Key Takeaways:
- Adherence to the NCA rules is not a choice. A company that utilizes cloud services should ensure that it meets security requirements to keep off penalties, audits, or even disruption of business.
- Multiple clouds require more control. AWS, Azure, and GCP are more flexible, yet security has been made more difficult to control. Risks may easily go unnoticed unless they are controlled.
- The majority of security problems are due to improper settings. Numerous cloud risks occur due to such basic errors as open access, weak permissions, or the lack of logs. These problems are prevented by frequent checks.
- Security is to be verified and not presumed. Presence of security controls is not sufficient. Audits and penetration testing is what you need to know whether or not your systems are really protected.
- The process of compliance is a continuous one. The NCA compliance is not a one time job. Constant monitoring, periodic review, and awareness of the staff are required in order to remain safe and non-compliant.
Table of Contents
Toggle- What Saudi Organizations Need to Know about NCA Cloud Compliance?
- AWS Setup Steps that Meet NCA Compliance Requirements
- Azure Security Fixes for Full NCA Compliance
- GCP Configurations Proven for NCA Compliance Success
- Penetration Testing Approaches for NCA Approval
- Multi-Cloud Security Rules Aligned with NCA Standards
- NCA Compliance Roadmap: Key Takeaways and Next Actions
- NCA Compliance in Multi-Cloud Environments FAQs
What Saudi Organizations Need to Know about NCA Cloud Compliance?
NCA Compliance in Multi-Cloud Environments is no longer optional for Saudi organizations using AWS, Azure, and GCP. It is a regulatory requirement with real legal and security consequences.
Saudi Arabia’s digital landscape is updating rapidly under the vision 2030. And many organizations focus on moving beyond local servers into the world of multi-cloud environments.
The National Cybersecurity Authority (NCA) assists to protect Saudi Arabia’s vital interests by setting high-security baselines.
Cloud compliance helps to meet regulatory requirements for cloud usage and adhering to local, national and international regulations.
A multi-cloud strategy using AWS, Azure, and GCP offers great flexibility, but it also creates a complex legal challenge.
For IT managers, it is no longer enough to just be secure. You must prove that you are following the law and regulations.
Even a small mistake in your settings can lead to big fines or data leaks under the Essential Cybersecurity Controls (ECC) and Cloud Cybersecurity Controls (CCC).
This guide highlights how to keep your clouds legal without the usual stress and how NCA compliance helps Saudi enterprises.
AWS Setup Steps that Meet NCA Compliance Requirements
Amazon Web Services (AWS) is a global cloud platform that provides businesses with on-demand access to computing power, database storage and content delivery.
Instead of managing physical servers, organizations in Saudi Arabia use AWS for build and scale applications securely using high-performance technology.
In order to make your AWS environment comply with the National Cybersecurity Authority (NCA) requirements, it is essential to focus on the following strategic and technical measures.
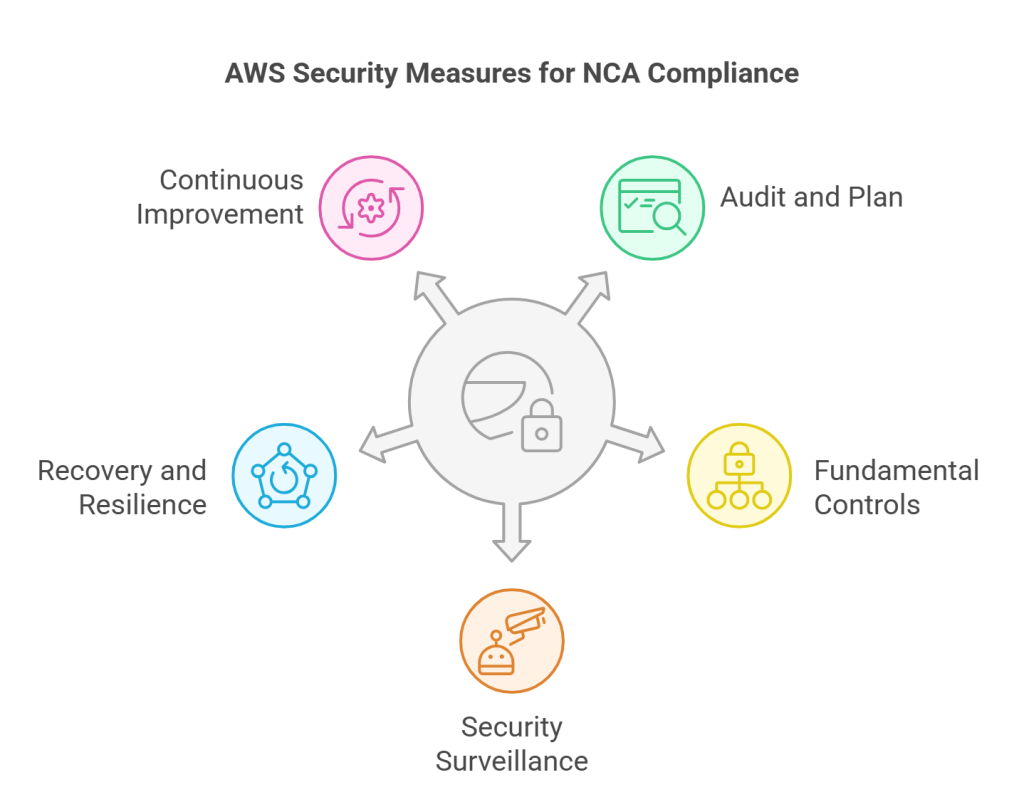
- Begin with an audit and plan: Conduct a gap analysis and compare your AWS configuration to the NCA compliance and seal any vulnerabilities. Then categorize data into groups such as Public, Internal, Confidential or Restricted in order to enforce the appropriate level of protection.
- Establish a strong base of fundamental controls: IAM can be used to implement least privilege in order to provide users with access to only the necessary resources. Secure networks using VPCs, Security Groups and NACL to add isolation to workloads and prevent threats.
- Improve security surveillance and activities: CloudTrail and CloudWatch can be used to provide real-time logs and automatic threat detection. Establish an effective incident response plan to identify and manage breaches within a short period. Conduct audit settings quarterly in relation to CIS AWS Foundations Benchmark.
Also Read : A 2025 Guide To Understanding the Essential Cybersecurity Controls (ECC) of NCA in Saudi Arabia
- Ensure recovery and resilience of business: Distribute resources to different Availability Zones to prevent unavailability. Install encrypted and automated backups in order to have quick data recovery.
- Continuous Improvement: Conduct audits and penetration tests in order to test your defenses. Conduct regular training of train staff on NCA requirements and obtaining cloud management. Keep up with new NCA regulations to keep in compliance.
Whether you are an organization, you may deploy these key AWS security controls and create a resilient infrastructure that meets the NCA requirements while safeguarding important Saudi information.
Azure Security Fixes for Full NCA Compliance
An Azure configuration review is a thorough evaluation of your organization’s Azure and Office 365 environments to uncover security gaps, misconfigurations, and deviations from industry best practices.
The insights gained help strengthen your cloud infrastructure, improve compliance posture, and minimize the risk of data breaches or operational disruptions.
Azure review considers industry best practices and includes detailed reviews of Azure’s security controls like IAM, virtual machine security policies, networking security groups, SQL services on SQL servers or databases, and secure storage account configuration.
Also Read : The Future of NCA Compliance: Anticipating Changes and Preparing for 2025
The comprehensive assessment of your Azure environment helps you to realize the lack of security and best practices. But the business impacts of those vulnerabilities are being exploited.
Providing detailed reports of findings enable you to implement the best practices, plug security gaps in your Azure environment, and mitigate risk of security breaches.
A smart threat mitigation will help you stay compliant with regulations, uphold your reputation and save costs.
GCP Configurations Proven for NCA Compliance Success
A GCP configuration review assists you in identifying security vulnerabilities, misplaced configuration, and threats in the functionality of your business relating to the usage of Google Cloud.
In Wattlecorp, the team will review your GCP configuration and provide understandable actions to minimize risks, secure data and applications, and enhance security.
Verifies the manner in which your resources on Google Cloud are configured and accessed.
Establish remedies on weak spots before they result in security incidents.
Assists in a more robust security stance and capabilities in enhanced cloud utilization.
What is the checklist in a GCP configuration review?

- IAM: Review users and access permission and delete access that is not necessary.
- Networking: Verify VPCs, firewalls and routing to prevent undesired access.
- Logging and monitoring: Ensure that the key events are logged and alerts are installed.
- Storage: Check access, sharing and encryption of sensitive information in buckets.
- Virtual machines and databases: Evaluate VMs, Cloud SQL and BigQuery on secure environments and exposure.
The advantages of a GCP configuration review.
- Secures valuable information and important applications.
- Identify and correct configuration errors which introduce risk.
- Conserves time to allow teams to concentrate on the actual business.
- Helps to adhere to the security and regulatory requirements.
- Increases customer and stakeholder confidence in enhanced cloud security.
Penetration Testing Approaches for NCA Approval
Configurations are just promises. Penetration testing is the proof.
The National Cybersecurity Authority (NCA) in Saudi Arabia requires organizations to go beyond basic automated scans. Wattlecorp’s professional penetration testing uses multiple layers to validate your cloud security for NCA compliance.

- Cloud Logic Testing: Test if any attackers can exploit IAM roles to gain unauthorized elevated privileges in your cloud environment.
- Cross-Cloud Vulnerabilities: Ensure a breach in your Azure setup doesn’t create a backdoor to your AWS data or other cloud services.
- API Security Testing: Examine connections between cloud services, which are often the weakest link in multi-cloud architectures.
Implementing a NCA-approved penetration testing not only strengthens your multi-cloud defenses but also it helps Saudi enterprises to meet regulatory requirements with confidence.
Multi-Cloud Security Rules Aligned with NCA Standards
Three Core Rules for NCA Compliance in Multi-Cloud Environments.
Keeping your multi-cloud setup compliant with Saudi Arabia’s National Cybersecurity Authority (NCA) doesn’t have to be complicated.
Following some security rules helps to make compliance clear and manageable.
- Zero Trust – Assume Every Connection is a Threat
Zero trust assures that you never fully trust any connection, not even from the inside your network. Every user, device, and service must be secured before accessing resources. And this strong security approach helps to protect against insider threats and compromised accounts.
- Data Minimization by Storing Only What You Need
Ensure to store only the sensitive information that is essential for your business operations. because, the less data means fewer risks if anything goes wrong.
- Continuous Monitoring – One Dashboard for All Clouds
Use a single dashboard to watch your AWS, Azure, and Google Cloud environments simultaneously. Catch issues early and respond faster when threats appear.

Why even strong configurations need testing?
Your cloud configurations might look perfect on paper. But hidden flaws can still exist.
Wattlecorp’s penetration testing service in Saudi Arabia puts your multi-cloud environment through real-world attack scenarios. Not just scan for finding problems, it is focused to simulate actual threats and show exactly how attackers could break in.
Our detailed reports map directly to NCA requirements.
More importantly, we provide clear, actionable steps to fix every issue. And the result is a battle-tested cloud environment ready for your next NCA audit with zero stress.
Ready to strengthen your multi-cloud security? Contact Wattlecorp for NCA-approved penetration testing tailored for Saudi enterprises.
NCA Compliance Roadmap: Key Takeaways and Next Actions
The journey to achieving NCA Compliance in Multi-Cloud Environments is not a one-and-done task. It requires a mindset of constant improvement.
For that you need to identify and know exactly where your sensitive data sits across AWS, Azure and GCP.
At Wattlecorp, we bridge the gap by using the configuration steps mentioned above to fix immediate security holes.
Moreover, ensure to validate our defenses by connecting with experts to perform an NCA compliance, gap analysis and a deep-dive pen test.
Each offers various architectural principles and approaches to data sovereignty, degrees of automation and depth of managed services.
These differences directly influence how the solutions are designed, deployed and operated.
There is no universal best cloud provider for regulated industries because each has its own distinct strengths.
Talk to Wattlecorp’s NCA experts or schedule your penetration testing service in Saudi to ensure your multi-cloud infrastructure is fully compliant.
NCA Compliance in Multi-Cloud Environments FAQs
1.What is NCA Compliance Saudi Arabia?
The NCA compliance is a legal obligation that the government and non-government organizations in the Kingdom should adhere to particular cybersecurity standards such as the ECC and CCC. These regulations are aimed at safeguarding national security and data confidentiality. There is a risk of legal punishments in case of failure to comply and exposes the business to cyberattacks.
2.How do I achieve NCA Compliance in AWS, Azure and GCP?
To ensure compliance on these platforms, it is a combination of appropriate configuration and local hosting. Each cloud must be configured according to the NCA regulations concerning encryption and logging without placing all the sensitive information on the data centers in Saudi Arabia. Lastly, these controls should be checked by periodic audits and penetration tests.
3.What are the best security practices for multi-cloud environments?
An integrated strategy is the best one. You are supposed to centralize all your clouds by means of a Centralized Identity Provider and should have a Zero Trust architecture. It is also important to employ automated tools which will bring to your attention the moment the configuration has been deviated off your defined security baseline.
4.How does penetration testing support NCA Compliance?
NCA demands that your security controls be technically verified. Penetration testing is a simulation of an attack in the real-world. It demonstrates to auditors that you do not have your firewalls, encryption, and access controls set on paper, but they are in fact operational in preventing a professional hacker.
5.What is the importance of NCA Compliance to Saudi Arabian businesses?
Business continuity is vital besides being on the right side of the law. NCA compliance is now becoming evident in many government contracts. It develops a reputation of being trusted by your clients and makes sure that a cyber incident would not bring your business to a halt and reveal sensitive data of customers.