Key Takeaways:
- The NCA cloud security controls focus more on shared responsibility, secured provider infrastructure and at the same time customers should secure their data, applications and access to users.
- NCA requires secure configuration baselines on IaaS, PaaS and SaaS; organizations are expected to implement effective configurations such as encryption and turnoff of idle ports.
- Multi-factor authentication (MFA) and privileged access management (PAM) are required to control the identity aspects to prevent unauthorized access as it becomes required in NCA guidelines.
- Real-time threat detection and safe logging can assist Saudi organizations to identify and track threats in real-time and have a robust audit trail to ensure NCA compliance.
- Vulnerability Assessment and Penetration Testing (VAPT) is essential to seal security gaps and keep NCA up to date and avoid cyberattacks in the future.
Table of Contents
Toggle- How NCA Cloud Security Controls Protect IaaS, PaaS, and SaaS Environments in Saudi Arabia
- Understanding SaaS, PaaS, and IaaS Under NCA
- Defining Security Accountability in the NCA Shared Responsibility Model
- Ensuring Compliance with NCA’s Cloud Configuration Baseline Standards
- Establishing Strong Identity, Access and Data Protection Controls
- Implementing Continuous Monitoring and Logging Requirements
- VAPT’s Essential Role in Achieving and Maintaining NCA Cloud Compliance
- Navigating Compliance Gaps in Saudi Cloud Environments: A Strategic Approach
- NCA Cloud Security Controls FAQs
How NCA Cloud Security Controls Protect IaaS, PaaS, and SaaS Environments in Saudi Arabia
What is NCA Cloud Security Control and how do they apply to IaaS, PaaS, and SaaS environments in Saudi Arabia?
The Cloud Cybersecurity Controls (CCC) function as a critical extension of the Essential Cybersecurity Control, which is developed by the National Cybersecurity Authority (NCA) to address cloud-specific security.
These rules were made to identify and resolve the specific dangers of cloud computing in Saudi Arabia, such as unwanted data access, lack of clear visibility and the risks of using third-party hosting.
The NCA cloud security controls provide a clear map for both Cloud Service Providers (CSPs) and the businesses that use them (CSTs).
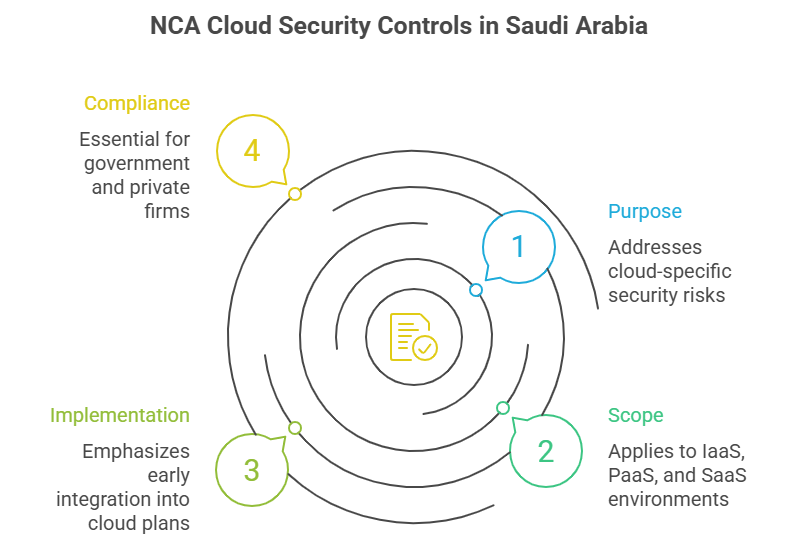
It highlights that security shouldn’t be a late addition and organizations must bake these controls into their cloud plans from day one, ensuring every virtual tool or cloud app is built on a foundation of safety.
Whether you are a government body or a private firm in Saudi Arabia, it is essential to know how to apply these rules across software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (IaaS) is the secret to staying compliant and keeping your operations running smoothly.
Understanding SaaS, PaaS, and IaaS Under NCA
To put NCA cloud security controls into practice, you need to understand what you are in charge of. The cloud service is split into three main models, each needing a different look at cloud security configuration.
- Software as a Service (SaaS): SaaS delivers fully managed applications over the internet. Under NCA, the cloud provider manages the application and infrastructure, while organizations remain responsible for user access, data usage, compliance, and vendor risk management.

- Platform as a Service (PaaS): PaaS delivers a ready-to-use platform for application development and deployment. Under NCA, the provider secures the infrastructure and platform components, while organizations are responsible for application security, data protection, identity management, and compliance controls.
- Infrastructure as a Service (IaaS): IaaS provides virtualized computing resources such as servers, storage, and networking. Under NCA, organizations are responsible for securing operating systems, applications, data, access controls, and monitoring, while the cloud provider secures the underlying infrastructure.
Defining Security Accountability in the NCA Shared Responsibility Model
To achieve full compliance in Saudi Arabia, organizations must recognize that the NCA cloud security controls operate on a shared responsibility basis, where your specific safety obligations shift depending on the service model you deploy.
A common pitfall for businesses in Saudi Arabia is the set it and forget it mindset, thinking the provider does all the security work. The NCA framework is very clear about the shared responsibility model.
Also Read :- A 2025 Guide To Understanding the Essential Cybersecurity Controls (ECC) of NCA in Saudi Arabia
Under the NCA cloud security controls, the provider takes care of the security of the cloud such as the physical buildings, cooling, and hardware.
However, the customer is in charge of the security in the cloud. This includes cloud security compliance for your files, user accounts, and the specific settings you pick.
If a database is left open without a password, the blame lies with the customer, not the provider.
Ensuring Compliance with NCA’s Cloud Configuration Baseline Standards
A configuration baseline is a set of safety settings that must be applied to every cloud asset. For NCA cloud security, these baselines act as a wall against common hackers.
For IaaS cloud security service setups, this means closing unused digital ports, using encrypted storage, and making sure no resource is open to the public internet unless it has to be.
For saas security, it involves checking outside apps that connect to your system and making sure data sharing is only for people who need it.
Keeping these baselines steady ensures your cloud security controls stay strong across your whole company.
Establishing Strong Identity, Access and Data Protection Controls
In the current digital landscape of Saudi Arabia, the perimeter is no longer a physical wall; it is the identity of your users and the integrity of your data.
The NCA cloud security controls shift the focus from protecting pipes to protecting people and assets. Implementing these controls isn’t just a technical task, it is a strategic necessity to maintain the trust of stakeholders across Saudi Arabia.
Under the NCA cloud security controls, organizations must move beyond simple passwords. In Saudi Arabia, compromised credentials are a leading cause of breaches. By adopting a Zero Trust mindset, you ensure that every entry point is rigorously defended.

- Multi-Factor Authentication (MFA): This is a non-negotiable requirement of the NCA cloud security controls. By requiring a second form of verification, businesses in Saudi Arabia can block unauthorized access even if a password is stolen.
- Privileged Access Management (PAM): Not all users are equal. The NCA cloud security controls mandate strict oversight for power users (administrators). In Saudi Arabia, logging and monitoring every action taken by these accounts is vital for preventing high-level system abuse.
- Encryption: This human-centric approach ensures that employees in Saudi Arabia only have the access they absolutely need. Whether you are checking PaaS or IaaS, encryption keys must be handled safely based on NCA rules.
Implementing Continuous Monitoring and Logging Requirements
Cloud environments are evolving quickly and new resources are being added or removed in a matter of seconds.
To remain in line with required NCA cloud security, there should be continuous monitoring of such changes.
Organizations in Saudi Arabia should document all administrative operations, failed login attempts and cases of access to data.
Also Read :- NCA Compliance and Cybersecurity Excellence: How Saudi Banks Can Achieve Regulatory Success
Such logs are used to rebuild the incidents in the event of a security breach and are also important evidence when NCA audits the cloud compliance.
The absence of a central logging system makes it very challenging to detect a professional attacker within the cloud network. Moreover ensure to keep all essential logging requirements to strengthen our security posture.
VAPT’s Essential Role in Achieving and Maintaining NCA Cloud Compliance
Setting up your cloud based on the rules is a good start but making sure it actually keeps people out is what matters. This is why VAPT services in Saudi Arabia are a must-have for checking NCA compliance.
A Vulnerability Assessment and Penetration Test (VAPT) acts like a drill for your cloud setup.
It can highlight if a safe SaaS security baseline requirements setting can be stepped over or if an IaaS server has a weak spot.
By investing into VAPT services in Saudi, companies can find and fix gaps before an auditor shows up or a hacker finds a way in. It turns compliance from a simple checklist into real-world protection.
Navigating Compliance Gaps in Saudi Cloud Environments: A Strategic Approach
Reaching NCA cloud security compliance is an ongoing task, not a one-off job. As threats in Saudi Arabia change, your NCA cloud security controls need to be checked and tested often.
By focusing on strict setup rules for IaaS, PaaS, SaaS and keeping a tight grip on who can access your data, you protect your business and the Kingdom’s digital future.
Wattlecorp helps organizations to handle these complex regulations through expert guidance by setting reviews and focused VAPT services in Saudi Arabia.
Ready to lock down your cloud? Talk to Wattlecorp for your NCA Cloud Security Check and Setting Review today.
NCA Cloud Security Controls FAQs
1. What are NCA Cloud Security Controls in Saudi Arabia?
NCA Cloud Security Controls are guidelines set by the National Cybersecurity Authority (NCA) to ensure cloud security in Saudi Arabia, which addresses issues like data access, third-party risks and cloud-specific threats. Wattlecorp helps you understand and use these NCA cloud security controls so your business stays on the right side of the law.
2. How do NCA controls differ for SaaS, PaaS, and IaaS?
The major difference between SaaS, PaaS, and IaaS is who does the work. For IaaS security, you handle more of the technical side, while for SaaS, you need to focus more on user permissions. With PaaS, the provider takes care of the platform security, but you are responsible for securing your applications and data.
3. Who is responsible for cloud security under NCA guidelines?
Both the provider and the user have a role in the responsibility for cloud security under NCA guidelines. The user is always the one responsible for protecting their own files and managing who gets in. Make sure your team knows their exact job in this NCA cloud security setup.
4. Are NCA Cloud Security Controls mandatory for private organizations?
Yes, NCA cloud security controls are mandatory for private organizations that work with the government or handle sensitive data in Saudi Arabia. Many private firms also voluntarily follow these controls to demonstrate their commitment to security and compliance.
5. How does VAPT support NCA cloud compliance?
VAPT gives you proof that your security settings actually work. It is often a needed step to show auditors that you are following the rules. Wattlecorp’s VAPT services Saudi assists to find the hidden holes that could cause you to fail an audit.