Cyber threats are taking different forms and faces with the advancements and innovations digital transformation brings to the present world. As these threats emphasize the need to adopt the strongest cybersecurity solutions, Saudi Arabia has taken specific measures to enhance their cybersecurity controls.
The Saudi Arabia National Cybersecurity Authority (NCA) launched an improved framework version of NCA ECC (Essential Cybersecurity Controls). NCA ECC Compliance-2:2024 represents a significant leap forward in ensuring cybersecurity measures. According to Saudi Vision 2030, the country has begun investing more on digital transformation. This has increased the requirement for great cybersecurity systems in place to ensure data/infrastructure security, says the recent Dimension Market Research report.
The framework update is a cornerstone that creates a scalable and reliable approach to protect conventional IT systems and present-day technologies. This blog aims to help you understand everything that ECC-2:2024 defines, including the core domains and the implementation checklist.
To manage risks associated with cloud service providers and external vendors, ensuring the security of cloud operations and third-party vendors.
Table of Contents
ToggleNCA ECC Compliance-2:2024 Framework in Saudi Arabia – What Does it Mean?
As mandated by the NCA cybersecurity in Saudi Arabia, the NCA ECC-2 framework outlines extensive guidelines that support the protection of digital infrastructure. The revised framework also strives to ensure compliance with national cybersecurity policies.
As designed to get rid of cyber threats and their complexities, the framework helps organizations develop a reliable cybersecurity standard, incorporating cloud security, defense, and administration, among other elements.
NCA essential cybersecurity controls in Saudi Arabia: Key Goals:
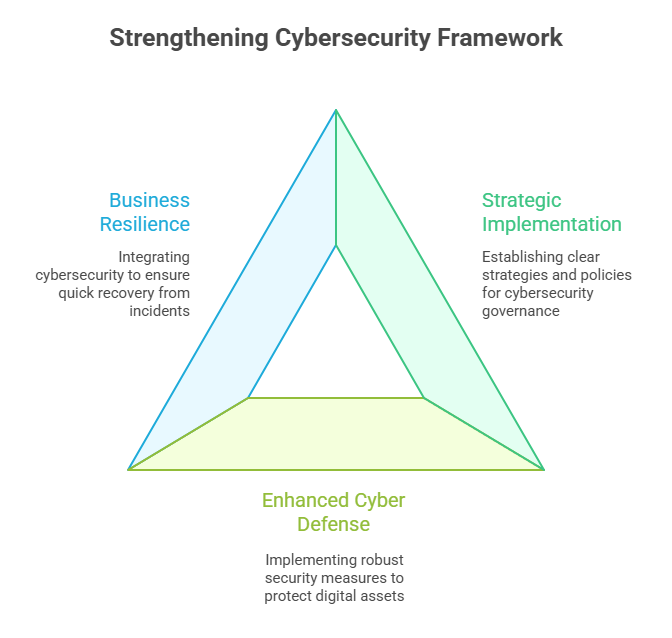
- To implement clear strategies, policies, and responsibilities to improve cybersecurity governance.
- To enhance cyber defense, implement strict asset management controls, robust network security, and effective vulnerability management.
- Foster resilience in business processes through cybersecurity integration that ensures rapid recovery from incidents.
Why Does Your Organization Require An NCA ECC Checklist?
The Saudi Arabia NCA ECC-2:2024 framework covers a detailed specification of controls and their subdomains. Let’s look at why your organization should have an NCA ECC checklist to streamline your process:
Simplified Implementation Process
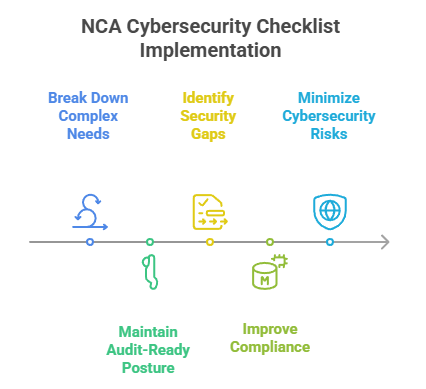
The NCA essential cybersecurity controls in Saudi Arabia checklist breaks down complex needs into subtasks, enabling you to be prepared and focused as you implement the process step by step.
Ensures Audit Preparedness
As the NCA cybersecurity framework places a strong emphasis on compliance, your organization should maintain an audit-ready security posture. The checklist helps you track the controls and find those areas for improvement to stay prepared for any audit.
Reviews Security Control Differences
With regular checklist reviews, you can easily identify the gaps and missing controls in the existing security system. It is beneficial to take the necessary steps before the vulnerabilities can become exposed.
Improves Compliance & Minimizes Cybersecurity Risks
With a structured checklist, you can ensure NCA ECC compliance and reduce your organization’s potential exposure to cyberattacks by mitigating the risk of non-compliance.
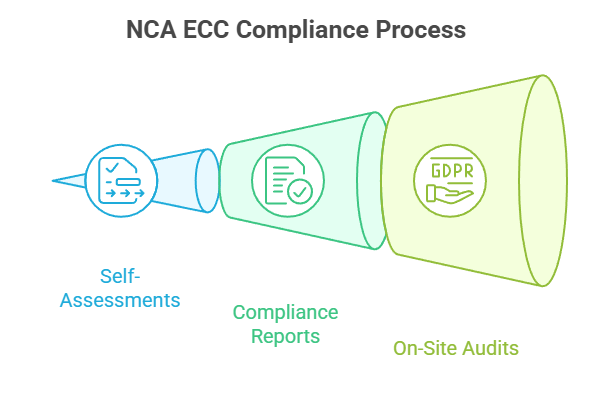
Organizations adhering to the NCA ECC regulations should:
- Execute self-assessments with the NCA ECC assessment tools
- Deliver periodic compliance reports
- Conduct on-site audits as mentioned
Non-compliance can lead to consequences, including legal actions, regulatory concerns, or restrictions on participating in authorized contracts.
Key Areas of the Saudi NCA ECC 2024 Framework
The NCA ECC regulations framework focuses on specific cybersecurity domains to deliver a great security posture. These are the domains that cover the fundamentals of cybersecurity management and security. Let’s take a look at the key areas of the NCA ECC framework:
- Cybersecurity Governance: It consists of the policies, roles, and responsibilities to stay compliant with security standards. This implements a security-rooted culture with a well-laid governance system. Effective governance enables organizations to streamline risk management and enforce their cybersecurity strategy, facilitating a proactive approach to implementing cybersecurity management.
- Cybersecurity Defense: It secures assets, IAM, cryptography, network cybersecurity, and vulnerability management. It utilizes security controls and subdomains to guard the most vulnerable systems. By adopting layered security, organizations can minimize potential attacks. With proactive controls in action, this domain helps elevate cybersecurity defense.
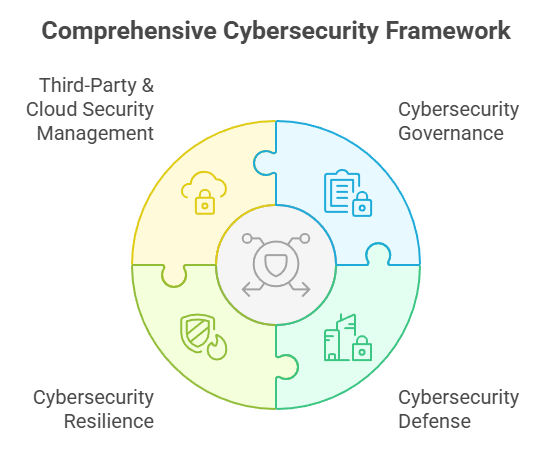
- Cybersecurity Resilience: By integrating cybersecurity resilience into regular business operations, you can ensure business continuity. This includes four primary controls that eliminate cyber threats. Organizations recover from breaches and service maintenance easier. This domain emphasizes reducing downtime and assuring operational stability.
- Third-Party & Cloud Security Management: It addresses the risks that vendors and cloud-based services encounter, thereby ensuring data security. It offers supply chain security through the use of adequate subdomains and robust cybersecurity controls. This helps organizations avoid third-party risks by adopting stringent security assessments for secure partnerships and high cloud security.
Through a structured cybersecurity process, the NCA ECC Compliance framework helps you maintain cyber resilience and compliance.
Step-By-Step Implementation Guide for NCA ECC-2
Here’s an NCC ECC implementation guide to let your organization adhere to the compliance and enhance the entire cybersecurity posture:
1. Leverage Cybersecurity Governance
A reliable administrative system contributes highly to cybersecurity. Let’s take a look at the steps to adopt:
- Develop an end-to-end cybersecurity process that clearly defines protocols, roles, and responsibilities to ensure a comprehensive approach.
- Assign specific roles and responsibilities across every organizational level.
- Ensure that the policies go hand-in-hand with both national and international standards.
- Make regular training programs that ensure security culture awareness throughout the organization.
- Establish an incident response team and the processes that manage potential security breaches.
Also Read : The Intersection of NCA ECC and Data Privacy: Ensuring Comprehensive Protection
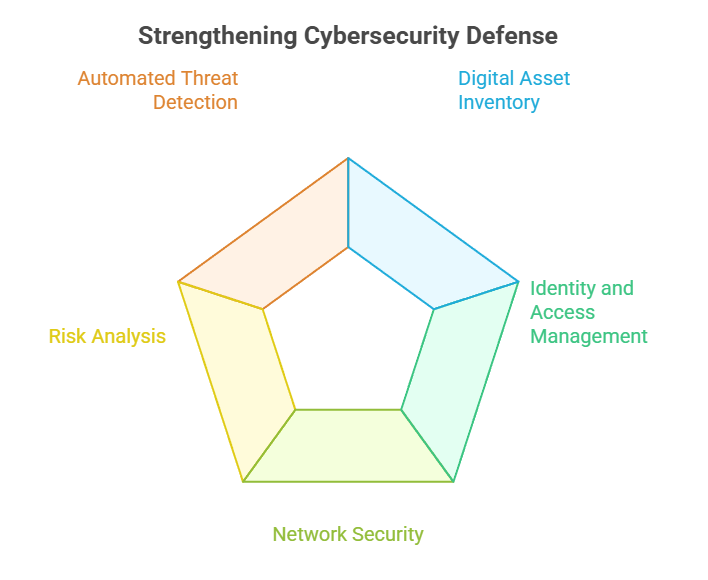
2. Enhance Your Cybersecurity Defense
Your organization’s cybersecurity defense is essential for securing digital assets and sensitive data. NCA ECC Compliance-2 employs a defense process that involves multiple layers to avoid potential cyber attacks. Steps to follow:
- Implement an inventory of digital assets and adopt an appropriate classification of sensitive data.
- Leverage Identity and Access Management (IAM) systems to manage and monitor who has access to which type of data.
- Enhance network security by implementing firewalls, IDS (Intrusion Detection Systems), and encryption measures.
- Conduct regular risk analyses to identify and mitigate potential weaknesses.
- Leverage automated tools to detect and respond to cyber threats.
3. Develop Cybersecurity Resilience
Build the capability to find and recover from cyber threats. Cybersecurity resilience enables your organization to recover from disruptions quickly. This is vital to reduce the impact on operations and services. Here are the points to consider:
- Deploy cybersecurity resilience for business continuity.
- Identify critical systems that remain operational while incidents occur and after.
- Create and test recovery strategies to reduce downtime in the attack.
- Implement regular simulations and drills that analyze the resilience strategies and their efficiency.
Also Read : The Future of NCA Compliance: Anticipating Changes and Preparing for 2025
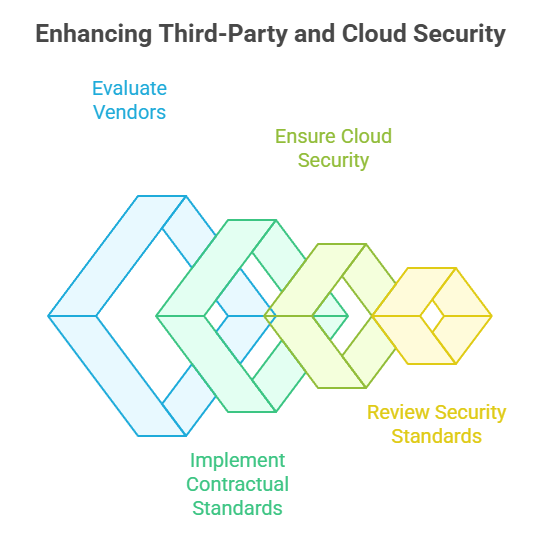
4. Optimize Third-Party & Cloud Computing Security
As businesses go for third-party and cloud computing providers, risk management related to these external partners is crucial for maintaining a secure ecosystem. For this, you should secure your business’s interactions with cloud services and third-party vendors. Here’s a process flow you can adopt for these:
- Evaluate and audit third-party vendors to ensure their compliance with the organization’s security policies.
- Implement contractual standards for third-party providers to ensure adherence to the framework.
- Ensure that cloud service providers adopt robust security measures for data monitoring and protection.
- Regularly review and update security standards related to cloud processes and third-party providers for ongoing security.
Implementation of the NCA-ECC-2 Framework doesn’t need to be overwhelming. Wattlecorp can simplify the process while ensuring your organization remains compliant with the revised Saudi NCA cybersecurity compliance framework without any hassle. Whether managing policies, adopting risk analyses, or addressing third-party cybersecurity, Wattlecorp has the capabilities to address each point of the NCA ECC-2 requirements.
By using real-time monitoring, compliance, NCA ECC audits in Saudi Arabia, and auto-evidence collection, we enable you to save time, minimize errors, and stay audit-ready. Our dedicated cybersecurity service experts are always prepared to support you and anticipate any challenges that may arise during your compliance journey. To learn more about how we can help, schedule a consultation today!
NCA ECC compliance FAQ
1. What is Saudi Arabia’s NCA ECC Audit Compliance?
The compliance ensures that the Saudi Arabia-based organizations adhere to the NCA essential cybersecurity controls as mandated by the National Cybersecurity Authority (NCA). It helps refine the digital defenses of the NCA cybersecurity framework, enabling you to achieve the mission of the National Cybersecurity Alliance.
2. How to prepare for NCA ECC compliance audits?
You can begin with the NCA ECC assessment tool, which can analyze the existing cybersecurity posture. With the help of a step-by-step guide to NCA ECC compliance audits, you can align with Saudi compliance audit standards and address all relevant ECC cybersecurity requirements. Here are the steps:
• Implement Cybersecurity Governance
• Enhance Your Cybersecurity Defense
• Develop Cybersecurity Resilience
• Optimize Third-Party & Cloud Computing Security
3. What are the possible challenges while preparing for the NCA ECC audit?
Patch management and configuration auditing are the primary challenges encountered during audit preparation. Using the NCA ECC assessment tool alongside the NCA cybersecurity framework helps you automatically detect and alleviate these concerns, enabling you to meet the ECC NCA requirements.
4. How can businesses navigate NCA ECC audit challenges?
Businesses can overcome the challenges of Saudi NCA ECC compliance audits by training their teams and utilizing the NCA ECC assessment tool for regular improvement. Collaborating with ECC cybersecurity experts also ensures adherence to the NCA essential cybersecurity controls.