Table of Contents
Toggle- How can Secure Source Code Review Services Protect Indian Businesses Applications from Vulnerabilities?
- What Is Secure Source Code Review And Why Is It Important For Indian Business Applications?
- The Top 5 Source Code Review Services Indian Businesses Should Consider
- Choosing The Right Secure Source Code Review Services For Indian Businesses
- The Benefits Of Utilizing The Right Secure Source Code Review Service for Indian Businesses
- Secure Source Code Review FAQs
How can Secure Source Code Review Services Protect Indian Businesses Applications from Vulnerabilities?
The consequences of leaving your source code vulnerable to cyberattacks are more than you can imagine. From data breaches to reputational damage, the losses you may incur in your business can be harsh enough to bring it to extinction. You definitely wouldn’t want it to happen to you, would you? This is why you need an added layer of protection to your software by considering utilizing secure source code review services.
With cyber threats and data breaches on the rise in India, protecting software integrity is not only important, but has become highly crucial. A secure source code review helps identify and fix vulnerabilities before attackers exploit them, ensuring stronger security from the start.
The current blog sets out to explore the top secure source code review services for Indian businesses like yours. The intent is to safeguard your applications, boost security for your sensitive data, and improve your business stability when operating in India.
What Is Secure Source Code Review And Why Is It Important For Indian Business Applications?
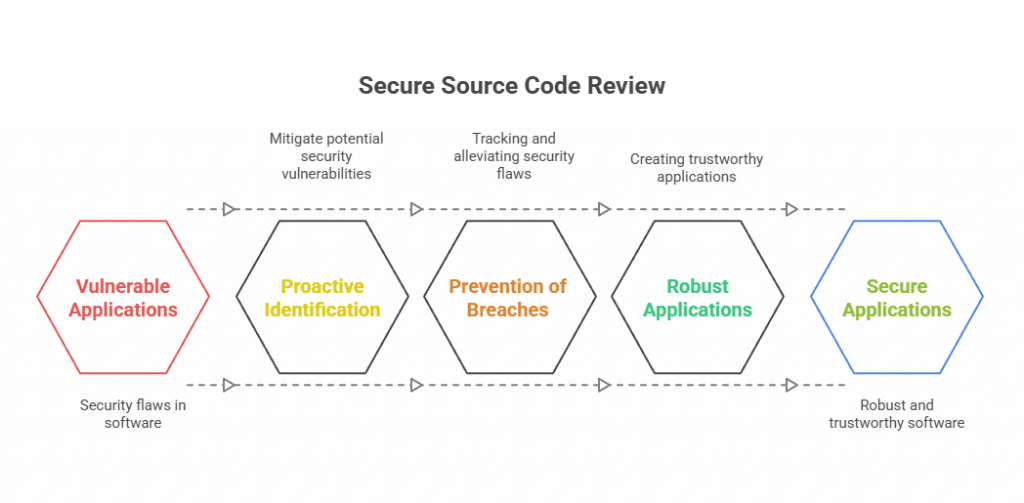
Secure source code review refers to a process to recognize security vulnerabilities within a software application’s source code.
To understand the need to conduct a Secure Source Code Review, you should note its key attributes, which include:
- A proactive identification and mitigation of potential security vulnerabilities in the software code.
- Prevention of security breaches and data leaks by tracking and alleviating security flaws in the early phase of software development.
- The creation of more robust and trustworthy applications.
With the amended CERT-In Rules in April 2022 making it mandatory to report cyber incidents every 6 hours, this simultaneously enforces synchronizing system clocks with mandatory local log storage. Failing there will lead to incurring severe penalties, such as ₹ 100,000 in fine or one-year imprisonment or both.
Most importantly, with CERT-In (Indian Computer Emergency Response Team) being empowered to issue strict cybersecurity guidelines under Section 70B of the IṮ Act 2000, these critically undermine the need for modern Indian businesses to adopt robust cybersecurity practices to secure their applications, systems, and network.
The Top 5 Source Code Review Services Indian Businesses Should Consider
As per authentic sources, secure code review purposefully serves to create a safe and trustworthy software application. Aligning with this purpose, there have emerged the following and most recommended secure source code review services:
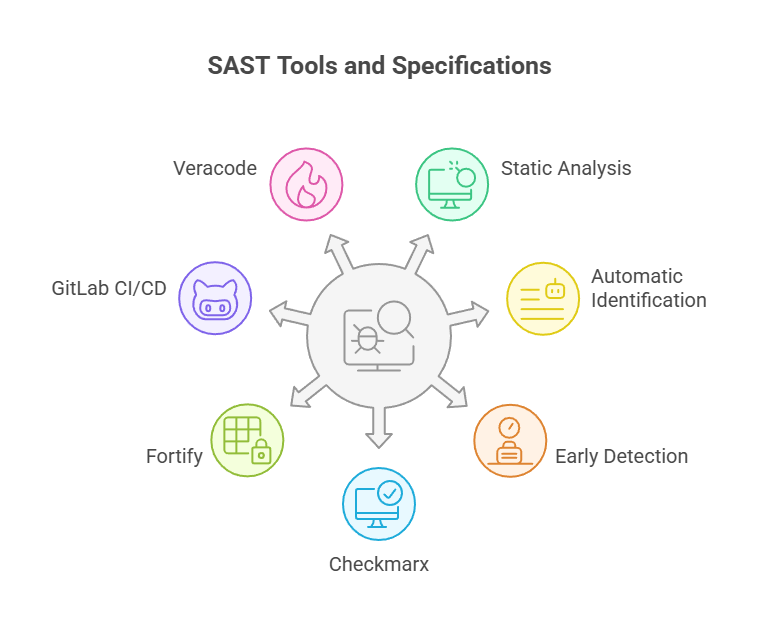
1. Static Application Security Testing (SAST)
Being a secure code review process, SAST automatically analyses application source code without actually running the application.
When it concerns analyzing code structure and syntax, SAST offers developers the insight that helps them detect and fix vulnerabilities, such as SQL Injection, buffer overflows, cross-site scripting (XSS), etc., instantly and early on in the development cycle.
SAST Specifications
- Static analysis without needing to execute the application when detecting security weaknesses within the source code.
- Automatically identifies potential security concerns when integrated into the code review process.
- Catches security issues when used early in the development lifecycle to avoid them from getting embedded in the application.
Tools Used:
- Checkmarx in SAST: Streamlines software development by improving speed and security, enhancing developer experience.
- Fortify Static Code Analyzer: Helps identify potential security flaws within the source code of an application before it’s run.
- GitLab CI/CD in SAST: Analyzes source code within the CI/CD pipeline. SAST analyzers can run in any Git tier.
- Veracode: To rapidly find and fix vulnerabilities in SAST services.
2. Manual Code Reviews
What It Involves: Trained-cum-experienced cybersecurity experts for undertaking manual code reviews by meticulously examining lines of code.
Manual Code Review Features
By analysing the code’s logic and context, manual code reviews can scan and identify potential security weaknesses that automated analytic tools cannot.
- Facilitates contextual understanding to interpret code behaviour and identify potential security weaknesses via a deep knowledge of common attack vendors and industry best practices.
- Offers customised approaches for specific project requirements when conducting secure code reviews.
- Covers critical areas, such as authentication, data handling, authorization, encryption, and input validation.
- Subtle vulnerabilities, such as insecure coding practices and improper error handling can be identified, which are not otherwise flagged by automated tools.
Tools Implemented
- Bitbucket: Enables developers to leave direct inline comments on specific lines of code within a pull request.
- GitHub’s Built-in Code-Review Feature: Utilizes pull requests’ to conduct manual code review to allow users to submit code changes to a branch to request feedback.
Also Read : The Secure Code Review Process: How It Protects Your Business from Hacks
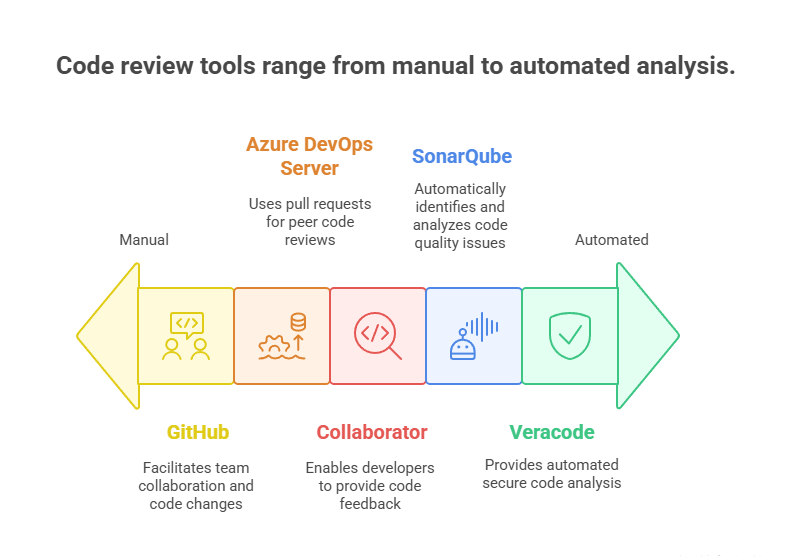
3. Peer Code Reviews
What These Do: Peer code reviews involve having someone in your team review your work to look for bugs, possible security issues, and logic errors. These summon senior team members to detect source code vulnerabilities.
Peer Code Reviews consider the following:
- Security: To determine whether potential security vulnerabilities are properly addressed.
- Coding Style: To check whether the code adheres to established code conventions.
- Efficiency: Assesses how optimally a code performs.
- Functionality: Determines if a code functions appropriately for what it is intended to perform.
- Maintainability: Ascertaining if a code can be easily modified for future applications.
- Readability: Denotes code quality, i.e., ease of understanding, maintenance, and modification.
Tools Required
- Azure DevOps Server: Utilizes the ‘pull request” feature to conduct peer code reviews.
- Collaborator for developers to examine and provide feedback on each other’s code.
- Veracode for enhancing peer code reviews by providing an automated and comprehensive secure code analysis and highlighting potential security vulnerabilities.
- SonarQube, a powerful tool enhances peer code reviews by identifying and analyzing potential code quality issues automatically.
- GitHub: Developers can propose changes to the codebase. These can be reviewed, discussed, and subsequently merged by other team members.
4. Threat Modelling
What It Is: Predominantly utilises the threat modelling methodology to analyse an application’s design and architecture. Unlike traditional source code review, Threat Modeling also strives to identify potential security vulnerabilities by considering various scenarios of possible cyber attacks.
Key Features
- A proactive approach to analyse various possibilities of attacks instead of focusing on detecting existing code vulnerabilities.
- Focus on Design and Architecture to check data flows and facilitate interactions between components to identify potential security weaknesses.
- Collaboration with Developers helps implement effective security measures by analysing and understanding identified risks.
- Structured Methodology that includes defining system boundaries, identifying assets, analysing threat vectors, and prioritising mitigation strategies.
Tools Adopted
- Imperva: A company reputed to offer a host of application security tools. These include Web Application Firewall (WAF) to help identify and mitigate potential threats within a system. Imperva serves to actively monitor and protect web applications against common vulnerabilities.
- OWASP Threat Dragon: A modeling tool that helps create threat model diagrams in the secure development lifecycle of a software application.
- ThreatModeler: An automated threat modeling tool that helps identify and mitigate threats for applications in their software development lifecycle.
Amid the growing concerns regarding national espionage, this has automatically triggered the need to scrutinize source code from a government level rather than preferring private audits. Accordingly, the Indian government has mandated the CCTV and IoT camera manufacturers (foreign or domestic) (foreign or domestic) to submit hardware, software, and source code to government labs for security testing purposes. This was made effective from April 2025.
Also Read : How Industry-Specific VAPT Solutions Secured Payment App For A Financial Enterprise
5. Code Quality Analysis Tools
What These Do: Utilise a wide variety of tools to check coding standards. Also helps identify potential issues due to style inconsistencies. Also assists in enhancing code readability and maintainability.
Key Attributes
- Can identify syntax errors, security vulnerabilities, and potential bugs, code standard violations.
- Conduct static code analysis and support multiple programming languages.
- Integrate well with development platforms, such as GitLab, GitHub, Integrated Development Environments (IDE), and CI/CD pipelines.
- Provide real-time feedback during development with detailed reports on code quality issues.
- Simplify code setup and configuration.
- Establish a user-friendly interface.
- Facilitate quick navigation across issues in code.
Tools Utilized
- Checkmarx: For its prominence in conducting code quality analysis, Checkmarx helps ensure and enhance application security.
- SonarQube: For its open-source code quality analysis property, SonarQube helps perform static code analysis that will help you identify potential bugs.
Choosing The Right Secure Source Code Review Services For Indian Businesses
It is very important that you choose the source code review service that properly matches with your secure code review needs.
This process can seem perplexing, especially due to the scores of services and tools that are available. However, we can help simplify this for you by keeping the following things in mind:
- Focusing on Security: Your primary goal should be to find security vulnerabilities within the code. You must take into consideration instances like SQL injection points, insecure data handling, cross-site scripting, etc.
- Conducting Manual and Automated Reviews: Should efficiently undertake automated and manual source code reviews to detect and fix potential vulnerabilities.
- Fetching Detailed Reports: The source code review service you choose should generate a comprehensive report that details the security weaknesses identified. It should also document the severity of the risks with recommendations for remediation.
- Compliance With Relevant Standards: Source code reviews should also cater to specific compliance requirements. OWASP (Open Web Application Security Project) offers a perfect example to this.
The National Cyber Coordination Centre (NCCC) and the National Critical Information Infrastructure Protection Centre (NCIIPC) – both operated by CERT-In, have been introduced to strengthen national cybersecurity and protect critical information infrastructure. These span across sectors, including banks, telecom, and power.
The Benefits Of Utilizing The Right Secure Source Code Review Service for Indian Businesses
The following benefits have been linked to utilizing the right secure source code review service:
- Improved Code Quality: A right secure code review service can help highlight areas for improvement, such as in code structure, maintainability, and readability.
- Reduced Risk Of Cyber Threats: Helps with proactively addressing potential security concerns. Companies offering software applications can effectively minimize risks related to data breaches and cyberattacks by utilizing the right source code review service.
- Proactive Security: Companies can duly prevent security breaches by identifying and fixing vulnerabilities in the early stage of software development.
The Master Direction on IT Governance 2023 for RBI and SEBI’s Cybersecurity & Cyber Resilience Framework (April 2024) critically mandates robust system logging, incident response, and vulnerability assessments. Equal importance has been given to align these to secure source code review practices.
Secure Source Code Reviews are vital to protect software applications for modern Indian businesses from source code vulnerabilities and resultant exploitation.
With CERT-In’s botnet-cleaning initiative under Digital India reinforcing the need to undertake secure coding at the client level, this move intends to provide Cyber Swachhta Kendra an edge in improving cybersecurity.
Also, the threat of cyberattacks on weak/poor code quality demands the need to adopt the right Source Code Review Services.
Wattlecorp Cybersecurity Labs has been reputed for offering top-notch secure code review services for its clients across the globe. The huge clientele it has received so far is a testimonial that holds it supreme among existing cybersecurity service providers in countries, including India.
As Indian cybersecurity laws are tightening with regulatory oversight becoming more intense, would you let your code go astray? Hope your answer is ‘NO’.
And, if you’re serious about meeting compliance, security enhancement, and eliminating code-level threats as an Indian-based business, would you not seek a top-ranking source code review service provider based in this country? If you’re searching for one, Wattlecorp Cybersecurity Labs is your right destination.
With our experts adept at providing source code review service by conducting deep testing source code, you derive enhanced security and compliance through eliminating code-level threats before they strike.
Secure Source Code Review FAQs
1.What are the benefits of performing a Secure Source Code Review in the Indian context?
Performing a secure source code review offers you a host of benefits. Some of these include:
• Improved code quality
• Early detection and mitigation of security vulnerabilities
• Reduced data breach risk
• Better compliance with security standards
• Increased developer knowledge sharing
• Enhanced application stability
• Improved user trust and confidence
2.How does a Secure Source Code Review process work?
The key steps to undertaking a secure source code review for Indian business applications include:
• Understanding the application for a thorough review of the application’s architecture.
• Selecting reviewers based on their experience and expertise. Also considering developers with profound knowledge of security.
• Choosing a review methodology, such as manual or automated or a combination of both to cover project complexity and availability of the tools.
3.What types of vulnerabilities are identified during a Secure Source Code Review?
When conducting a secure source code review, you may come across potential security vulnerabilities that may include:
• Cross-site scripting (XSS)
• SQL injection
• Improper input validation
• Inappropriate or insecure data handling
• Insecure cryptographic practices
• Logic errors
• Potential unauthorised access