The cybersecurity landscape is evolving. So is cybercrime. Cybersecurity experts warn of new-age attack vectors and APTs (Advanced Persistent Threats), highlighting the need to develop and implement robust defensive strategies. With the threat actors leveraging AI-driven automation and sophisticated invasion tactics, CI/CD pipelines-integrated comprehensive security testing with DevSecOps have emerged as critical pillars to address evolving cybersecurity challenges in 2024-2025.
The UAE is no exception. With cyber threats evolving by the day, launching its National Cybersecurity Strategy 2025–31 makes it highly mandatory to tighten its government’s grip for safeguarding the critical digital assets of its businesses. Protection, innovation, institutional capacity, and partnerships being the major pillars driving UAE’s digital growth, these significantly uphold a secure digital growth under UAE Cabinet guidance.
Application Security Testing (AST) being central to business continuity and growth for the UAE, the one question that remains is how effectively can UAE organizations safeguard their applications from cyber threats. This is where Vulnerability Assessment and Penetration Testing (VAPT) comes into action.
If CI/CD pipeline can smoothly aid in application development and deployment on a continuous plane, integrating VAPT into this process can drastically help your organization take that extra stride in securing your digital assets and sensitive data from the clutches of sophisticated cyber crimes.
Let’s get into the details.
Table of Contents
Toggle- Understanding The Terminological Distinction Between VAPT And AST
- The Application Security Testing Framework
- Why VAPT Integration Into CI/CD Pipelines Is Non-negotiable In The 2025 Threat Landscape
- Technical Implementation of VAPT Tool Integration Into CI/CD Pipelines For UAE Business Applications
- Benefits Of Detecting Vulnerabilities Early In The Development Lifecycle
- Why UAE-based Software Delivery Teams Should Consider Integrating VAPT Within CI/CD Pipelines
- Wattlecorp’s Approach To Incorporating VAPT Within CI/CD Pipelines?
- VAPT in CI/CD pipelines FAQs
Understanding The Terminological Distinction Between VAPT And AST
Vulnerability Assessment and Penetration Testing
VAPT depicts a comprehensive, dual-phase security approach by combining manual exploitation with automated vulnerability discovery.
- Vulnerability Assessment (VA): Systematically identifies and catalogs security weaknesses using automated scanning tools.
- Penetration Testing (PT): Manually exploits identified vulnerabilities to mimic and demonstrate real-world attack scenarios and business impact
A thorough analysis of your systems,network, and applications strengthens cybersecurity posture for your business.
The Application Security Testing Framework
Application Security Testing (AST) when compared to VAPT enlists a broader category of security testing methodologies. These are designed to analyze (security test) applications all through their development lifecycle.
The AST Framework comprises SAST (Static Application Security Testing), DAST (Dynamic Application Security Testing), IAST (Interactive Application Security Testing), and SCA (Software Composition Analysis).
- SAST: Performs source code analysis of an application during its development (SQL injection and buffer overflows)
- DAST: Application is tested in runtime, i.e., in production. (broken authentication and cross-site scripting)
- IAST: Security testing of an application during its execution
- SCA: Involves vulnerability analysis of the third-party component
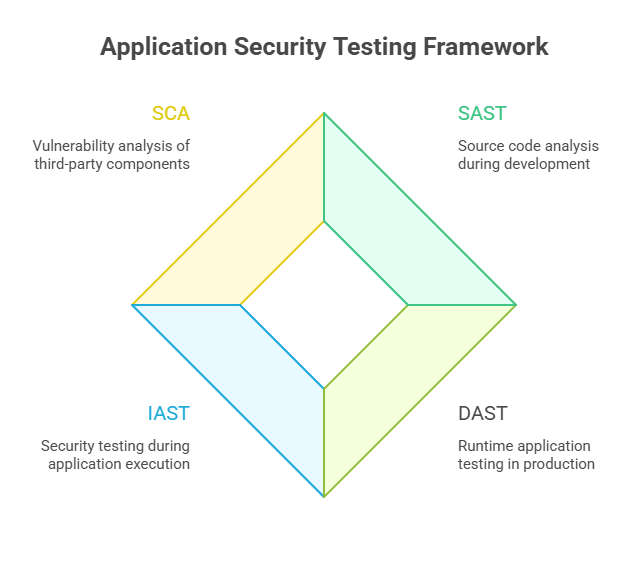
Its ultimate purpose is to render maximum integrity and resilience to software applications throughout their development lifecycle.
Key Distinction Between AST and VAPT
AST mainly relies on automated testing methodologies when testing code and runtime vulnerabilities.
On the other hand, VAPT – when combining automated tools with human involvement, offers a more holistic security assessment by simulating real-world scenarios.
Also Read : The Role of VAPT in Achieving Compliance in UAE
Why VAPT Integration Into CI/CD Pipelines Is Non-negotiable In The 2025 Threat Landscape
Threat Vectors Targeting CI/CD Pipelines In The UAE
With a good number of businesses in the UAE (including startups) relying on cloud-native services, these have gradually made room for cyber crimes to thrive and grow in sophistication. Integrating VAPT into CI/CD pipelines in such scenarios is not only a matter of choice, but a dire necessity – to strengthen the security posture.
By proactively finding and fixing underlying security vulnerabilities, VAPT integration within CI/CD pipelines can help secure business applications right from its development stage. An approach like this will not only help minimize security breach risks, but will also aid in meeting compliance with stringent laws and regulations in the region.
Now let’s look into the common threat vectors targeting CI/CD pipelines
- AI-Powered Supply Chain Attacks: Here, threat actors leverage machine learning to identify and exploit dependency vulnerabilities.
- Pipeline Poisoning: Involves malicious code injections into CI/CD workflows to target the build processes.
- Container Escape Techniques: Utilize advanced container breakout methods to get into the Kubernetes environments.
- Infrastructure as Code (IaC) Vulnerabilities: Misconfigurations in Terraform, CloudFormation, and Ansible templates.
The UAE plans to spread cybersecurity awareness through its Cyber Pulse initiative by introducing training sessions and workshops. Efforts like these will help reinforce the role of VAPT within a broader cybersecurity ecosystem.
Industry-Specific Threat Profiles In The UAE
Banking, Financial Services, Oil and Gas, Insurance (BFSI), Telecommunications, and Government Sectors:
- Open Banking API Vulnerabilities: PSD2 compliance gaps exploitation causing unauthorized financial data access.
- Crypto-mining Infrastructure Attacks: Conducting cryptocurrency mining operations by targeting high-compute environments.
- Regulatory Compliance Bypass: Programming sophisticated attacks by circumventing SOX, PCI-DSS, and Basel III requirements.
Software as a Service (SaaS) Sector:
- Multi-tenant Data Isolation Breaches: Leveraging advanced techniques to access cross-tenant data in shared environments.
- API Rate Limiting Bypass: Utilizing sophisticated methods to overwhelm SaaS platforms through distributed attacks.
- OAuth 2.0 Flow Manipulation: Exploiting authentication vulnerabilities to acquire unauthorized access to customer data.
Technical Implementation of VAPT Tool Integration Into CI/CD Pipelines For UAE Business Applications
GitLab CI Integration
With modern GitLab CI implementations, developers-cum-testers can effectively leverage the platform’s built-in security scanning capabilities while integrating advanced VAPT tools:
Yaml # .gitlab-ci.yml - Advanced VAPT Integration stages:
- build
- sast
- dast
- vapt
- deploy
Variables:
SECURE_ANALYZERS_PREFIX: "registry.gitlab.com/gitlab-org/security-products/analyzers"
VAPT_SCANNER_VERSION: "2025.1"
SAST:
stage: sast
image: $SECURE_ANALYZERS_PREFIX/semgrep:latest
Script: - semgrep --config=auto --json --output=sast-results.json .
artifacts:
reports:
sast: sast-results.json
expire_in: 1 week
DAST:
stage: dast
image: $SECURE_ANALYZERS_PREFIX/dast:latest
Script: - dast -t $CI_ENVIRONMENT_URL -f json -o dast-results.json
artifacts:
reports:
dast: dast-results.json
expire_in: 1 week
VAPT Assessment:
inputs:
pathtoPublish: 'vapt-results'
artifactName: 'security-reports'
publishLocation: 'Container'
- stage: SecurityGate
displayName: 'Security Gate'
dependsOn: SecurityAnalysis
jobs:
- job: SecurityApproval
displayName: 'Security Team Approval'
steps:
- task: PowerShell@2
displayName: 'Security Gate Logic'
inputs:
targetType: 'inline'
script: |
# Parse VAPT results
$vaptResults = Get-Content -Path "vapt-results/vapt-report.json" | ConvertFrom-Json
$criticalCount = ($vaptResults.findings | Where-Object { $_.severity -eq "critical" }).Count
$highCount = ($vaptResults.findings | Where-Object { $_.severity -eq "high" }).Count
Write-Host "Critical vulnerabilities: $criticalCount"
Write-Host "High vulnerabilities: $highCount"
if ($criticalCount -gt 0) {
Write-Host "##vso[task.logissue type=error]Critical vulnerabilities found. Deployment blocked."
exit 1
}
if ($highCount -gt 5) {
Write-Host "##vso[task.logissue type=warning]High vulnerability count exceeds threshold. Manual approval required."
# Trigger manual approval process
exit 1
}
Write-Host "Security gate passed. Proceeding with deployment."
Industry-Specific Implementation Strategies
BFSI Sector: Regulatory Compliance Integration
Financial institutions require specialized VAPT implementations that address regulatory requirements:
PCI-DSS Compliance Integration:
yaml
# PCI-DSS focused VAPT configuration
vapt_pci_compliance:
stage: compliance_testing
image: wattlecorp/vapt-pci:2025.1
script:
- vapt-scanner --target $CI_ENVIRONMENT_URL
--compliance-framework PCI-DSS-v4.0
--cardholder-data-flow-analysis
--network-segmentation-test
--encryption-validation
--access-control-verification
--logging-audit-trail-check
--vulnerability-scan-quarterly
--penetration-test-annual
artifacts:
reports:
compliance: pci-dss-report.json
expire_in: 12 months
only:
- production
- pre-production
SaaS Sector: Multi-Tenant Security Testing
SaaS platforms require specialized testing approaches for multi-tenant environments:
Multi-Tenant Isolation Testing:
yaml
# Multi-tenant security validation
saas_security_testing:
stage: vapt
image: wattlecorp/vapt-saas:2025.1
script:
- vapt-scanner --target $CI_ENVIRONMENT_URL
--test-profile saas-multi-tenant
--tenant-isolation-test
--api-rate-limiting-bypass
--oauth-flow-manipulation
--data-leakage-detection
--privilege-escalation-test
--subdomain-takeover-scan
parallel:
matrix:
- TENANT: ["tenant1", "tenant2", "tenant3"]
API_VERSION: ["v1", "v2"]
artifacts:
reports:
security: saas-security-report-${TENANT}-${API_VERSION}.json
Advanced VAPT Tool Integration Patterns
Container Security Integration
Modern applications require container-specific security testing:
yaml
# Container security pipeline
container_security:
stage: security
image: docker:latest
services:
- docker:dind
script:
# Build secure container
- docker build -t app:$CI_COMMIT_SHA .
# Container vulnerability scan
- docker run --rm -v /var/run/docker.sock:/var/run/docker.sock
-v $(pwd):/workspace
wattlecorp/container-scanner:2025.1
--image app:$CI_COMMIT_SHA
--output /workspace/container-scan.json
--format json
--severity-threshold high
--include-secrets-scan
--include-malware-scan
--include-compliance-check
# Runtime security testing
- docker run -d --name app-runtime -p 8080:8080 app:$CI_COMMIT_SHA
- sleep 30
- docker run --rm --network container:app-runtime
wattlecorp/runtime-scanner:2025.1
--target localhost:8080
--runtime-analysis
--process-monitoring
--network-traffic-analysis
--file-integrity-monitoring
API Security Testing Integration
API-first applications require specialized testing approaches:
yaml
# API security testing
api_security:
stage: api_testing
image: wattlecorp/api-security-scanner:2025.1
script:
- api-security-scanner
--openapi-spec ./api/openapi.yaml
--base-url $CI_ENVIRONMENT_URL
--authentication-config ./api/auth-config.yaml
--test-cases ./api/security-test-cases.yaml
--output-format json,html
--output-file api-security-report
--include-owasp-api-top10
--include-business-logic-flaws
--include-rate-limiting-bypass
--include-injection-attacks
--include-authentication-bypass
--include-authorization-flaws
--parallel-requests 50
--max-test-duration 3600
artifacts:
reports:
api_security: api-security-report.json
paths:
- api-security-report.html
Performance Optimization for CI/CD Integration
Parallel Execution Strategies
Modern DevOps trends emphasize AI automation and GitOps support, requiring optimized parallel execution:
yaml
# Optimized parallel VAPT execution
parallel_vapt:
stage: security
parallel:
matrix:
- SCAN_TYPE: ["sast", "dast", "iast"]
SEVERITY: ["critical", "high", "medium"]
script:
- case $SCAN_TYPE in
"sast") execute_sast_scan --severity $SEVERITY ;;
"dast") execute_dast_scan --severity $SEVERITY ;;
"iast") execute_iast_scan --severity $SEVERITY ;;
esac
artifacts:
reports:
security: ${SCAN_TYPE}-${SEVERITY}-results.json
Caching and Optimization
yaml
# Intelligent caching for VAPT tools
cache:
key:
files:
- package-lock.json
- requirements.txt
- go.sum
paths:
- vapt-cache/
- vulnerability-database/
- security-rules/
before_script:
- |
if [ ! -d "vapt-cache" ]; then
mkdir -p vapt-cache
wget -O vapt-cache/vulnerability-db.zip
https://updates.wattlecorp.com/vuln-db/latest.zip
unzip vapt-cache/vulnerability-db.zip -d vulnerability-database/
fi
Benefits Of Detecting Vulnerabilities Early In The Development Lifecycle
Imagine if you could detect and fix a problem before it turns into a threat! Finding vulnerabilities early into an application’s development lifecycle is not just about boosting your security posture. In fact, it saves you from facing costly breaches – the kind that makes headlines!
You save time, money, and effort – allowing you to run your business more smoothly and efficiently.
Here are a list of other benefits you obtain when integrating VAPT into your application testing process:
- Risk Reduction: Reduces risks of exploitation from malicious actors upon prompt identification, assessment, and mitigation early into the development lifecycle.
- Proactive Security: Detecting and negating security threats early into the development cycle offers a proactive approach to managing security than reacting to security incidents when they happen.
- Improved Trust: Continuous demonstration of commitment to security helps organisations build enhanced trust with their customers.
Businesses categorized under mandatory cyber incident reporting should mandatorily report security incidents under UAE Federal Decree‑Law No. 34 (2021). Measures like this underpin the need to catch issues early as strong legal incentives.
Also Read : 5 Signs Your Business Needs VAPT Immediately
Why UAE-based Software Delivery Teams Should Consider Integrating VAPT Within CI/CD Pipelines
If you’re a UAE-based software delivery team, VAPT integration in CI/CD workflow, will help you:
- Improve collaboration: By providing automated feedback loops and shared repository – enabling developers to work more effectively and efficiently.
- Streamlined workflow: By automating tasks and reducing manual intervention, CI/CD pipelines help streamline the SDLC process.
- Faster feedback loops: Developers can gain rapid feedback through automated tests and deployments. This allows for rapid identification and fixation of issues – also improving software reliability and code quality.
- Improved Reliability: CI/CD helps ensure software reliability and availability by automating the deployment process and simultaneously providing mechanisms for rollback and recovery.
- Reduced Deployment Time with Faster Time To Market: Significantly reduces the time taken to deploy new versions of software.by automating the deployment process. Developers like you can respond quickly to changing user needs through this.
- Enhanced Software Quality: Helps ensure high-quality software by reducing bug risks and improving overall user experience through continuous testing and feedback loops.
Wattlecorp’s Approach To Incorporating VAPT Within CI/CD Pipelines?
As an experienced cybersecurity service provider, we’ve been able to successfully tackle the most complex security issues for our clients’ businesses. And when it comes to successfully integrating VAPT to secure your business operations, our VAPT experts can do it to perfection.
Considering the aforementioned challenges of incorporating VAPT in CI/CD pipelines, our experts have the following troubleshooting approaches for you:
- Shift-Left Security: Denotes incorporating security practices early into the SDLC for promptly identifying and fixing known vulnerabilities. This approach effectively helps reduce costly breaches.
- Automating Static and Dynamic Scans Within the Pipeline: By utilizing the DevSecOps model combined with automation tools, such as Kubernetes and Docker, our team incorporates static and dynamic scans.
- Regular updates and patching to tackle newly discovered vulnerabilities: Through Software Composition Analysis (SCA), we can help you identify open and third-party libraries in an application. Detecting and addressing newer vulnerabilities through updates and patches becomes possible via this approach.
- Collaboration between developers, security experts, and operations teams: By utilising DevOps and DevSecOps (CI/CD) models, we ensure collaboration and communication among the development, security, and IT teams. You can thereby improve your operational efficiency by nurturing a vulnerability-response work culture.
- Continuous monitoring and feedback loops for improvement: Here also, we implement our DevOps and DevSecOps models, where we can conveniently automate scanning and quickly deploy updates through an efficient feedback loop. This results in an efficient connection among the operations, development, and security teams.
VAPT integration in CI/CD workflow makes way for proactively securing your application against potential cyber threats early in the software development lifecycle.
UAE’s efforts to enhance its cybersecurity efforts by adopting DevSecOps and VAPT-embedded CI/CD comes in the light of its want to curb cyber terrorism to a significant extent. A move like this has prompted it to invest a massive amount of AED 7.35 billion. An amount like this is enough to depict how seriously this nation is in enforcing a high-profile cybersecurity measure to secure its digital transformation.
CI/CD pipelines enhanced by DevSecOps could turn out to be a major stride in this effort, where VAPT integration will drastically help ensure security from the start rather than an afterthought. The key is to make security assessment a part and parcel of the software development lifecycle.
Want to effectively integrate VAPT into your CI/CD pipeline, but do not know whom to turn to for assistance? Our DevSecOps team at Wattlecorp at UAE will provide you with all assistance and consultation you need to secure your application in the best possible manner.
Safeguard your applications with Wattlecorp and steer clear of vulnerabilities that kill!.
Book a Vulnerability Scan!
VAPT in CI/CD pipelines FAQs
1.What are the performance implications of integrating comprehensive VAPT into every CI/CD pipeline execution?
Performance optimization for effective VAPT integration requires a strong strategic scan distribution, intelligent caching, and risk-based execution policies.
Optimization Strategies:
• Intelligent Scheduling: Leverage off-peak hours for comprehensive scans using delayed execution
• Microservice-Specific Testing: Target only modified services in microservice architectures
• Parallel Execution: Distribute scans across multiple agents with result aggregation
Performance Metrics (Based on 2025 implementations):
• Full VAPT scan: 15-45 minutes (depending on application complexity).
• Incremental scan: 3-8 minutes.
• Parallel execution efficiency: 60-80% time reduction
• Cache hit rate: 40-60% for dependency scans
2.What are the challenges in integrating VAPT in CI/CD Pipelines?
Integrating VAPT into CI/CD pipelines for application security testing can be challenged by:
Slowing down processes, increasing build and deployment times.
Difficulty in integrating automated tools due to differing configuration management practices.
False positives in automated tests demanding proper knowledge of the application, including language and framework.
Developer Resistance due to emphasis on functionality over security.
The rise in AI-driven phishing threats coupled with the UAE’s infostealer malware spike (RedLine) stresses the importance of handling false-positive findings to ensure resilient pipelines.
3.How do we handle false positives in automated VAPT scans within CI/CD pipelines?
False positive management in CI/CD-integrated VAPT requires a multi-layered approach that combines automated filtering, machine learning-based validation, and human expertise integration.
Technical Implementation:
yaml
# Advanced false positive management
false_positive_management:
stage: validation
script:
- python3 /scripts/ml-false-positive-filter.py
--input vapt-raw-results.json
--model /models/fp-detection-model-v2025.1.pkl
--confidence-threshold 0.85
--output vapt-filtered-results.json
- python3 /scripts/historical-analysis.py
--current-results vapt-filtered-results.json
--historical-data /data/historical-scans/
--similarity-threshold 0.90
--output vapt-validated-results.json
Best Practices:
- Prepare and maintain a curated whitelist of known false positives, considering business justifications.
- Implement confidence scoring for automated findings.
- Use historical trend analysis to identify recurring false positives.
- Establish expert review workflows for edge cases.