Compliance Readiness and Security Assessment for a
leading digital bank
How we implemented industry-best compliance standards and data security measures for a fintech bank with customers across the GCC in under a month.
Project Overview
- Industry:
Fintech
- Company Size:
120
- Challenge:
Urgent need to address security issues, Industry standard
- Solution:
Vulnerability assessment and Compliance
Our Challenge and Solution
Digital banks are often the primary target for cyber attacks and come with a long list of compliance standards. Our effort was to analyze, design, and employ targeted efforts to minimize risks, future-proof from threats, and make the application compliance-ready to operate in multiple countries.
Key Challenges
- Lack of compliance and increasing data privacy threats limited their scalability
- External penetration risks increased network data leakage threat
- Chances of reduced data integrity in M365
- Ineffective VPN standards with the potential for external attacks
- Vulnerable cloud environments reduced the overall security score
Business Impact before us
- Sensitive client details were vulnerable to cyber threats
- Possibility of substantial financial losses
- Potential for data leaks that hinder progress
- Lack of security compliance impacted licensing
- Lack of security frameworks to identify threats
- Unorganized data compromised access control
Our Solutions
- Internal network checklist and VAPT to review overall security
- Network segmentation review to ensure business properties are properly isolated
- M365 configuration review to evaluate authentication and data loss prevention
- VPN configuration review via universal standards-compliant security audits
- Conducted Security Operations Centre (SOC) maturity assessment
Delivered Data Privacy & SOC Detection Improvement
- Ensured UAE PDPL, GDPR compliance
- Performed data privacy risk & impact assessment
- Implemented an adequate threat mitigation plan
- Provided risk mitigation reports
- Compliance certificates that improve trust
- Yearly assessment reports
Technical Implementation Roadmap
Scoping and Planning
2 week
- Define the scope and boundaries
- Understand key business functions
- Challenge identification
- Project Initiation Discussion
- Business Process Walkthrough
- Business understanding and Scope confirmation
Initial Assessment
1 week
- Review business operations
- Review core operations and data flow
- Assessments review meeting
- Review core operations and data flow
Technical security testing
4 week
- VAPT
- Provide executive summary report
- Initial assessment report and action plan
- Revalidation and remediation
Process design
Ongoing
- Development of policies and procedures
- Awareness training
- Stakeholder review and feedback
- Configuration assistance
- Implementation support
- Report preparation
Compliance Audit
Ongoing
- Compliance audit planning
- Compliance audit execution
- Preparation of corrective action report
- Gap closure
Scoping and Planning
2 week
- Define the scope and boundaries
- Understand key business functions
- Challenge identification
- Project Initiation Discussion
- Business Process Walkthrough
- Business understanding and Scope confirmation
Initial Assessment
1 week
- Review business operations
- Review core operations and data flow
- Assessments review meeting
- Review core operations and data flow
Technical security testing
4 week
- VAPT
- Provide executive summary report
- Initial assessment report and action plan
- Revalidation and remediation
Process design
Ongoing
- Development of policies and procedures
- Awareness training
- Stakeholder review and feedback
- Configuration assistance
- Implementation support
- Report preparation
Compliance Audit
Ongoing
- Compliance audit planning
- Compliance audit execution
- Preparation of corrective action report
- Gap closure
- Implementation Methodology
Best Practices Applied
- Regular security assessments
- Industry best VAPT and Data Privacy standards
- Security by design philosophy
- Principle of least privilege
- Defence in depth strategy
Security Framework
- MITRE ATT&CK Framework
- NIST Cybersecurity Framework
- OSSTMM Security Testing Framework
- CIS Benchmarks & Critical Security Controls
- OWASP-aligned Vulnerability Detection Framework
Key Findings Overview
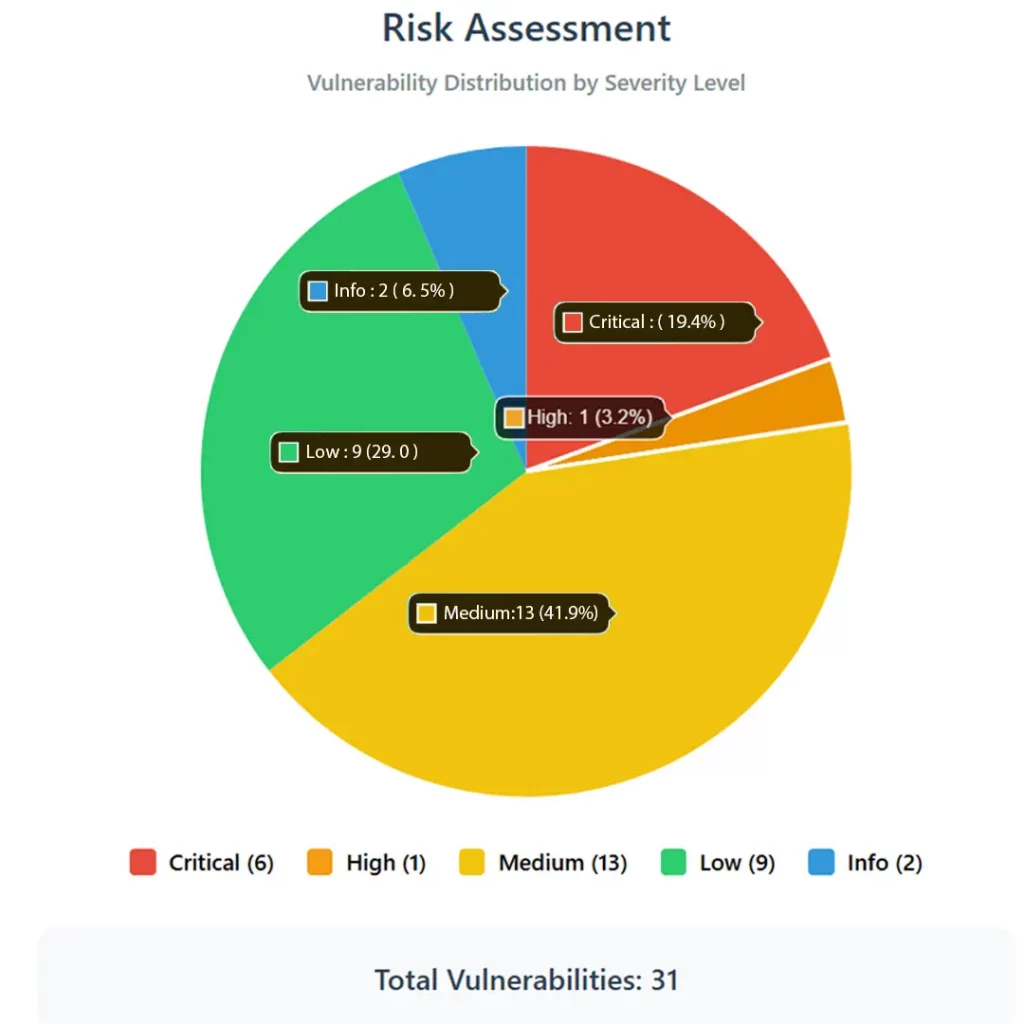
- We identified 31 total risks across all assets.
- OVERALL ASSESSMENT SECURITY POSTURE
- Rating: 6/10 (Moderate Risk)
- Exposed VMware ESXi interface and IIS version disclosure pose low information exposure risks.
- No significant vulnerabilities identified, demonstrating a strong external security posture.
- Weak Wi-Fi passphrases are mitigated by MAC whitelisting, resulting in low risk.
- The web application has critical authentication flaws, including CAPTCHA bypass, which allow for account compromise and potential abuse.
- The website shows minor to moderate security weaknesses from exposed logs to missing hardening measures
Key Business Outcomes
For Enterprise Customers
For CISOs & Project Managers
- Dynamic productivity improvements by 30%
- Increased customer trust and retention
- Achieved industry-best security standards
- Heightened risk reduction by 80%
- Implemented industry-best compliance standards
- Enabled multi-framework compliance and licensing
- Comprehensive threat detection and monitoring
- Higher insight generation with minimal user effort
Key Business Outcomes
For Enterprise Customers
For CISOs & Project Managers
- Dynamic productivity improvements by 30%
- Increased customer trust and retention
- Achieved industry-best security standards
- Heightened risk reduction by 80%
- Implemented industry-best compliance standards
- Enabled multi-framework compliance and licensing
- Comprehensive threat detection and monitoring
- Higher insight generation with minimal user effort
Ready to shield your business with the right security?
Let’s discuss a strategy to safeguard your organization from threats of all intensities and ensure end-to-end security for all your business needs, 24/7.
Ready to shield your business with the right security?
Let’s discuss a strategy to safeguard your organization from threats of all intensities and ensure end-to-end security for all your business needs, 24/7.