The importance of ensuring the security aspects of a SaaS application is significant enough to not ignore it in the first place. Securing a SaaS application isn’t optional—it’s a necessity. Ignoring it can leave businesses open to serious cyber threats.
Many companies rely on the SaaS Security Checklists as a structured way to protect their systems. But with cyber threats constantly evolving, it’s important to assess how effective this checklist really is. At the same time, businesses need to separate facts from misconceptions to make the most of this tool. Understanding its strengths and limitations helps companies use it more effectively and strengthen their security.
Table of Contents
ToggleUnderstanding SaaS Security Checklist
- Defining SaaS Securing Checklist
The SaaS Security Checklist can be defined as a methodical strategy to assess and improve the security of SaaS apps. Creating a SaaS Security Checklists mandates employing best practices, including undertaking regular audits, applying access control, encryption, and adhering to specific compliance standards. The customized checklists we created have been found to comply with international regulations, including, but not limited to GDPR, HIPAA, and SOC2. CTOs and CISOs can also use these checklists as effective reference points to ensure their SaaS solutions have clear safety and legal parameters.
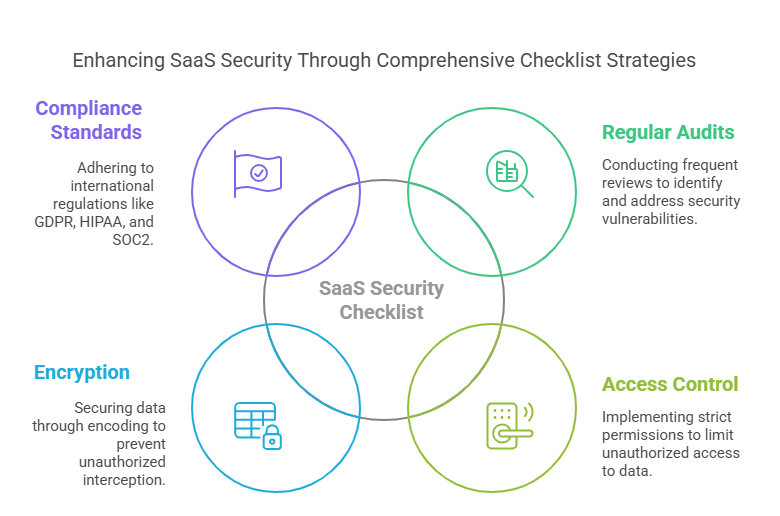
SaaS Security Checklist Facts: What Works
The role of SaaS Security Checklists in modern cybersecurity needs to be examined—are they truly essential, or just another industry buzzword? According to Wattlecorp’s security experts, these checklists can be highly effective when used in the right areas. Here’s where businesses can benefit the most:
- For Enhancing Compliance
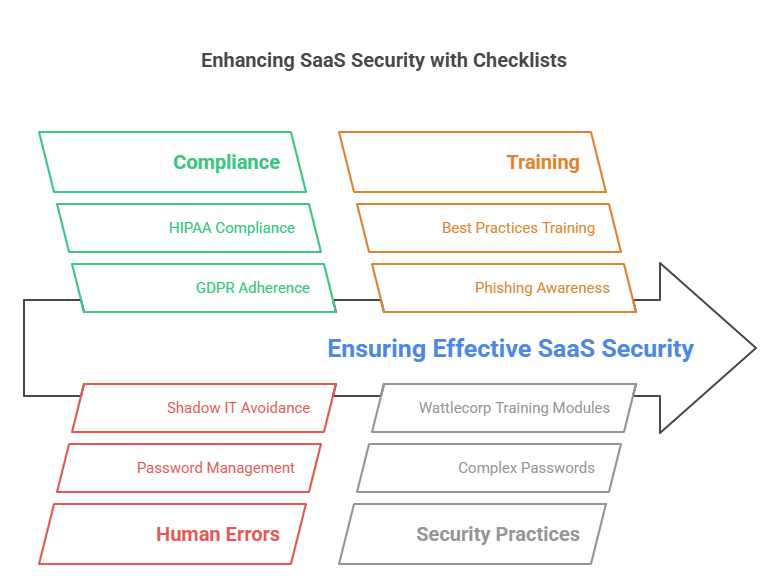
Understandably, ensuring compliance is a must for companies handling sensitive data, Utilizing a SaaS Security Checklists in such a scenario guarantees the adherence of your SaaS tools to legal specifications, such as:
1. GDPR (General Data Protection Regulation): For European markets, also taking into consideration the EU residents.
2. HIPAA (Health Insurance Portability and Accountability Act): HIPAA is all about protecting sensitive patient health information as laid down by the United States Law.
3. PCI-DSS (Payment Card Industry Data Security Standards): Security guidelines that are designed to safeguard cardholder data and payment card information by reducing credit card fraud risk.
- Reducing Human Errors
The fact that human-bound mistakes account for the highest degree of data breaches cannot be denied. Incorporating SaaS Security Checklists into organizational procedures by training teams on best practices can be a one major leap to ensuring data security compliance.This means using strong, complex passwords, avoiding shadow IT, identifying phishing scams, and making the most of Wattlecorps training modules for better security.
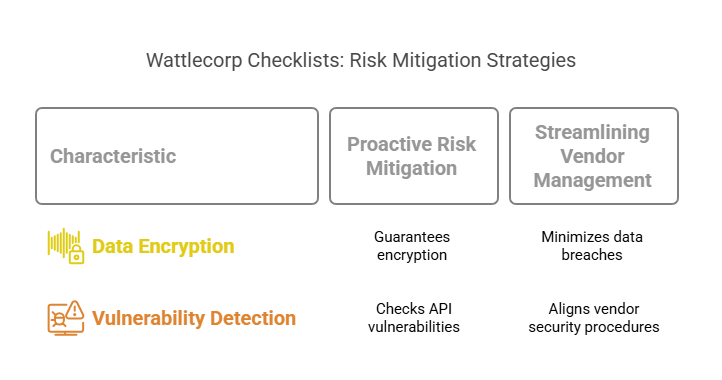
- Proactive Risk Mitigation
Checklists prepared by the Wattlecorp experts embedded with sophisticated solutions can effectively help SaaS companies locate vulnerabilities before being exploited. These help with:
- Guaranteeing encryption for both at-rest and in-transit data.
- Being intuitive enough to check for vulnerabilities and incorrect setups in APIs.
- Streamlining Vendor Management
The shared responsibility approach that SaaS companies frequently use strongly warrants data protection.
This means that even vendors can access critical information, calling for significant risks and threat to sensitive data. Customized checklists prepared by the Wattlecorp team can effectively guarantee aligning the vendor’s security procedures to that of your company, thus minimizing risks related to data breaches.
| Category | Checklist Item | Action Required |
| Data Protection | Encrypt data at rest and in transit | Utilise tools, such as AES-256 for data encryption and TLS 1.3 for data transmission. |
| Regular updation of encryption protocols | Upgrading outdated algorithms, say 3DES to AES or RSA-2048. | |
| Implementing secure backups | Implement the 3-2-1 backup rule to maintain data in three copies – storing 2 on different media and 1 with a separate storage infrastructure for backup | |
Identity and Accessibility | Enforcing Multi-Factor Authentication (MFA) | Using two or more factors like biometrics or authentication apps. |
| Implementing Role-Based Access Control (RBAC) | Assigning permissions based on roles and responsibilities. | |
| Reviewing and revoking outdated access | Regularly audit and remove access for ex-employees or outdated accounts. | |
| Adopting Zero-Trust Architecture | Continuously verifying access regardless of network location. | |
| API Security | Monitoring and scanning APIs for vulnerabilities | Utilizing automated tools for regular scans and updates. |
| Secure APIs with OAuth 2.0 and Mutual TLS | Implementing strict authentication and rate-limiting policies. | |
| Incorporating real-time API monitoring | Tracking traffic patterns to detect anomalies or breaches. | |
| Compliance and Audits | Aligning with industry standards | Ensuring compliance with GDPR, HIPAA, SOC2, or PCI-DSS as applicable. |
| Conducting regular security audits | Performing third-party penetration tests and vulnerability scans. | |
| Evaluating application-specific risks | Assessing risks, such as misconfigurations and shadow IT for each SaaS app. | |
| Endpoint Security | Enabling full-disk encryption on all endpoint devices | Encrypting laptops, smartphones, and any connected IoT devices. |
| Installing endpoint detection and response (EDR) tools | Using antivirus and malware detection software. | |
Updating device software regularly | Patching vulnerabilities through frequent updates. | |
| Incident Response | Developing an Incident Response Plan (IRP) | Defining steps for detection, containment, recovery, and reporting. |
| Testing disaster recovery procedures | Conducting regular drills to ensure preparedness. | |
| Implementing automated data backup solutions | Using tools to ensure daily backups and quick restoration processes. |
SaaS Security Checklist Myths: Separating Fact from Fiction
It is disappointing to note that sometimes SaaS Security Checklists are misinterpreted despite the benefits that are linked with them. Thanks to Wattlecorp’s tech team’s expertise in this regard, for it can genuinely assist its clients in distinguishing facts from myths in the following ways:
Myth: A Checklist Solves All Security Problems
Facts: A checklist is not a solution, but a tool. Security is a continuous process that requires user knowledge, upgrades, and monitoring. In its offering of managed services, Wattlecorp guarantees continued proactiveness with this procedure.
Myth: SaaS Providers Handle All Security
Fact: The shared responsibility approach undermines SaaS security. Businesses need to safeguard their data by controlling user access while providers secure the infrastructure. The specialized tactics that Wattlecorp use help close security gaps.
Also Read :What is SaaS security posture management? A Basic Guide
Myth: A one-Size-Fits-All Checklists Work
Fact: Every organization has its own security needs – whether it be one offering SaaS solutions or any other for that matter. Understanding this fact would be enough to create security checklists that well fulfills the purpose. Wattlecorp offers tailored solutions when it concerns with preparing specialized checklists for industries adhering to SOC2 for tech firms or HIPAA for healthcare,
Myth: Checklists Replace Expert Oversight
Fact: SaaS Security Checklists can never be a substitute for expert oversight even though these help businesses review the security efficacy of SaaS applications. Penetration testing and vCISO services delivered by Wattlecorp provide more in-depth understanding-cum-insights on vulnerabilities existing there.
Also Read: Future-Proofing SaaS Security: The Role of an Annual Security Program
To summarize, the effectiveness of SaaS Security Checklists lies in how appropriately and efficiently your SaaS business can utilize them. In other words, if this tool is used in the way it should be, the answer to the above query would be a resounding YES. Wattlecorp, having realized the value of a SaaS Security Checklist in protecting SaaS applications, has well understood that integrating this specific tool into a more comprehensive and proactive cybersecurity plan is key to protecting your SaaS-related business operations.
Secondly, being aware of the particular difficulties that companies face when protecting their SaaS apps, Wattlecorp has been observed to fuse customized checklists, cutting-edge tools, and professional monitoring to ensure that these are optimal enough to secure the various SaaS applications. So, are you willing to protect your SaaS platform the way it should be? Get in touch with us right now and we will be glad to help you prepare SaaS Security Checklists that cater to the security requirements of your SaaS applications. Do visit our SaaS security webpage to book for this specific service and our security professional will be there for you at the earliest.
SaaS Security Checklists FAQs
1. What are the key components of a SaaS Security Checklist?
From what could be observed through the table presented above, data encryption, access control, compliance adherence, and frequent audits are essential elements of a typical SaaS Security Checklist.
2. How effective is a SaaS Security Checklist for businesses?
The SaaS Security Checklist is extremely efficient and helpful when you integrate cutting-edge security measures. However, you may need to customize the checklist to meet particular business needs with equal importance to frequent updations.
3. What are common myths about SaaS Security Checklists?
Common myths or misconceptions include the thought that providers can handle all types of security vulnerabilities with SaaS applications, that a ‘one-size-fits-all’ checklist is sufficient, and lastly, security checklists can replace expert oversight.
Replacing these notions with intuitiveness regarding the efficiency of a checklist and customizing the same with specific business needs is key to obtaining a 360-degree functional SaaS security checklist.