Key Takeaways:
- SAMA audits play a critical role in safeguarding sensitive data, strengthening risk management, and enhancing cybersecurity practices across Saudi Arabia’s financial sector in an increasingly digital environment.
- Financial institutions must comply with SAMA’s audit requirements to safeguard sensitive data, personal details in this rapidly growing digital world.
- SAMA examiners focus on critical areas targeted by examiners of the SAMA include risk management, resilience of operations, governance, consumer protection, and third-party cybersecurity, and organizations are expected to reach at least Level 3 maturity.
- The SAMA audit preparation involves systematic steps such as gap analysis, internal testing, VAPT and continuous monitoring. With expert guidance from Wattlecorp, organizations can enhance compliance readiness and increase their chances of audit success.
- SAMA audits are critical for improving cybersecurity in Saudi Arabia’s financial sector. They use strong risk management and digital security steps. These audits require following the SAMA Cybersecurity Framework. They handle threats like ransomware and phishing with gap analysis and VAPT.
Table of Contents
Toggle- How SAMA Audits Define the Future of Saudi Arabia’s Financial Cybersecurity
- Which Organizations Need to Comply with SAMA Audit Requirements?
- The Key Focus Areas that SAMA Examiners Focus on Most
- Decoding the SAMA CSF Maturity Model with Levels, Evaluation and Growth
- The Step-by-Step Process of SAMA Audit and Its Timelines
- Preparing for a SAMA Audit: From Gap Analysis to Internal Testing and VAPT
- Strengthening SAMA Compliance with Expert VAPT Services in Saudi Arabia
- A Realistic Walkthrough: What a SAMA Audit Looks Like in Action
- Strengthen Compliance with Wattlecorp’s Expertise
- SAMA Audit FAQs
How SAMA Audits Define the Future of Saudi Arabia’s Financial Cybersecurity
In Saudi Arabia’s fast-growing financial world, the SAMA audits protect the security of tomorrow’s banking. The SAMA, or the Saudi Arabian Monetary Authority, is the country’s primary monetary authority.
The key advantages of SAMA audit are:
- Protected Digital Assets
- Easier Risk Management
- Defensive Against Cyber Threats
- Alignment with Global Cybersecurity Standards
- Improved Customer and Investor Trust
- Increased Operational Resilience
- Competitive Advantage in a Regulated Market
SAMA Audit framework ensures financial institutions to strengthen their risk management, secure digital systems and security practices.
Through regular audits and continuous monitoring, SAMA Audit guarantees that cybersecurity becomes a core operational priority, which supports both improving the protection of financial data and maintaining trust across the sector.
Which Organizations Need to Comply with SAMA Audit Requirements?
Protecting sensitive data has become a core priority in this rapidly growing digital system across Saudi Arabia.
The SAMA compliance in KSA is a key concern for organisations, financial institutions, and government bodies to keep our sensitive data protected and cyber risks minimized.
Yet, many organizations still lack clarity on whether these regulations apply to their operations.
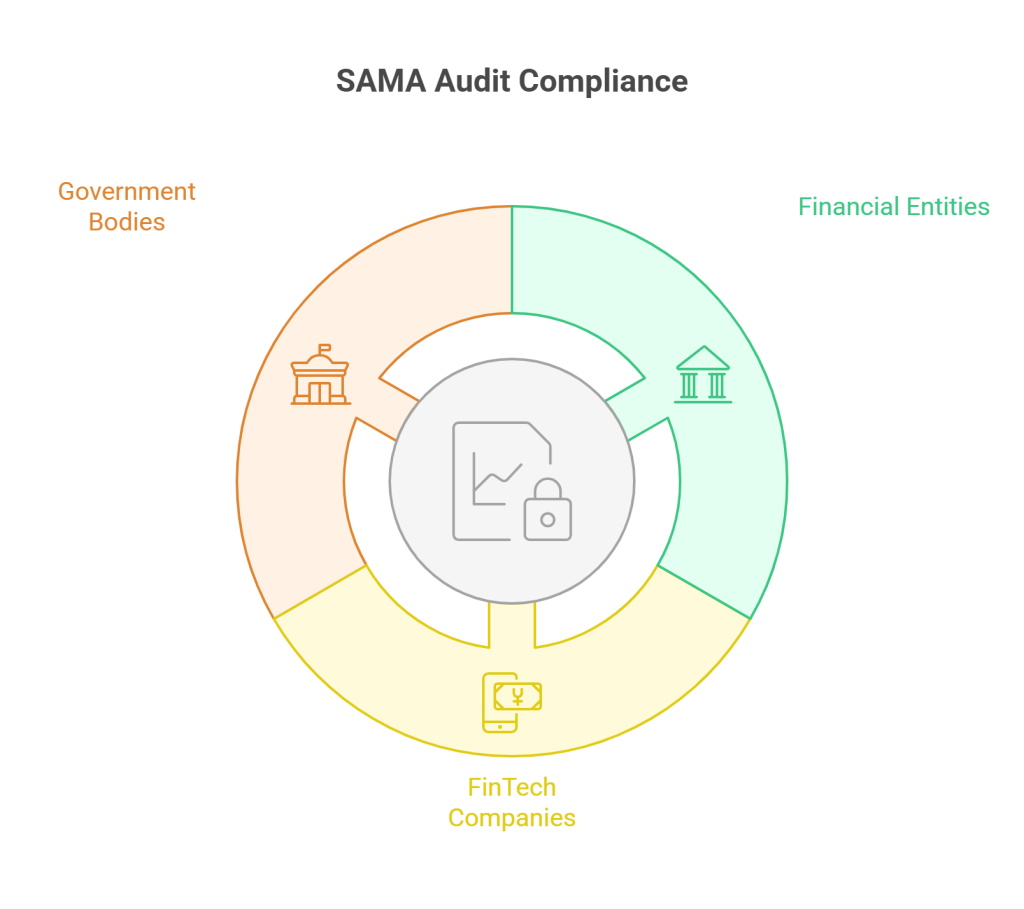
The Cybersecurity Framework of SAMA requires that all the financial entities such as banks, insurance or reinsurance companies and financing companies in Saudi Arabia are audited.
Fintech companies and payment service providers as well as subsidiaries need to be aligned with CSF controls in leadership, risk management and third-party supervision.
The Key Focus Areas that SAMA Examiners Focus on Most
What do SAMA examiners actually check during an audit?
The purpose of SAMA compliance regulation is to ensure the best practices for financial institutions for securing digital assets by following the highest global security standards.

While the SAMA Audit process, consider to prioritize key focus areas that should focus more by the SAMA examiner.
- Risk management
- Data security and operational resilience
- Governance and Internal Controls
- Consumer Protection
- Third-Party Cyber Security
While focusing on these focus areas, SAMA examiners prioritize to check that organisations have reached at least Level 3 cybersecurity maturity, where the security processes are structured, formally documented and consistently monitored instead of relying on traditional approaches.
Decoding the SAMA CSF Maturity Model with Levels, Evaluation and Growth
SAMA CSF Maturity model includes 6 maturity levels under Saudi Central Bank (SAMA) to measure and improve cybersecurity capabilities in financial sectors. These financial institutions are required to operate at a minimum of Maturity Level 3 under the SAMA framework. It includes well-documented cybersecurity controls that are consistently applied across the organization.
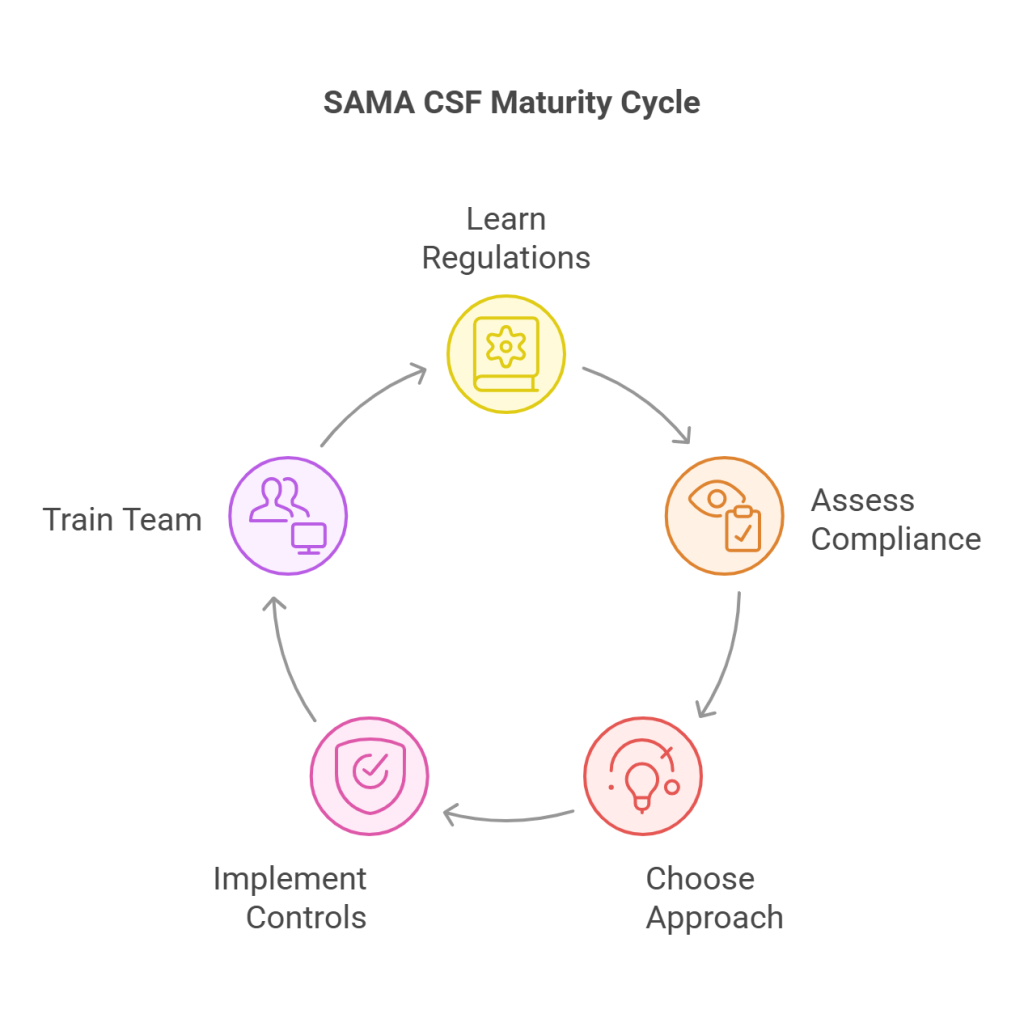
Step 1: Learn about SAMA CSF regulations
Step 2: Implement a comprehensive compliance assessment
Step 3: Choose the best compliance approach
Step 4: Implement Compliance Controls
Step 5: Provide Team Training
SAMA auditors follow these steps and evaluate the current maturity and also ensure to meet the institution’s cybersecurity roadmap, which is aligned with future maturity targets.
The Step-by-Step Process of SAMA Audit and Its Timelines
SAMA audit is generally a systematic procedure that promotes transparency and structural clarity.
The process of the audit begins with a formal notification alerting. Subsequently auditors clearly outline the scope and demand documents to be reviewed.
Organizations make sure that they submit cybersecurity-related policies, procedures, asset inventories, logs and risk registers.
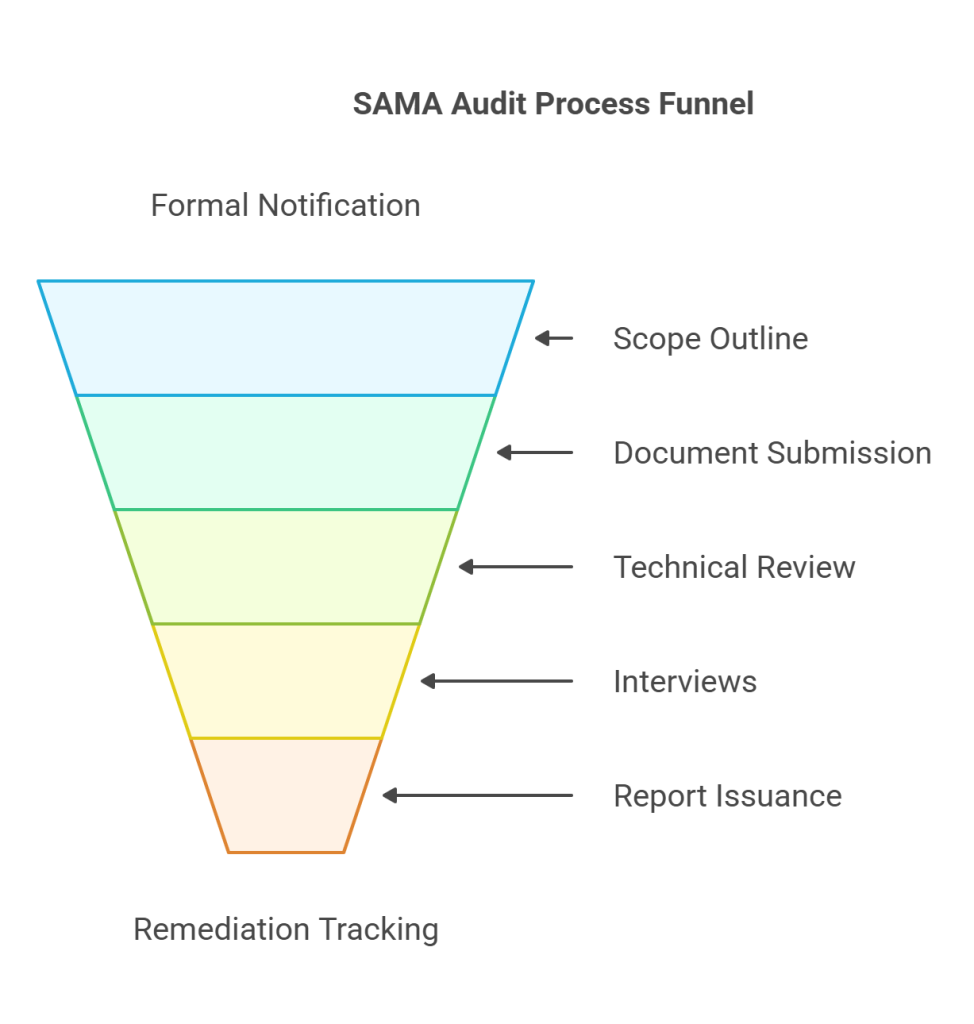
After reviewing the documents, auditors confirm the technical controls and interview critical individuals, including the CISOs, IT managers, compliance officers and executives both on site and remotely to evaluate their level of readiness to the overall cybersecurity.
SAMA timelines are not set for a single, universal audit date for all regulated entities, it mandates that organizations establish their own regular, risk-based audit cycles.
It includes: pre-audit self-assessment, internal audit, external auditor appointment, field inspection, report issuance and remediation tracking.
Identification of gap assessment, documentation process, and remediation are the typical preparation phases for preparing SAMA audit.
Preparing for a SAMA Audit: From Gap Analysis to Internal Testing and VAPT
Financial institutions get practical advice here on getting ready for SAMA audits.
Start by running a gap analysis to spot differences between existing controls and SAMA standards.
Next comes internal audits to check if policies work in practice.
Finish with Vulnerability Assessment and Penetration Testing (VAPT) to identify attacks early and find hidden flaws.
Top SAMA Audit Findings and How Leading Banks Address Them
Knowing the frequent audit deficiencies like weak access controls, incomplete incident response plans or undocumented risk registers drawn from SAMA examiner reports.
Audit examiner shares the remediation strategies based on the report that is used by top KSA banks, such as automated monitoring tools, staff training programs and third-party VAPT partnerships for quick fixes.
Also Read : Achieving SAMA CSF Compliance: Step-by-Step Implementation for Fintechs
Strengthening SAMA Compliance with Expert VAPT Services in Saudi Arabia
Expert VAPT services in Saudi Arabia make SAMA audit success easier with finding vulnerabilities at an earlier stage.
It provides documented evidence of fixes and increasing cybersecurity maturity to the needed Level 3+.
These services provide timed reports required by examiners and scan systems simulating real attacks, making compliance become a competitive advantage of financial firms.
VAPT can be used to identify gaps such as insecure access controls or unpatched software, making remediations fast to perform with re-testing as a confirmation and minimizing audit results and aligning with the risk management of SAMA.
By offering strong threat defense, financial institutions can be made operationally resilient, improve customer trust and generate fewer disruptions.
A Realistic Walkthrough: What a SAMA Audit Looks Like in Action
Case Study 1: Banking Sector
The Concern: A mid-sized Saudi bank faced mounting pressure during SAMA CSF audit. They should enhance their cybersecurity measures to safeguard customer information, secure transaction systems and routine implementation of the Maturity Level 3 and keep their operation running.
The Solution: The bank established a cybersecurity governance committee with CISO in charge and implemented technical controls such as multi-factor authentication, privileged access management and automated vulnerability scanning in their banking platforms.
The Result: After 12 months, the bank achieved zero major findings in their SAMA audit, cut security incidents and improved customer trust scores. This success enabled them to launch new digital services under full CSF compliance.
Also Read : How to Automate SAMA CSF Compliance: Tools, Tips & Real‑World Use Cases
Case Study 2: Fintech Startup
The Problem: A rising fintech company in Riyadh had a problem with SAMA audit preparedness caused by lack of documentation, inconsistent access control and limited visibility to see third-party risks throughout their payment system.
The Solution: They did gap analysis between CSF domains, centralized logging using SIEM tools, enforced least-privilege access and outsourced external VAPT testing. Internal mock audits (regularly conducted) improved their risk registers and incident response.
The Result: Fintech was able to pass an initial SAMA audit with a few observations only, obtain more licenses on open banking services, and save on remediation time. Their reported controls facilitated rapid scaling in line with Vision 2030 digital ambitions.
Strengthen Compliance with Wattlecorp’s Expertise
SAMA audit examiners support verifying regulatory compliance with reviewing risk management and controls.
Based on the report findings and recommendations, SAMA audits require Maturity Level 3 controls, risk management and technical defenses. And the examiners assess, cybersecurity maturity and conduct interviews and technical validations.
Audit failure brings fines, license suspension, and reputational harm. By following gap analyses, mock audits, VAPT helps to monitor the track CSF real-time.
Schedule CSF gap assessment and implement VAPT on core systems.
Wattlecorp’s certified auditors deliver gap analysis with VAPT services and remediation roadmaps. These services significantly help to reduce audit findings for KSA banks and fintechs. Contact Wattlecorp for your SAMA compliance advantage.
SAMA Audit FAQs
1. What does a SAMA auditor typically check during an audit?
SAMA Auditors are involved in verifying the accuracy of financial records by conducting detailed examinations of financial institutions to ensure compliance with the rules and structure of SAMA and to assess the effectiveness of risk management and check the adequacy of internal controls. SAMA audit is designed to ensure that these institutions are operating safely, are financially sound and have integrity in their operations in the region.
2. How long does a SAMA audit usually take for financial institutions in Saudi Arabia?
SAMA audits in KSA take a number of months beginning with notification and concluding with the final report. Establish stages of document preparation, fieldwork with testing and interviews and final fixes.
3. What documents are required before a SAMA CSF audit begins?
Submit cybersecurity policies, procedures, asset inventories, logs, risk registers, incident response plans, access control lists, and proof of controls in action. Auditors also need governance charts, third-party risk reports, and maturity self-assessments for CSF domains.
4. What happens if an organisation fails a SAMA audit?
Failure by an organisation to pass a SAMA audit results in a monetary fine, ban and suspension or loss of operating license. In addition to regulatory interventions, a failure may harm the reputation and lose customer faith and therefore a corrective action must be taken, which is compulsory. The frequent failure of compliance might have more serious legal implications.
5. How does VAPT help in improving SAMA audit readiness?
VAPT assists to identify the vulnerabilities and simulates attacks, which lets banks to fix weaknesses before SAMA examiners test controls. It provides documented proof of security testing, directly supporting CSF maturity levels and reducing audit findings. Regular VAPT aligns with SAMA requirements for risk assessment and control validation.