Client Overview
This wasn’t their first time thinking about security. But now, it felt urgent.
A fast-growing SaaS company reached out. Their platform handled a lot of sensitive customer data. Things were scaling quickly. More users. More features. More pressure. They knew they needed to tighten things up.
Not because something had gone wrong. But because if it ever did, it would cost them trust—and once that’s gone, it doesn’t come back easily.
Challenges
Their codebase had grown fast—really fast. New features, new tools, and a mash-up of frameworks and plugins stitched together. It worked. But no one had taken a hard look at it with a security lens.
They didn’t have in-house security expertise. Just talented devs shipping product at speed. But without the right guardrails, even great code can leave the door open.
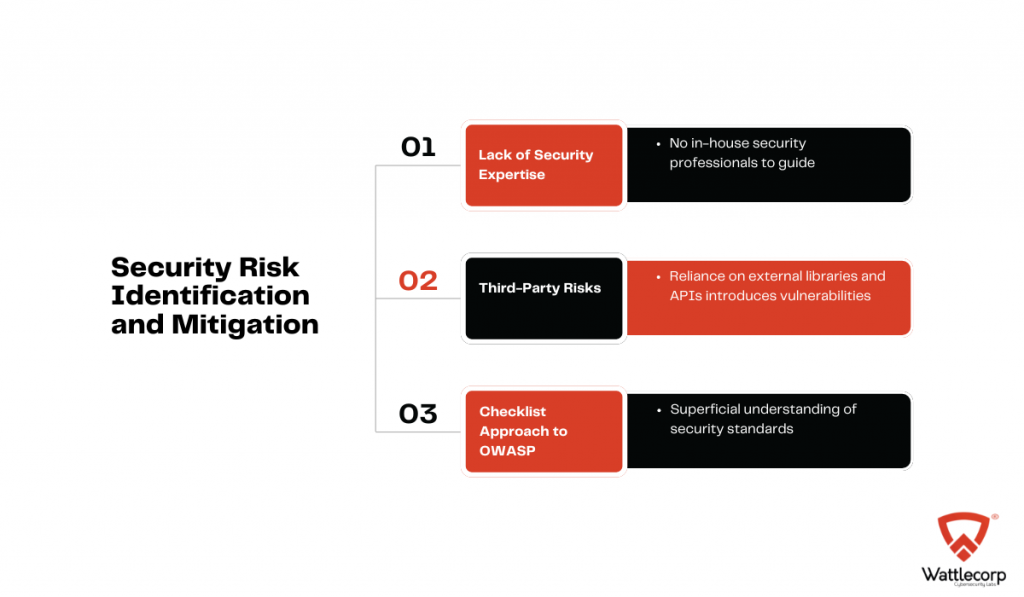
They were using third-party libraries and APIs—like everyone does. The problem is, those come with risks baked in.
And they were trying to keep up with OWASP Top 10, but honestly, most of it felt like a checklist, not something they deeply understood.
So they came to us. Not just for a fix—but for clarity.
How We Secured the Application?
We didn’t start with tools. We started with questions.
Where were the riskiest parts of the app? Who was using what? What could break, and how badly?
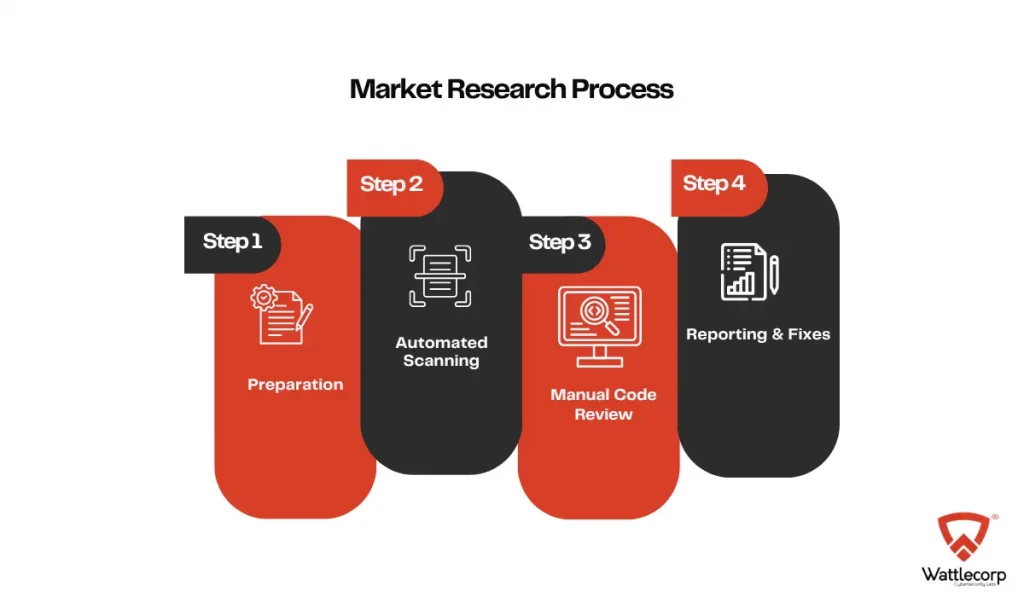
Step 1: Preparation
We mapped out the high-risk areas. Focused our efforts. Built a checklist, but not the kind you skim through. This one lined up with the standards—OWASP Top 10 and a few others they needed for compliance.
Step 2: Automated Scanning
Yes, we used scanners. The best ones. They caught the usual stuff—old packages, common issues, the kind of flaws that sit quietly until someone decides to exploit them.
We sorted the noise from the real threats. Not every warning is worth your time.
Step 3: Manual Code Review
Now came the part that tools can’t do. We went in—line by line.
Checked how they handled login sessions. Looked at how the APIs were stitched together. Some of the most serious issues weren’t flagged by any scanner. But our team spotted them. That’s where experience matters.
Step 4: Reporting & Fixes
No jargon. No 40-page PDF full of “maybes.”
We gave them a report that made sense—what’s broken, why it matters, how to fix it. Then we got on calls with their devs. Sat with them, walked through each issue, and made sure nothing got lost in translation.
We didn’t just point at the problem. We helped fix it. Then we tested again.
And yes, we left them with clear guidance so they wouldn’t make the same mistakes twice.
Key Security Issues & Fixes
There was one standout: a Prototype Pollution vulnerability buried in their JavaScript. Subtle. Easy to miss. But dangerous. It could’ve let attackers twist how the app behaved and quietly leak data.
We replaced the vulnerable parts with Map structures, added strict validation, and closed the door on that risk for good.
We also cleaned up logs that were revealing too much. Tightened how target=”_blank” links were used (yep, even that can be a threat). And we hardened their API security so only the right people got in.
The Result
By the end, the app didn’t just feel safer—it was.
They caught and fixed things before attackers could even try.
They met the standards they needed to. No ticking boxes. Real alignment.
The devs now knew what to look for—and what to avoid.
Their code was cleaner, their team was smarter, and their product was stronger.
Why Secure Code Review Matters?
Most founders think of security as something you patch on top. But it’s not.
It needs to live inside your process—just like testing, just like performance.
The earlier you build it in, the less you’ll lose later.
The right mix of automation and expert review gives you eyes where scanners can’t see.
And when your team understands the “why,” not just the “how,” they stop repeating the same mistakes.
This company didn’t just fix vulnerabilities. They learned how to spot them before they ever made it to production.
That’s the real win.
