Key Takeaways:
- Neglecting audits can lead to preventable crises as shown by the Louvre’s security failures. This emphasizes the need for regular compliance audits.
- Governance gaps and lack of continuous monitoring are common issues that expose organisations to security risk that leads to vulnerability to security risks and potential breaches.
- Industries like SaaS/BFSI firms must integrate compliance with cybersecurity. Cybersecurity consultants and pentesters are key to keeping your organization in full protection.
- Continuous audits assists in building trust, resilience, and maintaining long-term compliance.
Table of Contents
Toggle- Hidden cost of ignoring Cybersecurity Audits: A Compliance Consultant’s View
- What is a compliance audit?
- The Louvre case: What went wrong?
- Key findings revealed from the audit
- Why organisations in SaaS/BFSI must pay attention
- Role of a compliance consultant in audit to remediation
- Align Your Audits with cybersecurity framework
- The Role of Penetration Testing in Audit Follow up
- How Wattlecorp Ensure Cybersecurity Compliance Audit
- Compliance Audit FAQ
Hidden cost of ignoring Cybersecurity Audits: A Compliance Consultant’s View
Do you know what happens when you ignore an audit?
The Louvre incident opens our eyes and shows that a simple security mistake may cost serious loss.
Everyone started discussing the importance of cybersecurity even after the physical robbery. Actually, thieves didn’t hack or find out their weak passwords, they just tried physical robbery.
But when investigators looked deeper on security, the old cybersecurity mistakes came up again.
Suddenly, the story changed completely and I realized that the museum ignored security basics.
Cybersecurity compliance is becoming more and more essential to keep our data safe and secured from the unexpected cyber attacks. Therefore, it is important to understand the disadvantages of ignoring audits.

At wattlecorp, we believe in our cybersecurity solutions to keep your business protected from threats of various size and scope, which helps you save millions of dollars in losses and facilitate stress-free day-to-day business operations.
Maintaining regulatory compliance can be a headache for businesses. Security can be tricky stuff.
To make your system secure, you need to go through a laborious and time-consuming audit process. And even then, you might not have a full picture of your current state.
The purpose of the audit is to ensure that all our systems, processes and data are in proper shape and secured.
When this audit is ignored, you may experience or miss the early warnings of threats. Avoiding these mistakes can lead to serious issues such as:
- Data breaches or cyberattacks
- Financial losses from theft or system downtime
- Legal penalties for non-compliance
- Reputation damage due to public exposure
At Wattlecorp, we provide comprehensive compliance services that are aligned to cybersecurity policy and regulations to safeguard your data from unexpected threats.
What is a compliance audit?
Have you ever thought about what is compliance audit and why is it so important?
Compliance audits are formal reviewing of an organization’s internal and external activities, policies, standards and regulations. It includes areas such as cybersecurity, data privacy, financial reporting, health and safety.
Regular compliance audit is necessary and following an effective compliance management system supports the protection of sensitive information based on organization’s environmental regulations.
Also Read : Why Website Security Matters: A Complete Guide
The Louvre case: What went wrong?
The Louvre museum robbery happened on October 19 when two of the thieves cut through a window on the second floor of the museum and pulled jewelry out of two glass cases in the Apollo Gallery on that floor, according to the authorities.
Let’s be honest, the Louvre case wasn’t just about smart thieves or stolen art.
It’s all about neglecting the security warnings.
When investigating the surveillance security, they realized they used very weak security passwords.
Louvre’s most foolish act of keeping their CCTV server kept their password as “louvre” itself.
The real issue wasn’t just the heist, it was the realization that years of ignoring the fundamental security measures that had decreased the trust and left the Louvre exposed.
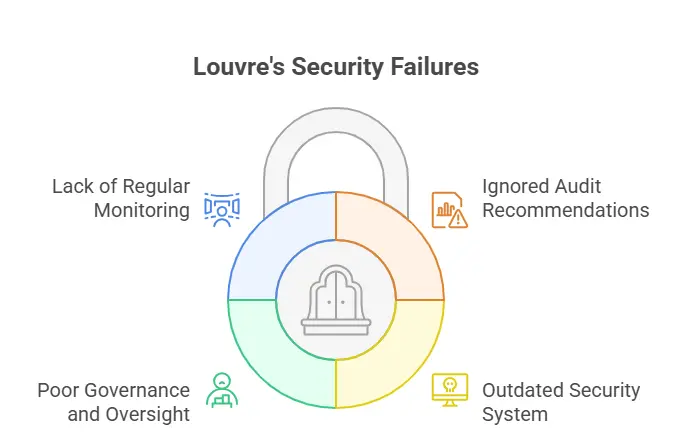
- Ignoring the audit recommendations
- Outdated security system
- Poor Governance and Oversight
- Lack of regular monitoring
These are the most common mistakes which severely affect our security.
Key findings revealed from the audit
The Louvre’s audit revealed a pattern of ignoring issues such as governance failure, weak infrastructure, monitoring blind spots which really weakened its defenses.
- Governance Failures: Audits assist to reveal lack of defined ownership for security and compliance operations, when the audit recommendations rarely moved beyond paperwork.
- Weak Infrastructure: Many of the Louvre’s core systems were outdated, poorly maintained, or running on legacy hardware. All these mistakes give a chance to modern attackers to exploit.
- Monitoring Gaps: Inactive security cameras, logs went unchecked, fail to connect alert system with central dashboard. And also delay in action for unnoticed suspicious activity.
Cybersecurity compliance audits ensure to identify the most common security mistakes and provide accurate remediation for that.
Why organisations in SaaS/BFSI must pay attention
For SaaS and BFSI organisations, both deal with sensitive information, finances, and 24-hour work. One missed audit observation or failure to apply patches in time may result in compliance breaches to colossal data breach.
Trust erosion is the major risk in SaaS. In that case where the clients rely on the integrity of data, a single compromise may destroy decades of trust within seconds.
The reputational and regulatory is the risk in BFSI. And not taking action on the results of audits does not lead to cyberattacks but also to complications such as fines, investigations, and customer panic.
Also Read : How Industry-Specific VAPT Solutions Secured Payment App For A Financial Enterprise
Role of a compliance consultant in audit to remediation
Audits point out what’s broken, where it is and how to fix it. Here comes the relevance of compliance and resilience.
What does a compliance consultant really do?
Actually the compliance consultant makes a bridge from audit to remediation, which assists to identify the gaps and provide real world solutions. These findings help to provide clear action plans.
They assess the risks with prioritise the remediation based on the impact and fix it with relevant regulations or frameworks such as ISO 27001, SOC 2, NESA IAS, or PDPL.
Align Your Audits with cybersecurity framework
To ensure your organisation to stay secure, accountable, and resilient we need to keep connected with both compliance audit and cybersecurity compliance framework.
How well do you know the link between compliance audit & cybersecurity compliance framework works?
A compliance audit measures how well your policies, configurations and daily operations align with the requirements. This link between compliance audit and cybersecurity compliance supports compliance to strategic advantages.
The Role of Penetration Testing in Audit Follow up
Compliance audits focus more on the security vulnerabilities. At Wattlecorp, our penetration testing experts prioritize audits to validate every fix and simulate real-world attack scenarios across networks, applications, APIs, and configurations.
We ensure your systems can withstand actual cyber threats. By combining post-audit testing with continuous monitoring, Wattlecorp helps organisations to turn compliance into a proactive defense mechanism.
How Wattlecorp Ensure Cybersecurity Compliance Audit
The Louvre museum incident reminds us of a simple fact that security fails when warnings are ignored at the right moment.
Ignoring the audit recommendations, outdated security system, poor Governance and oversight and lack of regular monitoring are the most common mistakes which severely affect our security.
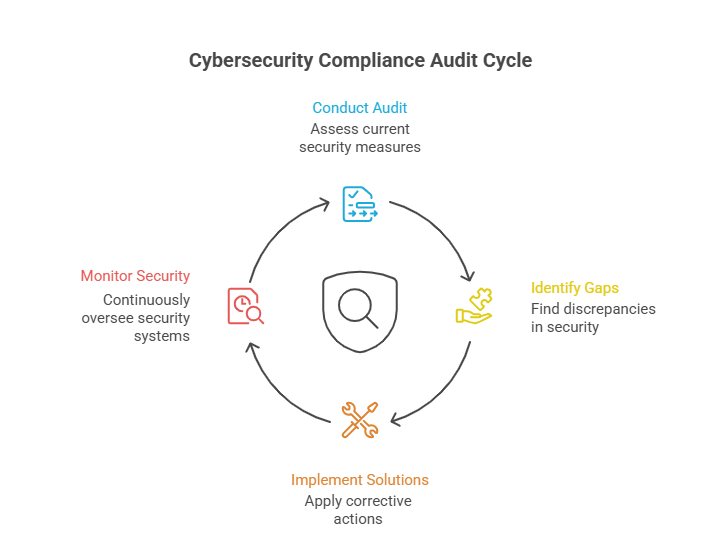
There comes the importance of having a security audit. With a strong cybersecurity compliance, organizations can protect digital assets and ensure security policies are regularly audited to prevent vulnerabilities and potential breaches.
Whether you’re a SaaS platform managing user data or a financial institution, which prioritizes guarding customer trust, a security audit is not just a report, it checks and tells you where you stand and what needs fixing before something breaks.
Also Read : Fintech Penetration Testing in the UAE: A Complete Security Assessment Case Study for Digital Banks
At Wattlecorp, we specialize in comprehensive cybersecurity compliance audits to ensure organizations keep their data protected from cyber attack. Our experts support identifying the gap between audit finding and providing actionable solutions.
Secure Your Digital Assets with Wattlecorp’s Cybersecurity Compliance Audits.
Compliance Audit FAQ
1. What is a compliance audit and why is it critical for organisations?
A compliance audit examines that organisation is adhering to legal, regulatory and in-house policies. It assists in lowering the risks, process enhancement, the development of trust and avoiding legal penalties. Providing early visibility into the security and process gaps, organisations can correct them before it leads to security threats.
2. What role does a compliance consultant play in preventing such failures?
A compliance consultant makes sure that audits are complete and assists to take corrective measures to close the gaps between audits and remediation with implementing realworld solutions. Translating complex regulatory and analysing audit findings into practical roadmaps that align security, compliance, and business priorities.
3. How does a cybersecurity compliance framework tie into physical security audits?
Cybersecurity compliance ensures both digital and physical protections to work together to safeguard an organisation’s sensitive data and assets. When mapped to physical security controls, these frameworks help create a unified security posture where access, monitoring, and incident response are consistent across both worlds.
4. When an audit identifies gaps, what are the next steps organisations should take?
Organisations should prioritise to focus on the risks and create a remediation plan with fixing critical issues immediately, implement long-term security improvements and validate that the gaps are closed. Wattlecorp ensures continuous support for each step from rapid fixes to compliance alignment and continuous monitoring.