Have you realized how important it is to ensure API Penetration Testing (Application Programming Interfaces) security? Being the backbone of modern applications and data exchange, it is essential that you ensure API security in totality – yes, from inducing strict authentication to encrypting data in both their static and dynamic state. These statements would definitely mean a lot if your businesses rely on APIs, wouldn’t they? Now imagine what will happen if you leave your API endpoints astray? Without proper security measures to protect them? The result can be anything from data breaches to financial loss and legal penalties. It goes without saying that these do not need to be explained here all at once.
Remember the Uber API data breach incident? In 2016, Uber was hit by a data breach in which the hacker got to illegally access the personal information of many of its drivers and riders (estimate 57 million). While incidents like Uber are endless, what these convey to us is that it’s high time we start securing our APIs – down to the core. This is critical as far as safeguarding your sensitive customer information and your business matters to you. Stressing further, API security assessment is vital to an organization’s well-being – whether you own them or rely on external APIs for meeting your business objectives.
So, what does it take to ensure API security?
Wattlecorp’s expert cybersecurity professionals suggest Penetration Testing for APIs as the latest and best modality to detect, assess, and mitigate API vulnerabilities.
Here, we will explore how and why penetration testing is helpful in securing APIs.
Key points to discuss include:
- API Security Risks
- Role of Penetration Testing in
- API Security
- Best Practices For Effectively Conducting API Penetration Testing
- Securing API Development.
Table of Contents
ToggleAPI Security Risks – Understanding The Sensitive Nature Of API Security
Most businesses do not take API security seriously. Understanding its essence will help you realise the sensitiveness of securing your API.
1. Identifying Common API Vulnerabilities
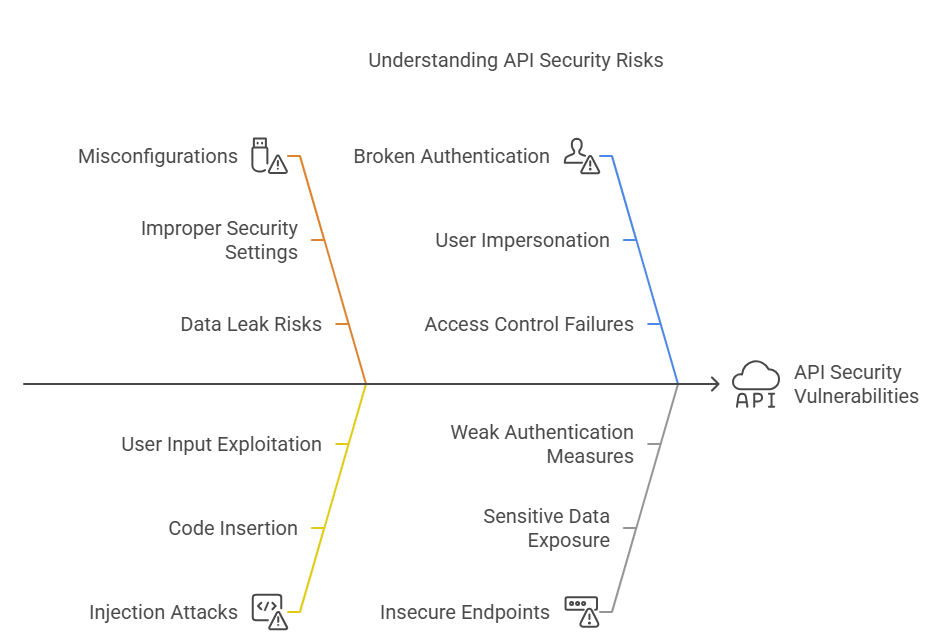
Ensuring API security is critical to safeguarding the confidentiality and integrity of business data. However, the process of securing APIs is easier said than done. For your information, API security risks comprise the following:
- Misconfigurations: If security features of an API are not configured properly, it risks the chances for unauthorised access and data leaks.
- Injection Attacks: Happens when malicious hackers insert/inject harmful codes into an API request. This results in vulnerability exploitation on how API processes user input.
- Broken Authentication: A security vulnerability that allows attackers to impersonate users when the latter tries to access a website or application.
- Data Breaches: Happens when attackers derive access to sensitive data.
- DoS Attacks: Attackers disrupt services by sending too many API requests.
- Insecure Endpoints: These can significantly expose sensitive data to data breaches.
- Unauthorised Access: Results due to weak authentication measures.
Hopefully, the types of API risks mentioned and explained above will guide you on how to safely secure your API. What you can expect is a strengthened security posture for your API in all efficacy and efficiency.
2. Real-World Cases Of API Security Incidents
Modern businesses are heavily reliant on APIs for their multiple requirements. From streamlining their operations and improving their scalability to improving their efficiency, the list goes on. Amid these chaos, they naturally tend to leave out the most vital thing – API security. If they can manage API security in every effectiveness, they can remarkably avoid any impending risks of cyber threats and incidents. The case studies illustrated below will help you understand how critical it is to safeguard and ensure API security for your business.
3.Capital One
The Capital One API Security Incident is another instance of API data breach that led to the exploitation of sensitive customer data way back in 2019. This incident represents one of the largest data breaches that impacted data privacy and safety. It was triggered because an AWS (Amazon Web Service) employee exploited vulnerability within the Capital One infrastructure. With over 100 million customer records affected, the Capital One API Breach provided a critical lesson on the importance of securing cloud environments.
4. Equifax
If there was any massive data breach that occurred to a company, it would be Equifax. The reason, API vulnerabilities again – leaving enough room for unauthorised access and control/manipulation of sensitive information. It was evident that the authentication measures that Equifax adopted weren’t enough to avoid such a crisis.

5.Facebook-Cambridge Data Leak
Another real-life example for not appropriately ingesting proper authorisation and access controls – resulting in a large amount of user data being leaked. The New York Times had reported that Cambridge Analytica’s employees and contractors sold psychological profiles of Facebook users to political campaigns. It was a clear incident of data leak, which left accessibility to a significant number of user data on Facebook. The Facebook-Cambridge Leak could be considered to be a massive security incident in history.
6.The Marriott Data Breach
Weaknesses within the API of Marriott Hotel resulted in a number of hotel guests losing their personal information. The Marriott Data Breach represented a good example for Broken Authentication, which allowed the hackers to steal sensitive data of this grand hotel’s guests. Lessons learnt from these incidents is to induce strong API security measures. The upcoming section explains why penetration testing is vital to ensuring and achieving robust API security. So, let’s get there.
What is API Penetration Testing?
API penetration testing is recognised as one of the most advanced and reliable methods for securing API infrastructure.. Penetration testing for API predominantly involves identifying vulnerabilities by simulating malicious attacks on the API endpoints of an application. Identifying and mitigating potential vulnerabilities within an application’s API to prevent impending cyber attacks by ensuring robust authentication is the primary objective of API penetration testing.
You need to note that API penetration testing differs from traditional penetration testing. Traditional pen testing strives to examine system vulnerabilities in a broader sense (across networks or applications). Whereas, API pen testing is keen on identifying security weaknesses within the API of an application.
You will also benefit from knowing and understanding how OWASP API Security Top 10 helps with API penetration testing. Functioning as a standardised framework for API penetration testing, the OWASP API Security Top 10 helps provide a prioritised list of API vulnerabilities. Our penetration testers from Wattlecorp are highly proficient in working on the security flaws based on the level of risk, severity, and impact these hold. The OWASP API Security Top 10 helps ensure a comprehensive coverage of potential attack vendors. These are then prioritised based on the severity of their risks and mitigated accordingly.
Performing API Penetration Testing: Methods Explained
For conducting penetration testing for API, you should have a clear objective in place. Because, as a business, your need to pen test API may differ from those of others. Say, for instance, you would need to meet compliance requirements, such as GDPR, SOC 2, or HIPPA. At other times, you may need to perform vendor assessments for third-party security assurance. Whatever be the reason, there are specific methods to pen test API.
Let’s find out what these include.
A. API Enumeration & Mapping
What It is: API Enumeration and Mapping is all about understanding endpoints, parameters, and request methods to an API. For your information, endpoints are nothing other than the URLs that exist in the API environment.
What It Does: API Enumeration primarily aids in discovering and listing all available endpoints. Whereas, API Mapping helps create a visual representation of how different endpoints connect with each other and the functionalities they offer.
Why It’s Important: API Enumeration and Mapping in terms of API Penetration Testing are helpful in:
- Identifying shadow APIs: Helps reveal APIs, which aren’t officially documented.
- Understanding API Functionality: Assists the developers and testers in understanding the structure and functionality of the APIs.
- Monitoring Changes: Helps track changes and ensure that endpoints are thoroughly and appropriately secured by regularly mapping APIs.
- Conducting Security Testing: Once the security testers have understood all the available endpoints, they can effectively identify potential vulnerabilities and resolve them. Common vulnerabilities include misconfigurations and unprotected endpoints.
Also Read : Internal vs External Penetration Testing: Which is Right for Your Business?
B. Authentication & Authorisation Testing
What It Is: Helps authenticate users/applications for what the latter claim to be. Also assists in determining that users are authorised to access specific resources.
What It Does: API Authentication and Authorisation Testing verifies users or applications of their identity. This process helps authorise the users/applications to the actions or resources they are allowed to access.
Why It’s Important: Authentication and Authorisation Testing in API helps with:
- Verifying Broken Authentication and Privilege Escalation: Implements strong authentication and authorisation for all API endpoints to protect them from security vulnerabilities, such as broken authentication and privilege escalation.
- Edge Case Testing: Scenario testing for expired or invalid tokens, including users presenting with ambiguous permissions.
- Security Testing: Helps identify vulnerabilities in the authentication and authorisation mechanisms.
- Positive Testing: Tests to verify that only authenticated users with correct permissions can access resources.
- Negative Testing: Unauthorised users with insufficient permissions are denied resource access.
C. Input Validation & Injection Testing
What It Is: A combination of Input Validation and Injection Testing in API helps ensure data integrity by simulating real-world attacks.
What It Does: Injection testing mimics real-world API injection attacks by manipulating inputs to detect unintended actions. Input validation serves as a counter measure by testing the format, type, and length of user inputs to validate whether these conform to the accepted format.
Why It’s Important: Input validation and Injection Testing are among the critical API penetration testing methods because these help identify and prevent security vulnerabilities.
Common injection attacks include SQL Injection, Cross-Site Scripting, and XML External Entities (XXE).
Also Read : Internal Penetration Testing: Why It’s Essential for Organizational Security
D. Rate Limiting & Denial-of-Service Testing
What It Is: Rate Limiting and Denial-of-Service Testing is another of those combination methods in API penetration testing.
What It Does: Both Rate-Limiting and Denial-of-Service Testing restrict the number of user requests within a specific timeframe.
Why It’s Important: Both Rate Limiting and Denial-of-Service Testing help secure API endpoints by preventing potential security flaws and threats. These include resource overload and DoS Attacks.
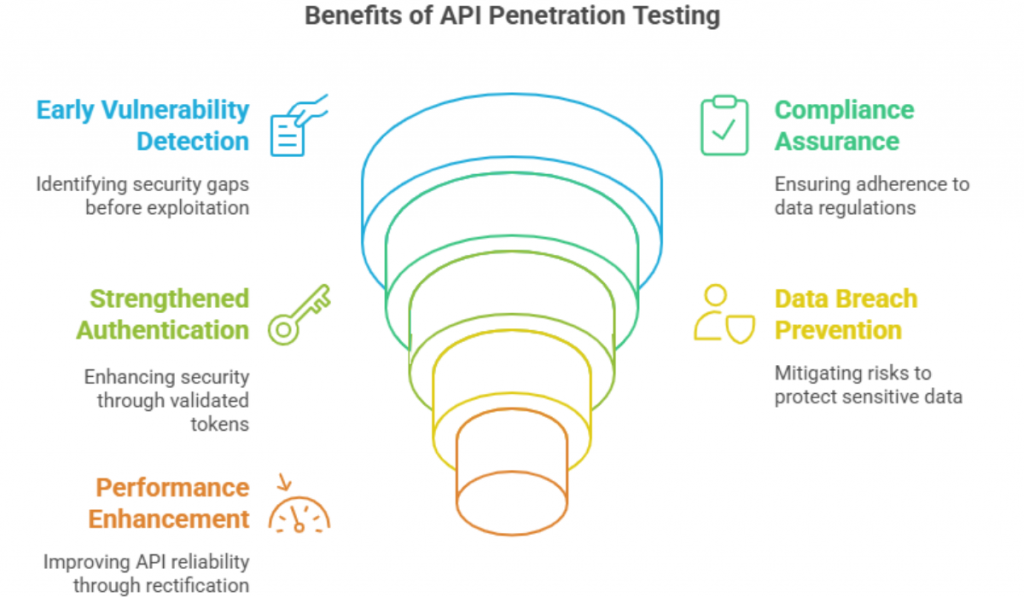
Key Benefits of API Penetration Testing
When you start adopting the best practices to conduct API penetration testing, you automatically get to enjoy benefits linked with this process. Without ado, let’s get to know what these include, especially when conducting regular API pen testing.
- Early Detection of Vulnerabilities: Helps identify and close security gaps before hackers exploit.
- Compliance with Security Standards: Guarantees adherence to data regulations, such as GDPR, HIPAA, PCI-DSS, ISO 27001 requirements.
- Strengthening API Authentication & Authorisation: By validating token-based authentication, API pentesting helps strengthen its authentication and authorisation
- Preventing Data Breaches & Financial Loss: One of the main objectives of API pen testing is to prevent data breaches and financial loss through risk mitigation and protecting sensitive data from getting exposed.
- Enhancing API Performance & Reliability: In identifying and rectifying misconfigurations, API pen testing helps improve performance and reliability.
Penetration testing for API is crucial given the surge in API traffic and increased reliance on applications. With APIs loaded with multiple requests, this increases the risks of cyber threats and attacks, specifically due to underlying vulnerabilities. Penetration testing idealises understanding and mimicking real-world hacker techniques. It is a sure-shot cyberdefense strategy that effectively helps prevent potential cyberattacks – thereby, strengthening API security. It would also be a good idea if you consider integrating DevSecOps as a prudential security measure to protect your APIs and everything in its vicinity.
How Wattlecorp Can Help Enhance Your API Security
Are you serious about your API safety and want to protect it in all its worth? And are you in search of a reliable API penetration testing service provider? Wattlecorp Cybersecurity Labs is the right one for you. Armed with a team of certified VAPT professionals and cybersecurity experts, we are here to solve any pertinent security issues you may be facing, including enhancing your API security.
In the years of offering cybersecurity service to our clients and the trust and confidence they bestowed on us is an achievement we highly honor. Our high-profile clients include the Fortune 500 companies, such as Bentley, Mercedes Benz, and Walmart to name a few. Schedule a call or drop your concerns in the form provided and we will get back to you to solve all your API security-related concerns. Schedule an API Security Assessment today and maximise API security for your business.
Penetration Testing FAQs
1.How does penetration testing help identify API vulnerabilities?
Penetration testing for API first and foremost involves simulating real-world attacks, analysing or studying API responses, and utilising automated tools to find security weaknesses. This also includes prioritising and mitigating risks based on their severity and impact.
Note that you need to be expert enough to conduct API penetration testing, else hire expert service.
2.What are the common API security risks that penetration testing can detect?
The common API security risks that penetration testing can help detect include:
-Misconfigurations.
-Unauthorised access
-Broken authentication
-Inadequate rate-limiting
-SQL Injections
3.What are the best practices for integrating penetration testing into API development?
The best practices to incorporate penetration testing into API development involve:
-Enforcing MFA
-Encrypting data – during rest and transmission.
-Running the OWASP API Security Top 10 for vulnerability prioritisation.
-Input Validation and Injection Testing.
-API Documentation
-API Security Checklist.