Stay here if you’re an SOC and need to effectuate your SOC Strategy. Partnering with SOC (Security Operations Centre) is the best option you can avail.
A well-structured SOC underpins everything from monitoring threats to staying ahead with swift incident detection and responses. You can also effectively initiate proactive risk management, and build and maintain an efficient SOC threat-response strategy. Note that the effectiveness of a SOC lies in providing a centralised platform to manage security operations. The real challenge, however, is to develop an SOC strategy that aligns with your business goals.
This blog will offer you insights into what it takes to build a resilient SOC. It will also consider planning a definitive strategy by utilising modern technologies to optimise SOC functionality.
Let this blog kickstart your journey to avail maximum security for your business. Also, have your vital assets protected against the unexpected by implementing SOC strategy and adopting appropriate SOC optimisation techniques.
Table of Contents
ToggleUnderstanding SOC Strategy
SOC (Security Operations Center) strategy refers to adopting a comprehensive approach to actively monitor, detect, analyse, and respond to cybersecurity threats.
The prime objective is to achieve effectiveness in rapid detection and response to security incidents with simultaneous mitigation of threats in real time.
SOC Strategy, therefore, serves as a guiding framework to build a cohesive system that integrates people, processes, and technology.
If you start implementing SOC strategy for your business, what you achieve is an effective alignment of your security objectives with your business goals.

Sounds good, isn’t it? If you ask how, this is possible by a SOC offering a clear direction for threat response, risk management, and continuous improvement of security measures.
What’s more important to note here is that by standardising its approach to help achieve reduced threat response times, SOC Strategy implementation helps enhance overall performance for your business.
The key to an effective SOC strategy implementation is using a well-documented SOC strategy framework.
The ultimate result is improved resilience to emerging cyber threats.
Tips To An Effective SOC Strategy Development And Implementation
Building an effective Security Operations Center (SOC) strategy is important to protect an organisation from all sorts of cyber threats.
For you to develop an effective SOC strategy, the following points should be considered:
1. Defining Measurable Goals
An effective SOC strategy implementation entails creating well-defined objectives and metrics. These should also smartly align with the broader security goals of an organisation.
Also Read : The Business Impact of Compliance Failures in SaaS
Implementing SOC strategy also involves identifying and tracking key performance metrics on a simultaneous note.
Note that an expert SOC should be able to promptly detect and respond to cyber threats.
It also takes into consideration a SOC’s ability to improve and strengthen an organisation’s security posture.
Defining key performance indicators (KPIs) also involves:
Maintaining compliance with industry-specific standards is critical to enforcing cybersecurity measures.
Organisations can, therefore, implement necessary security controls with the help of a structured framework when they adhere to relevant security standards.
2. Hiring Expert Personnel
SOC’s strength mirrors its staff’s capabilities and efficiency.
Thus, to derive an effective cybersecurity team, SOCs should undertake the hiring and training processes in all effectiveness.
Doing so helps retain skilled professionals without any ado.
- Look for varied skill sets, such as network security analysts, threat hunters, and incident responders instead of focusing on only one criterion for selection.
- Developing a full-fledged SOC team considers all the above.
- Threats change with time. Hence, it is imperative to provide ongoing education to your team.
- Keeping them updated on emerging trends and technologies will also help detect and mitigate threats in due time.
- Encouraging teamwork and knowledge-sharing via SOC team training aids in addressing complex threats more effectively.
3. Leveraging Advanced Technologies
We are living in an age where existing and emerging cyber threats are relentlessly thriving.
Understand that the more sophisticated these become, more are their chances to impose threats to our security controls.
These facts have made it highly crucial to integrate advanced technologies to stay ahead of cyber thefts and threats.
If you are working within a SOC environment and wish to enhance your service efficiency, you cannot go without leveraging these technologies and relevant tools.
Consider implementing AI-driven solutions for automated threat detection, pattern recognition, and predictive analytics.
Try integrating machine-learning models to identify anomalies and prevent possible attacks.
Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) platforms to centralise log data and streamline incident response workflows.
By utilising the aforementioned techniques, you can detect potential breaches in real-time.
They will also help provide visibility into endpoints and network traffic.
4. Develop Comprehensive SOC Strategic Planning
Well documented and repeatable processes result in successful SOC strategic implementation. These simultaneously facilitate security incident management.
- Create well-structured workflows for enhanced threat detection, analysis, and response. Ensure that these are clear, consistent, and accessible to your team.
- Create specific playbooks for different types of incidents, such as malware outbreaks or phishing attacks for quick and standardised responses.
Again, as an SOC, you can obtain real-time access to threat intelligence feeds.
Going on this route will extremely benefit you to stay ahead of emerging threats by effectively responding and tackling them.
SOC stands as a primary safeguard to detect and tackle potential security hazards by constantly overseeing the digital infrastructure.
Also Read : 6 Effective Team-Building Activities to Strengthen Your SOC and Incident Response Teams
5. Implementing A Unified Communication Platform
SOCs act as a primary safeguard to the digital infrastructure by detecting and aptly responding to potential security hazards.
These tasks mandate them to undertake threat intelligence sharing and cross-functional collaboration.
When properly carried out, these help them promptly mitigate potential security hazards.
These statements necessitate building a unified communication platform to connect with industry peers, vendors, and law enforcement agencies.
The result is an effective exchange of threat intelligence and best practices in incident response.
- Establish regular communication channels to collectively enhance security measures.
- Undertake training for non-SOC teams to report potential threat detection and incident escalation upon prompts.
6. Establish Real-Time Monitoring And Analysis
Successful SOC strategy implementation strictly requires round-the-clock monitoring. You can mitigate risks faster if you find threats quickly.
The below approaches will help you undertake real-time monitoring and analysis:
- Adopt a shift-based system/managed services to ensure ongoing SOC operation.
- Constantly track threat intelligence feeds to stay ahead of the latest attack vectors, vulnerabilities, and indicators of compromise (IOCs).
- Adopt behavioural analysis tools to detect unusual user actions and potential breaches.
7. Undertake Regular Assessments and Drills
Your responsibilities as a SOC organisation do not end with developing cyberdefense strategies.
Minimising threat detection and response times are equally important to prevent hacker exploitation for the organisation you serve.
Enhancing such a capability on your part requires you to undertake regular assessments and drills for your team.
All the aforementioned measures are meant to enhance preparedness to tackle possible cyber threats and attacks.
- Implement penetration testing to simulate attacks and identify vulnerabilities in your system.
- Automate tools to detect weaknesses in your network and applications.
- Leverage behavioural analysis tools to detect unusual activities or patterns that may suggest potential breach.
- Practice tabletop exercises and mock drills to refine your response strategies..
8. Maintain Compliance and Governance
SOCs should strictly adhere to regulatory compliance and relevant governance frameworks.
This is inevitable because their duties entail maintaining enhanced operational efficiency while meeting legal requirements at the same time.
- These also mandate adherence to relevant industry-specific standards such as ISO 27001, GDPR, or PCI DSS.
- Conduct regular audits for proper security policies and procedural undertakings.
- Implement NIST and COBIT frameworks to establish clear guidelines and accountability within the SOC.
6 Stages For Effective SOC Strategy Implementation
Developing an effective SOC strategy requires a structured approach.
This statement is made to convey the intense need to empower SOC by enhancing threat detection through SOC strategies.
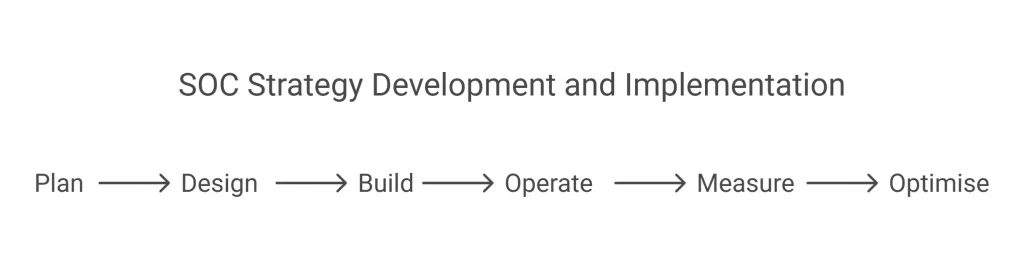
- Plan
Conduct a comprehensive gap assessment to identify existing security capabilities and deficiencies.
Planning lays the strategic roadmap for SOC strategy development and implementation.
- Design
Select the right technology, design a workflow, employ data integration, and form a well-qualified SOC team structure.
Also Read : Understanding the Unique Vulnerabilities of SaaS Products: Insights from ASP
- Build
Implement designed infrastructure and incorporate essential technologies and technological expertise to enhance operations.
This stage requires you to monitor tools, appropriately configure alert systems, and develop response playbooks.
- Operate
Manage day-to-day functions, carry out continuous monitoring, and enhance threat detection and incident response.
Requires skilled personnel to perform security analytics, forensic analysis, and threat intelligence.
- Measure
Establish metrics, such as incident response times, detection rates, and false positive rates to evaluate SOC performance.
Continue with regular assessments to help identify areas for improvement.
- Optimise
Track performance metrics and evolving threat landscapes to continuously update SOC processes and technologies.
It is an iterative process that helps determine the responsiveness of SOC to new challenges.
This stage in SOC strategy development primarily considers optimising data value for offering deep insights into data usage patterns.
What To Expect With SOC Strategy Development?
SOC strategy development when conducted systematically delivers the following outcomes:
Continuous monitoring and response on a 24/7 basis: When you seek service from SOC, you are likely to derive a fully-managed protection for your endpoints and employees. You can avail these through human expertise on a round-the-clock basis.
- Customisable security infrastructure: A system specifically designed to protect an organisation’s digital assets.
- Incident Response Planning: A set of instructions that outlines how a business should respond to a security incident.
SOC is the cornerstone of advanced threat detection and response.
Effective SOC strategy implementation is pivotal to safeguard the critical digital assets of an organisation.
An effective SOC strategy implementation aligns with business goals to enhance security measures.
Hiring SOC experts to streamline your cybersecurity measures allows you to focus on your core business operations.
Wattlecorp’s Security Operations Centre (SOC) service is one of the most proactive and vital cybersecurity solutions designed to safeguard your business from digital threats.
Located in the UAE, our VAPT experts offer round-the-clock service to protect your vital digital assets from emerging cyber threats/attacks.
Also Read : Proactive Threat Management For SaaS Business
The customised SOC strategic planning services that we offer have proven highly effective for our clients.
Improving operational security efficiency, constant surveillance, and timely reports to prevent data breaches and potential infrastructure damage are a few of the services we offer.
Our cybersecurity experts can also create a robust security infrastructure that is tailored to your unique security needs. This is regardless of whether you are seeking on-site or off-site security service.
Your search for enhancing your SOC strategy with business goals ends here! Confide in us for improving SOC efficiency through strategic planning for you.
You can directly call us or book an appointment for whatever concerns your SOC performance. Our expert cybersecurity team will promptly get back to you with the right SOC solutions.
Schedule A SOC Assessment and boost your chances of attaining everlasting security for your business.
Security Operations Center FAQs
1. What are the key elements of an effective SOC strategy?
An effective SOC strategy chiefly includes the following key elements:
• Threat intelligence
• Incident response
• Vulnerability management
• Compliance Adherence
• Continuous monitoring
• All these are meant to support early and efficient threat detection, redressals, and remediation.
2. How can a SOC strategy help reduce incident response times?
You can effectively reduce incident response times when implementing SOC strategy through the following methods:
• Effectuate alert triage processes.
• Undertake ongoing system monitoring.
• Adopt automated threat intelligence and analysis tools.
• Proactively detect and mitigate security incidents to prevent cyberattacks.
3. What metrics should we use to measure the success of our SOC strategy?
Tracking the following key metrics) will help you effectively measure your SOC strategy success rate:
• Mean Time to Detect (MTTD): Suggests how long it takes for your SOC to detect potential security threats. The lower value indicates faster detection with better proactive security.
• Mean Time to Respond (MTTR): Indicates the agility at which your SOC takes the necessary action to resolve/mitigate the threat detected.
• Incident Resolution Time: The time taken to fully resolve a security incident when detected.
• Compliance adherence: How well your SOC strategy aligns with relevant security regulations.
• False-positive rates: The percentage of alerts your security system generates, where these may not be the actual threats.







