• Individuals have the right to request access to their personal information and a copy, free of charge.
• The individuals can request corrections to their confidential data if incomplete or incorrect.
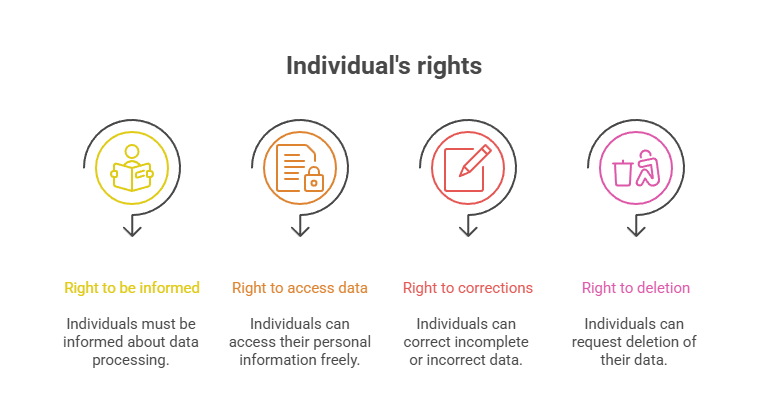
With these rights, individuals can oversee their personal data with high protection. Also, organizations should facilitate these rights efficiently and transparently.
Penalties For Non-Compliance with KSA PDPL
• Unauthorized data transfers beyond Saudi Arabia can cause 1 year imprisonment and /or penalties of SAR 1 million [~ USD 2,67,000].
• Disclosing sensitive confidential information can end up in 2 years imprisonment and/or SAR 3 million penalty costs.
• SDAIA can impose fines of about SAR 5 million in case of violation of the law.
Steps to Follow When a Breach of PDPL Occurs
• Inform SDAIA and the people affected within 72 hours
• Create detailed reports that state the breach, its nature, scope, and the measures adopted to eliminate its effects.
• Perform risk evaluations to understand the possibility and the effect of the security breach.
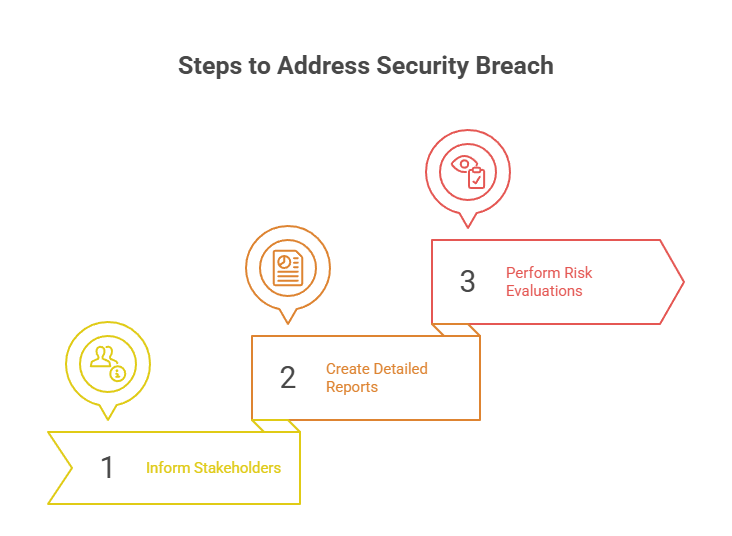
By following the PDPL Privacy-by-Design framework, you can keep the personal information of people in Saudi Arabia highly secure. This helps to align with the Saudi Arabia data protection legislation regulations.
How to Prepare For Saudi PDPL Compliance Implementation?
You might have this question in mind: What are the best practices to achieve effective compliance? We have the answer simplified for you.
Organizations should implement and regularly update a comprehensive data protection policy without fail to manage their compliance posture.
It is critical to integrate privacy-by-design and privacy-by-default into your services and systems from the outset. In addition to the significance of employee training and awareness programs, technical safeguards like access controls and encryption also play a major role.
Effective compliance is a combination of various critical elements, including keeping detailed data processing and legal justification records, and preparing incident response plans.
Also Read : Cybersecurity and Data Privacy Regulations: Understanding the Connection
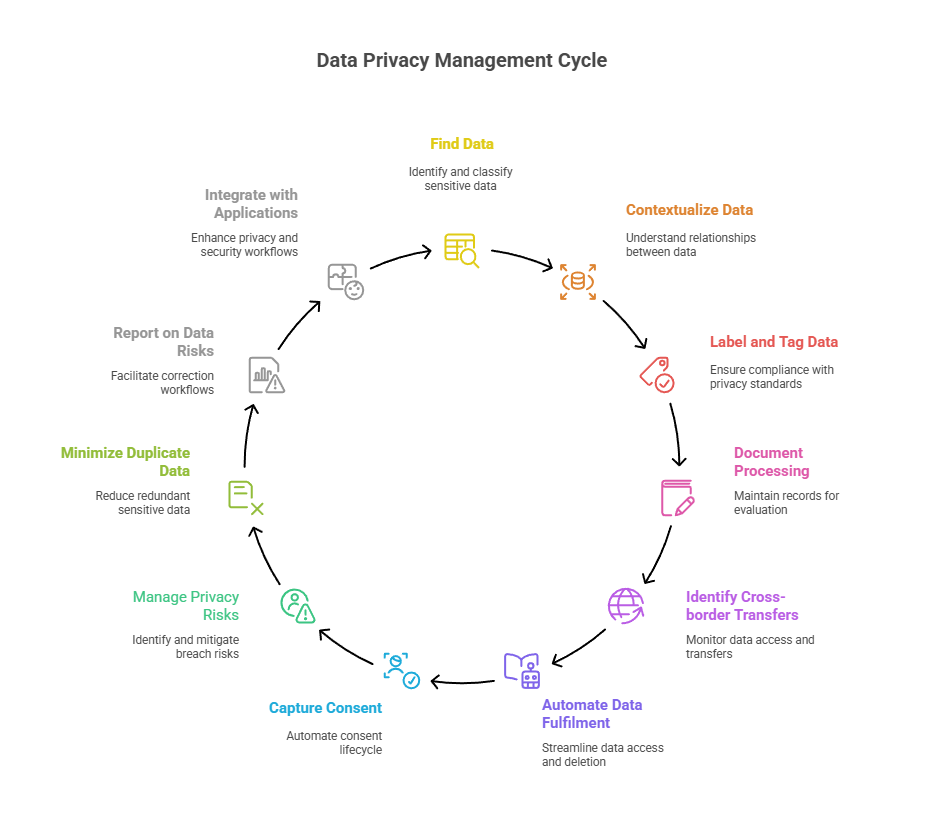
Here’s how to prepare for PDPL compliance implementation:
- Find the data: Identify the confidential information and classify most sensitive data.
- Contextualize the data: Learn the relationships between data by combining context with personal and sensitive information.
- Label and tag data: Make sure that the information is processed adhering to the privacy standards.
- Document record of processing activities: Keep a Record of Processing Activities ( RoPA) which can evaluate the data assets, extent of breach, location, information sharing, data transfers, and PIAs.
- Identify cross-border data transfers: Monitor data access, data transfer violations, and usage across the organizations to take proper action.
- Automate data fulfilment: Replace manual fulfilment of individual data access or deletion requests with automation.
- Capture consent: Automate preferences and consent lifecycle across applications, channels, and systems. This consists of consent for the following: ad targeting, direct marketing, cookies, private/sensitive data processing, and more.
- Manage privacy risks: Identify, segregate, and map data to create controls over breach risk reduction and achieve PIA( Privacy Impact Assessments).
- Minimize duplicate/sensitive data: Ensure duplicate identification and utilize retention practices for data minimization.
- Report on data risks: Facilitate correction workflows and check if sensitive data gets captured.
- Integrate with applications: Improve existing privacy, management, security, and workflows.
Saudi PDPL regulations are taking their turn with companies to keep up with the changes. As the world focuses on data ethics and security on a higher level, Saudi Arabia’s rules can get stringent. Businesses need to change the way they manage data to follow Saudi PDPL implementing regulations.
As Saudi Arabia tightens the compliance requirements for data privacy at the helm, the PDPL law acts as a strategic necessity. With PDPL compliance services in KSA from a reputed company like Wattlecorp, you can meet your evolving compliance needs while ensuring that the data remains protected at every level. To learn more about how we offer PDPL compliance solutions in KSA, let’s connect!
PDPL Compliance FAQ’s
1.Is GDPR only needed for PDPL in Saudi Arabia?
No. GDPR compliance is not just enough to maintain Saudi PDPL regulations. Though it ensures a foundation, organizations should follow Saudi Arabia’s detailed legal and regulatory standards for a complete PDPL compliance.
2.What is the Privacy by Design framework in Saudi Arabia’s PDPL?
As a core principle of Saudi Arabia’s PDPL, Privacy by Design helps organizations integrate data protection measures into their systems or operations from scracth instead of afterthought. It focuses on proactive risk mitigation and secures the personal data throughout the lifecycle.
3.Why is Privacy by Design an important factor for Saudi PDPL compliance?
As it illustrates a firm’s commitment to data minimization, user consent, and transparency, adopting Privacy by Design is necessary for Saudi Arabia PDPL compliance . It helps businesses get rid of violations while making privacy an ultimate priority.
4.How does Privacy by Design protect personal data under the Saudi PDPL?
Privacy by Design secures personal data through principles like access control, data encryption, and data minimization. As a cybersecurity company, we help businesses integrate these principles via secure architecture, policy implementation, and regular risk assessments.







