Achieving global security standards with Compliance, Security assessment, and cutting-edge data privacy tools
How we became a trusted partner by providing multi-year support for end-to-end data security and global certification standards for a vendor in the GCC.
Project Overview
- Industry:
Tourism and Hospitality
- Company Size:
500+
- Challenge:
Compliance readiness
- Solution:
Upgrade to global security standards
Our top challenges and Solutions
The challenges were complex but well-defined, from creating a user access matrix to market readiness with global compliance standards.
Key Challenges
- Establish the need for higher compliance standards
- Strengthen the existing weak network access control
- Analyse and review internal data handling systems
- Identify key vulnerabilities and risk assessment
- Achieve data privacy standards in multiple countries
- Strengthen security via global partnership management
- Ensure information security and Data privacy expectations
Business Impact
- Lack of trust without ISMS certification
- Inability to meet client security standards
- Open threats cause repetitive network failures
- No security policies to assess threat & meet SLA timelines
- Risk of leakage due to absence of Data Flow Diagram
- Outage/data unavailability risks with no BCP
Our Solutions
- Migrate frameworks from local to global
- Map PDPL with GDPR for future-readiness
- Timely vulnerability assessment and regular updates
- Align ISMS with global TPA requirements
- Continuous improvement of ISMS & Data privacy
Delivered Results
- ISMS certification for improved business opportunities
- Comprehensive vendor assessment questionnaire
- Continuous VAPT monitoring & instant threat response
- Enhanced data privacy compliance via GDPR–PDPL alignment
- Streamlined TPA responses and global compliance readiness.
- Backup updates and recovery systems, ensuring business continuity
Technical Implementation Roadmap
Assessment & Planning
- Vulnerability assessment and penetration testing
- Risk analysis and threat modeling
- Compliance review and Infrastructure audit
- Security policy and procedure assessment
- Internal audits
Solution Design
- Multi-factor authentication
- Improved password complexity
- Incidence response team placement
- Network security awareness programs
Implementation
- Network architecture diagram for network segmentation
- End-point detection and response
- User awareness training on the latest trends
- Business continuity plan (BCP) testing
Monitoring & Optimization
- Yearly VAPT
- Timely risk assessment and scans
- Antimalware and security policies
- Timely review of best practices
Technical Implementation Roadmap
Assessment & Planning
- Vulnerability assessment and penetration testing
- Risk analysis and threat modeling
- Compliance review and Infrastructure audit
- Security policy and procedure assessment
- Internal audits
- Project Initiation Discussion
- Business Process Walkthrough
- Business understanding and Scope confirmation
Solution Design
- Multi-factor authentication
- Improved password complexity
- Incidence response team placement
- Network security awareness programs
Implementation
- Network architecture diagram for network segmentation
- End-point detection and response
- User awareness training on the latest trends
- Business continuity plan (BCP) testing
Monitoring & Optimization
- Yearly VAPT
- Timely risk assessment and scans
- Antimalware and security policies
- Timely review of best practices
Technical Deep Dive
We left no tech unchecked to boost the overall security detail and ensure the future-readiness of our solution.
Technology Stack & Tools
for Storage | Eramba for Policy Management
Security Infrastructure
- Network access control
- Crowdstrike Falcon endpoint protection
- Digital asset management with Filespin
- Azure multi-layered security
Compliance & Governance
- Assigned ownership of data, system, and risks
- Custom GRC dashboard implementation
- Regular assessments for optimal system security
- Regulatory requirement mapping to internal controls
Monitoring & Analytics
- Regular security assessments
- Rigorous process optimization
- Awareness training programs
- Dedicated security personnel
- Implementation Methodology
Security Framework
- Integrated relevant frameworks from local to global
- Continuous security monitoring
- Vulnerability prioritization based on risk
Best Practices Applied
- PDCA cycle for all-around security
- Security by design philosophy
- Defense in depth strategy
Security Performance Metrics
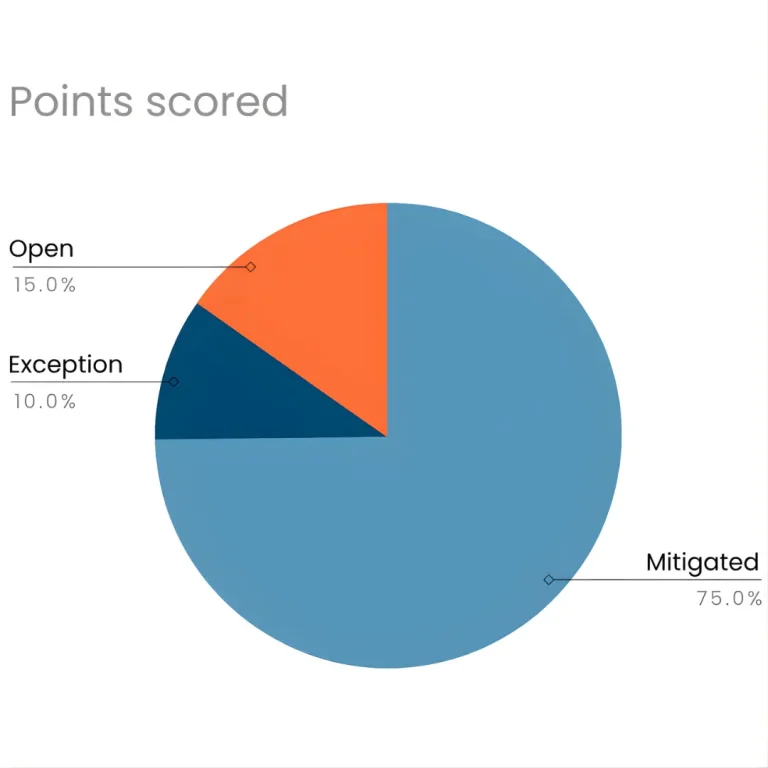
- 70-75% mitigated, 5-10% exception, 15% Open
- Rating: 6/10 (Moderate Risk)
Compliance Scores
GDPR Compliance 90%
ISO 27001 95%

Security Performance Metrics
- Pie chart
- 70-75% mitigated, 5-10% exception, 15% Open
Compliance Scores
GDPR Compliance 90%
ISO 27001 95%
- Rating: 6/10 (Moderate Risk)
Key Business Outcomes
For Startup owners
For CISOs & Project Managers
- Improved reputation for better deals
- Heightened scope for market expansion
- Improved trust through compliance
- Operational risk reduction by 75%
- Balanced business needs with security
- Automated incident response workflows
- Reduced threat response time by 70%
- Multi-framework compliance achievement
Key Business Outcomes
For Enterprise Customers
For CISOs & Project Managers
- Dynamic productivity improvements by 30%
- Increased customer trust and retention
- Achieved industry-best security standards
- Heightened risk reduction by 80%
- Implemented industry-best compliance standards
- Enabled multi-framework compliance and licensing
- Comprehensive threat detection and monitoring
- Higher insight generation with minimal user effort
Ready to shield your business with the right security?
Let’s discuss a strategy to safeguard your organization from threats of all intensities and ensure end-to-end security for all your business needs, 24/7.
Ready to shield your business with the right security?
Let’s discuss a strategy to safeguard your organization from threats of all intensities and ensure end-to-end security for all your business needs, 24/7.